
Since the beginning of the 21st century, the concept of Information Technology (IT) has shifted significantly. To the average person, IT no longer means possessing the capability to simply search the web using keywords, neither does it focus only on clunky desktop computers. With technology’s evolution, IT has expanded to include numerous subsets — from programming to engineering to security to analytics and beyond.
The “information” aspect includes far more than obtaining sensitive data or protecting it. Systems now possess the capabilities for complex queries, extrapolating data, predicting future events, and even advising officials. This access and wealth of knowledge inevitably led to the expansion of the IT security field. Are you familiar with the basics of cybersecurity? Read on to learn about the different types of IT security and how you can protect your business.
IT Security versus Cybersecurity
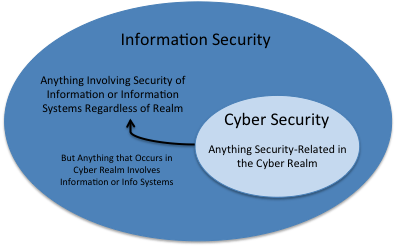 Although closely related, IT security differs slightly from cybersecurity. IT is broader in nature and focuses on protecting all of an entity’s data — whether that data be in electronic or a more physical form.
Although closely related, IT security differs slightly from cybersecurity. IT is broader in nature and focuses on protecting all of an entity’s data — whether that data be in electronic or a more physical form.
For example, IT security would encompass securing keypads that allow access to a room full of data files.
Cybersecurity tends to focus on criminal activity facilitated specifically through the Internet. In many cases, such criminal activity affects an entities electronic data and daily operations.
Despite the slight differences, IT security and cybersecurity roles and frameworks often overlap. If a business has both an IT and cybersecurity department, the precautions of one department will likely parallel those of the other. Regardless, it’s worth understanding the general differences and similarities before considering the various categories of IT security.
In general, IT security includes databases, software, applications, servers, and devices. In order to ensure protection, IT security also includes the concept of information assurance. Information assurance refers to the acronym CIA – confidentiality, integrity, and availability.
Assess your IT Security
What Are the Types of IT Security?
Depending on which experts you ask, there may be three or six or even more different types of IT security. Each security expert has their own categorizations. Furthermore, as networks continue to expand with the cloud and other new technologies, more types of IT security will emerge.
However, for the most part, there are three broad types of IT security: Network, End-Point, and Internet security (the cybersecurity subcategory). The other various types of IT security can usually fall under the umbrella of these three types.
1. Network security
At its simplest, network security refers to the interaction between various devices on a network. This includes the hardware and the software. Network security, according to SANS Institute, strives to protect the underlying networking infrastructure from unauthorized access, misuse, malfunction, modification, destruction, or improper disclosure, thereby creating a secure platform for computers, users, and programs to perform their permitted critical functions within a secure environment. One of the major goals is to prevent unauthorized personnel or device access.
For thorough network security, start with configuration. Make sure that from the get go all device configuration incorporates reasonable preventative measures. Next, put in place a detection system. For example, detection software analyzing logins could check for irregularities. Finally, set up response protocol for if and when a breach occurs. This will ensure smooth communication and hopefully minimize the damages of the network insecurity.
Some common methods of network protection include two-factor authentication, application whitelisting, and end-to-end encryption. Additionally, using a security framework, such as NIST’s cybersecurity framework, will help ensure best practices are utilized across industries. Whether the framework is more cybersecurity or IT based is a marginal concern, the key is to have some set of guidelines to follow when setting up or improving security operations.

2. End-Point Security
Another key to IT security focuses on the devices involved. It is crucial to verify that only authenticated devices access the system or data. In other words, endpoint security targets security threats from a device-level viewpoint (e.g., laptops, cell phones, tablets). Each new connection on an entity’s network widens then the threat intelligence field.
End-point protection software may include privileged user control, application controls, data controls, intrusion detection, and encryption. Encryption ensures the integrity of data being transferred, while application security controls protect against dangerous downloads on the user’s end. Furthermore, security departments typically install such software not only on the device in question, but also on the company’s server. When a security update occurs, the central server pushes the update to all end-point devices, thus ensuring a certain level of security uniformity. Likewise, having a central sign-in page allows enterprises to monitor who logs on and tracks any suspicious behavior.
3. Internet Security
Internet security, as noted above, tends to fall under the name of cybersecurity. It deals largely with the transit of information. For example, imagine you send an email, and while that message is in transit, a third party sweeps in and takes it before the message is delivered to its intended recipient (i.e., man-in-the-middle attack). Such hijackings are just one of many examples of crimes regarding the Internet. In such a case encryption serves as one method of defense, making any stolen information significantly less valuable to the perpetrator.
In particular, Secure Sockets Layer (SSL) and Transport Layer Security (TSL) are forms of encryption and authentication commonly used by business for their online platforms. They create public and private keys when interactions with customers take place, ensuring the integrity of the data during transactions. Sites using such encryption methods will usually have https in the address bar along with a small lock icon. Other common security measures for the Internet include firewalls, tokens, anti-malware/spyware, and password managers.
Beyond network, end-point and Internet security, the introduction and expansion of the cloud and the extensive application market also warrants attention. Cloud security parallels on premise security procedures in that the goals are generally the same – to protect stored date and data in transfer. The main difference lies in the expansion of the security “border.”
With the widened perimeter to protect, Redhat suggests a layered approach, taking the time to build in security defense in layers (e.g., encryption, multi-factor identification) at every level of the cloud (i.e., hosted resources delivered to a user via software). If not building an internal/company cloud, cloud providers also offer different security tools and protective measures. In either case, cloud management plays a key role in securing Internet infrastructures.

Checklists for IT Security
Understanding the different sectors of IT security helps significantly when trying to organize a strong defense against intruders. However, like most defense strategies, the plan will vary depending on the resources available.
Consequently, below are two separate checklists – one for small businesses and one for larger entities. Many of the smaller business recommendations apply to larger firms as well. Even if the checklist seems overwhelming at first, the goal is to take tangible steps to further bolster security. Such checklists help overcome the information overload of simply reading about best practices and current security concerns.
For Small Businesses:
Although small and large companies both struggle with internal breaches, smaller companies tend to have more vulnerabilities to such kinds of attacks. For example, an employee unwittingly downloads a malicious link for a supposed free vacation on a company computer. It’s easy to make such mistakes when you don’t know what you are looking for. However, because smaller companies often lack the resources to quickly combat and rebound after the attack, they must put in more effort to combat internal security risks. So what can small to medium companies do?
1. Educate employees
Make sure to create an IT security plan and disseminate it to all employees. For example, education awareness training policies should include password guidelines, external download procedures, and general security practices. It’s crucial to know why your team needs cyber security education.
Likewise, draft a policy directed at vendors or contractors. Even though it expands the security policy boundary, including vendors and contractors is vital, as consumers will likely still blame a small company for a breach even if the vendor was actually to blame. Having a clear third-party cyber risk assessment policy will assist entities facing repercussions in the aftermath of a security breach.
Additionally, small businesses should outline clear physical security measures to protect customer information, such as locking filing cabinets and keeping private information well out of reach of any wandering eyes and restricting physical access to cardholder data.
2. Data Redundancy
First, analyze how information is stored. Is critical information stored in only one location? If yes, consider how this information would be affected in the event of a ransomware attack.
Ransomware could cripple a business if data is only stored in one central location. Storing essential data backups (i.e., what is needed for minimum daily operations) in secure off-site location will ensure operations do not completely halt if a hacker or malicious code compromises a system. Furthermore, such backups should be updated on a regular basis. However, if storing data off-site, it is again important to verify such off-site servers and equipment is secure (e.g., utilizing encryption).
3. Hardware and Internet Security
Make sure company computers update whenever new security patches become available. Password management requirements should also be outlined in the company security policy. For example, encourage employees to use passphrases or complex passwords and to change them from time to time.
If passwords are difficult to remember, consider using a password manager. ConsumerAdvocate.org published a list of top password managers for 2019. Also, install anti-virus software and establish a procedure for downloading/installing new software. For the Internet, monitor internet connection points and consider using a virtual private network (VPN). Lastly, invest in Internet intrusion software.
4. Upkeep
Put in place an audit system to test your cyber incident response plan, review current security status, and evaluate if any areas need improvement. Auditing every six months is a general good practice for small entities.
For Larger Entities:
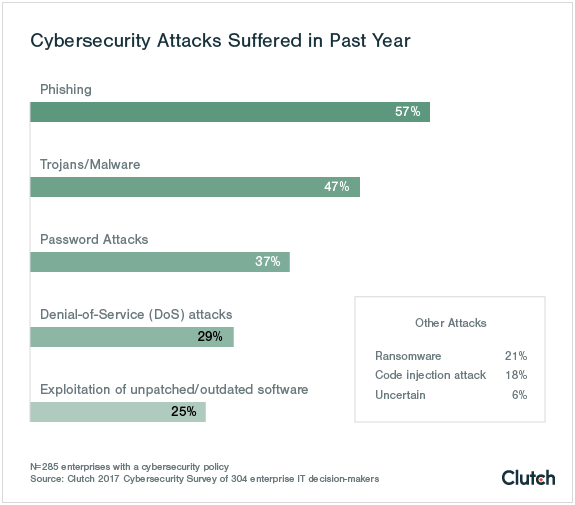
Larger entities tend to deal with more extensive or sophisticated attacks. Such attacks center on the field of cybersecurity. A 2017 Clutch large business survey found that phishing proved the most common type of attack followed by Trojans.
General concepts apply to large businesses as well – inform employees, monitor compliance, and enforce security policies. However there are some scenarios unique to larger enterprises.
1. Remote work policies
Larger companies increasingly offer the option for employees to work at home. Not only is this option cheaper for them, as it reduces overhead costs, but it also appeals to both young and old workers (e.g., less time in traffic appeals to older generations and less traffic is better for the environmental which appeals to younger generations). However, remote work expands the threat environment and makes it more difficult for IT departments to control.
There are a few steps every company can take to improve the safety of remote work.
First, educate employees on the difference between suspicious emails and password protection. Likewise, emphasize the importance of utilizing a work computer only for work; the more programs (not work related) downloaded onto the computer, the more vulnerable the machine becomes.
Second, provide a VPN for remote workers to help mitigate Wi-Fi breaches of your WiFi security having been krack’d and install the ability to remotely wipe the computer in the event the device falls into the wrong hands.
Lastly, take advantage of cloud computing. Using the cloud offers another layer of security as cloud service providers, like Amazon and Google, have significant resources to allocate for securing their cloud platforms.
2. Investing in new technology
Bigger companies have a greater number of employees to monitor and often locations to secure. Consequently, they will have to invest in more extensive defense mechanisms. Using automated security tools will reduce the manpower needed for constant monitoring. For example, the Open Web Application Security Project (OWASP) provides a list of viable web application security scanners. Other useful tools include penetration(e.g., AttackIQ FireDrill) and intrusion testing (e.g., Bricata) software.
Needless to say, there is a plethora of advanced cybersecurity software available to help companies protect their assets, but companies must first understand the validity of investing in such tools.
Need Help?
So what’s the overall takeaway? Every business, and to a certain extent every individual, should implement IT security measures. For mid to large sized businesses, this will include a heavier emphasis on cyber security. The key is to evaluate where your business is at now and create a plan based on any weaknesses. It is also vital to research the best products out there and find the ones that will best fit your entity’s needs. To get started on an IT or cybersecurity solutions plan today, contact RSI Security.


1 comment
Your top-notch services demonstrate your dedication to cybersecurity excellence. The aptitude and persistence of the RSI Security group have been instrumental in shielding our advanced resources. A commitment to staying ahead of changing threats is demonstrated by the thorough assessments, proactive solutions, and ongoing support. RSI Security has genuinely turned into a confided in accomplice in our network protection system.