Todays security blog puts forth a litany of eye-glazing Cybersecurity terms like Macro-Laden, OpenDNS, Social Engineering, and its ilk. But stick around till the end, as well detail how hackers continue to exploit both system and human vulnerabilities, and point out a few security layers that exist to foil their attempts.
We all realize that spam email continues unabated, and perhaps believe were getting pretty good at sending it off to our spam bucket or that automated filters are taking care of it for us. By now, most internet users have got to know not to click links or download files sent from unknown senders, right?
The unfortunate reality is that business email compromise continues to be very lucrative for the bad guys, with hackers collecting $5.3B WW between Oct 2013-Dec 2016, according to the most recent data from the FBIs Internet Crime Complaint Center (IC3). Of that massive global amount, a good chunk ($1.6B) was siphoned from US businesses, with the majority of fraudulent funds wired overseas to banks in China and Hong Kong.
How do these criminals target companies to defraud them (and acquire) these ill-gotten funds? Here are the five most common scenarios per the IC3.
- Businesses that work with foreign suppliers
- Imposters posing as an executive requesting a wire transfer
- Requests for funds transfers sent via a compromised email account
- Imposters posing as legal professionals needing a wire transfer on a time crunch
- Fraudsters using compromised emails to request W-2 forms or other confidential personal information
There are crooked methods aplenty (phishing, ransomware, etc) for hackers to gain access to confidential information or your funds, but this blog will specifically address the threat posed by Macro-Laden malicious documents.
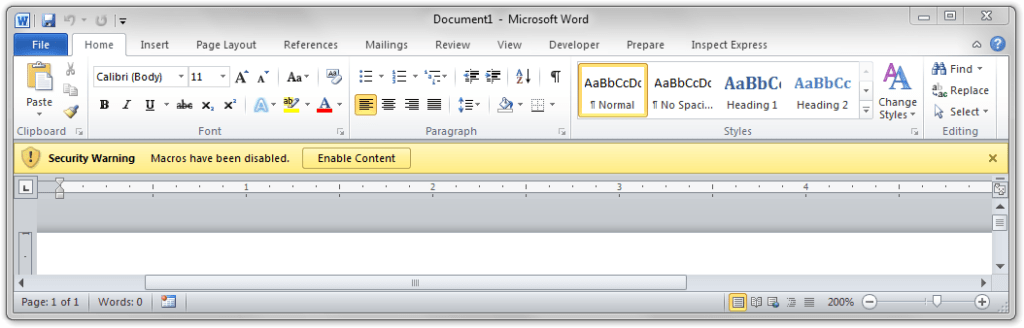
Just as we are inured to the scads of spam in our inbox on a daily basis, were also used to seeing the familiar Security Warning declared by Microsoft Word or Excel when a document youre trying to open contains macros.
As you might agree, Office macros are an everyday productivity tool, saving us time on repetitive tasks by bundling steps, and running the task with a single click or keystroke. That said, its been known for years now that these macros can contain malicious code that do harmful things to your computer or network. They can unleash viruses or malware or try to retrieve malicious files from a website.
(To be clear, if you receive Office docs from a known sender that do contain macros you likely have nothing to worry about — assuming the senders email hasnt been spoofed, but thats another story!)
Microsoft implemented macro security level features way back in Office 2003, and with Office 2013 all macros are disabled by default. Users are alerted that the macro wasnt allowed to run, requiring us to deliberately enable the macro via a simple click. How can hackers compel you into performing this act?
This is where Social Engineering comes in.
Social Engineering is the manipulation of people into performing actions that they shouldnt do. Examples include clicking on unsafe links, visiting malicious websites, fooling you into thinking youve been emailing with a client or executive to wire funds to a hackers foreign bank, or disclosing confidential information such as your social security #.
Returning to those bad macros, to get around the security warnings, hackers have whipped up creative means to compel you to click on that Enable Content button, thereby opening up their Pandoras box.
In the pace of a busy office environment, receiving emails left and right, collaborating with co-workers… if you saw these official looking instructions, would you really pause to consider whether these are legitimate?
Every one of these are fake notices. Would your first instinct be to wonder whether these are actually security threats or immediately click through because they appear legit?
In this day and age of pervasive threats and increasingly sophisticated bad actors, we absolutely must treat every access instruction or request as a potential breach vector. Many companies today have implemented security training for employees, with varying incentives or punitive measures to get you to think before you click, or to verify identity prior to wiring off funds.
Numerous Cybersecurity technological tools also exist to augment these training efforts, such as antivirus or malware programs, that either prevent virus-infected emails from reaching you at all, or neutralize the threat within your inbox / system.
One further tool, the 3rd remaining Cyber-term cited at the beginning of this blog, is OpenDNS — think of it as an encompassing web filter that prevents you from going to an infected, malicious, or undesirable (content-wise) website, even if you tried.
OpenDNS represents another security layer in an overall Cybersecurity protection scheme. We spoke of:
- Automated or manual spam filters
- Company training to identify malicious files or links and instruction to not open anything from an unknown user
- Built-in application security such as macro detection and suppression
- Antivirus or malware software to neutralize known, found threats
Beyond dangerous files, those malignant macros within Office documents can also take users to unsafe / inappropriate websites. OpenDNS is a very cost-effective security measure that prevents reaching those bad websites at all, representing a final-layer shield that can protect users even if they (deliberately or accidentally) try to access unsafe sites.
Well detail the ins and outs of OpenDNS in a future post.
About the Author