Following up on our earlier blog on the topic of Password Hacking, here is a deeper technical dive into the process of Password Hashing, and how it helps to keep your passwords secure.
When you create a password for new accounts on an ecommerce site, typically what gets saved is not your actual abcd letter password but a hash value calculation / representation of that password.
A hash is a one-way calculation / conversion of a word / character set to a long string of random values that cannot be reversed to produce the original word. There is no way to calculate what the original word was from the hash which makes them quite secure. To hash your passwords character set, a binary conversion of that character set is first done, and then that binary is run through a hashing algorithm.
An algorithm is just a fancy word for a complex mathematical calculation and there are a number of hash algorithms available such as SHA-512, MD-5, bcrypt, and PBKDF2. For each type of algorithm, all hash values are the same length. Algorithms differ in in complexity. More on why thats important later.
Heres the process to hash the word: password
The word password is first converted into binary code: 01110000 01100001 01110011 01110011 01110111 01101111 01110010 01100100 00001010
Running the password binary through the SHA-512 algorithm results in this hash code / value: 109f3bbbc244eb82441917ed06d618b9008dd09b3befd1b5e07394c706a8bb980b1d7785e5976ec049b46df5f1326af5a2ea6d103fd07c95385ffab0cacbc86
If you created a new account on a website and they were using SHA-512, the 128 character hash value above is what would be stored in place of your password. Then each time you logged into the website, it hashes your password and compares it to your original / stored hash.
If they are the same, you are logged in. If they are different, you must have put in the wrong password and you are denied. In this way, if the website gets compromised, all the attacker gets is a list of hash values instead of passwords. And since hashes cannot be backward calculated to the original password, the hacker cant gain access to your account.
Temporary Relief
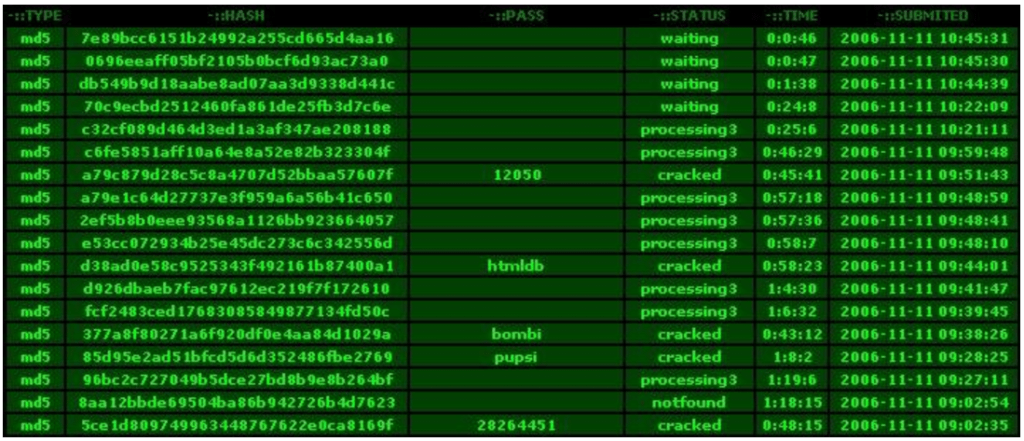
Although it might appear that your password is now safe because of all of that conversion and hashing, we now have to talk about rainbow tables.
Theoretically, hackers can calculate the hash value for any word and save that list as a precomputed table. So if a potential attacker hashed all common passwords (easily sourced from internet forums), he would eventually have a list of hashes and the words used to create the hash.
This is the basis of the rainbow table and it might look something like this:
Naturally, not only can hackers refer to commonly known passwords to create the table, but passwords can also be brute forced, trying all combinations of numbers, letters, and characters. That is where the complexity of the algorithm comes into play.
The more complex the algorithm is, the longer it will take to hash each possible password. This is a very good thing in that you’ll have more time to change your password in the event of a breach.
The length of your password is also a big factor in the amount of time it takes reach the correct answer. If you have a long password (12+ characters), the hash value is essentially useless due to the amount of time it would take to hash all possible combinations of 12 characters for the rainbow table.
According to Georgia Tech research scientists, sophisticated hackers are able to brute force passwords at the rate of 1 trillion password combinations per second. At that speed, an 11-character password (and all it’s possible combinations) would take 180 years to crack. But by adding just one more digit, to 12-characters, the time required now leaps to over 17,000 years!
As such, while the hashing process contributes to the overall security of your account, a persistent take-away is to avoid using common or short passwords!