Most people would agree that basic human rights include privacy. However, social media, computers, and the Internet have eroded the traditional privacy and security barriers put in place. Documents can be shared with a simple click and access granted with credentials. Society can no longer dictate, in many cases, who or what has access to Personal Identifiable Information (PII).This especially affects healthcare provider entities, which up until the late 1990s and early 2000s kept most records in paper format.
With the new ease of electronic communication, security can sometimes fall to the wayside. To ensure patient confidentiality within these new technological parameters, the U.S. government established the Health Insurance Portability and Accountability Act (HIPAA) in 1996. In addition to mandating health administrative guidelines, HIPAA included specific privacy protocols later updated in the HITECH Act. When creating a HIPAA compliance strategy for your company, you must, therefore, know all the pertinent health insurance facts. Read on to learn about the top 5 components of the HIPAA Privacy and Security Rule.
HIPAA Privacy Rule Summary
Initially, the Privacy Rule went into effect in 1996, as a subcategory of HIPAA. A broad HIPAA Privacy Rule Definition encompasses the following — a set of guidelines for how to implement breach notifications, maintain secure data storage, safely transmit patient PII, and ensure accountability in the workplace. While earlier privacy acts focused on government agencies, HIPAA expanded the field, requiring private health entities to comply with the new security and privacy standards. In 2003, HIPAA privacy compliance became mandatory for health care providers, health care clearinghouses, relevant business associates, and any entity accessing or transferring patient data. HIPAAs policies and procedures ensure accountability throughout the file transfer process, from patient permission to employee access. For example, HIPAAs Privacy Rule recommends encrypting files, requiring access passwords, and training employees in security best practices. Furthermore, HIPAAs Privacy Rule, and the fact that it is a legal obligation, helps ensure that entities storing or using PHI/PII constantly reassess how to better protect consumer data, as most enterprises seek to avoid breaches and hefty penalties. Ultimately, HIPAAs Privacy Rule seeks to balance patient confidentiality with efficient communication among health professionals and businesses.
Assess your HIPAA / HITECH compliance
HITECH Privacy Updates
After the enactment of the 1996 HIPAA Rule, technology and electronic transfers increased significantly, prompting the government to draft more relevant guidelines regarding Electronic Protected Health Information (ePHI). Subsequently, the Health Information Technology for Economic and Clinical Health Act (HITECH) went into effect in 2009. HITECH updates modified HIPAAs initial penalties and makes non-compliant entities more culpable for privacy shortcomings. In addition to willful neglect penalties, todays entities now face even higher fines if the privacy and security flaw remains uncorrected. Enterprises must promptly notify consumers or employees of any breaches, even if the breach entry point is closed. Furthermore, any breach that affects more than 500 patients must be reported to the Health and Human Services (HHS) office. HITECH also requires the HHS to audit all enterprises covered under HIPAA as well as any business partners, although no timeline is given for when such audits must occur.
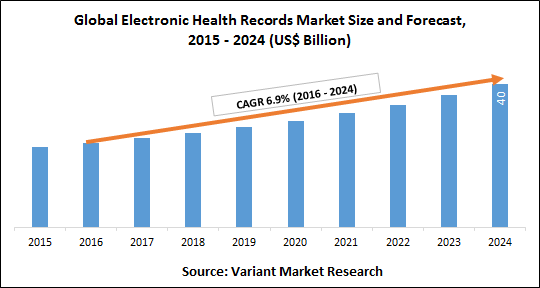
To improve accessibility, HITECH mandates that patients and third parties have the right to access electronic health records. While this may take the form of a scanned document sent via email, HITECH recommends health entities start the shift toward utilizing Electronic Health Record (EHR) systems, as apps and websites will gradually become the primary platform for accessing PHI. Lastly, HITECH places more stringent requirements on health entities to vet business partners prior to any interactions. Rather than only having to guarantee personal compliance (i.e., the company sending information), compliant entities must also confirm business partners abide by the same HIPAA and HITECH rules.
Understanding PII versus Sensitive PII
Although not all information requires the same level of security, some information, that at first may seem harmless, can become damaging when combined with other related details. The Department of Homeland Security (DHS) designates two forms of personal information PII and Sensitive PII.
Regular PII includes information from which personal details can be inferred or deduced. In other words, there may be a direct or, in many cases, an indirect link to an individual. For example, a business card falls under PII category, as it identifies a link with an individual and would likely lead to other similar PII links if investigated by a threat actor.
However, Sensitive PII refers to any information that, when lost or illegally disclosed, could result in substantial harm, embarrassment, inconvenience, or unfairness to an individual. Due to the greater risk Sensitive PII presents, it requires a higher level of protection.
Sensitive PII is further divided into always sensitive and sensitive by link categories. For example, Social Security Numbers (SSNs), drivers/state license, passport numbers, and biometric identifiers are always classified as Sensitive PII. By themselves, names, emails, financial records, and medical records, are classified as PII, but if obtained together (e.g., at least two), they gain the status of Sensitive PII. In other words, the more pieces of the PII puzzle a threat actor obtains, the more likely identity theft or another extremely harmful result will occur.
The above information highlights why HIPAAs Privacy Rule is so important, as health entities typically store and access such PII on a daily basis. Consequently, developing a security and privacy strategy is vital.
HIPAA Privacy Components
With HIPAA, two sets of rules exist: HIPAA Privacy Rule and HIPAA Security Rule. Each HIPAA security rule must be followed to attain full HIPAA compliance. However, it is sometimes easy to confuse these sets of rules because they overlap in certain areas. The HIPAA Privacy Rule focuses on Protected Health Information (PHI) whereas HIPAA Security Rules focus specifically on ePHI.
The five general categories below encompass almost all of the major points of the Privacy Rule. Together, the components address the internal and external threats companies face, as well as the publics right to control their PII and PHI.
1) Limited Access
Access to patient medical files and any other PII should be limited. Physical files should be kept in locked file cabinets and remain secure at all times. When files are removed for secretarial or work purposes, they should be kept out of reach from public view (i.e., wandering eyes should not be able to peak at confidential documents). Likewise, employee access must be designated on a need-to-know basis.
Experts recommend formulating access criteria and then assigning different levels of authorization. For example, if an individuals sole role is scheduling appointments, accessing patient data is likely unnecessary. Similarly, billing employees would not require access to physician notes in order to fulfill their duties. Access boundaries based on employee responsibilities helps mitigate risk and may even improve efficiency by reducing the amount of information that requires processing.
2) Data Transfers
Due to the nature of healthcare, physicians need to be well informed of a patients total health. Before disclosing any information to another entity, patients must provide written consent. Certain entities requesting a disclosure only require limited access to a patients file. Workers compensation claims do not require a detailed medical history; rather, only financial transactions and hourly work information are necessary.
In most PII transfers, entities should provide the minimum amount of PHI/PII needed to complete the required task. Yet, when it comes to medical referrals, HIPAAs privacy rule allows physicians to determine what constitutes necessary information. Who transfers files and when they are transferred is also vital information to record. Keeping detailed records of all file transfers (i.e., who, what, when, to whom) will aid in audit processing, improve accountability, and help minimize risk. If data transfers are occurring outside electronic systems, precautions must also be taken. For example, if a healthcare entity moves to a new office and must transport physical files, the company should designate a person to oversee the process. Such an individual would take stock of files to be transported, ensure the files remain locked during transport, and verify all files arrive at the location.
3) Patient Rights
Surprisingly, 41% of Americans have not seen their health information, despite the numerous access rights HIPAA grants. In addition to information security, the Privacy Rule also focuses on increasing transparency with consumers. Patients possess the right to request their medical records, whether in electronic or paper format. They also have the right to know who accesses their health information and what information is disclosed to other parties. Medical practices have a responsibility to assist patients in this process to the best of their ability. However, as with all data transfers, physicians must ask patients to complete consent paperwork before releasing information.
When files are transferred to personal accounts (e.g., email), consumers should be informed of the security risks, such as sending documents to an unsecured email account. Unlike with business partners, enterprises are not legally bound to verify consumers use secure platforms; they are only bound to provide a warning. Moreover, HIPAA requires the disclosure of any transfer fees prior to the sending of information. Lastly, health entities must protect not only physical/electronic health records, but also any conversations with physicians, recorded billing information, and insurance systems.
Helpful Tip: Invest in a reliable, easy to use electronic record system, as it will improve efficiency when looking up or transferring patient files.
4) Privacy Officer
Due to the seriousness of the data involved and the detailed privacy rules, HIPAA requires compliant enterprises to designate a Privacy Officer. If a small company lacks the ability to create a new position, an outside Privacy Officer may be hired. A Privacy Officer designs a plan for privacy compliance, oversees its implementation, and then ensures the plan and employees stay updated on any changes in the rules. Furthermore, such officers will address any privacy breaches or accusations of non-compliance.
One of the first tasks a Privacy Officer must complete is an internal review of the current level of compliance. It is vital to understand the weak points in privacy practices before developing a plan to maximize security resources and maintain efficiency. When a Privacy Officer implements changes, employees must be made aware through training sessions or other communication channels. Lastly, a Privacy Officer will communicate progress and receive information from the HIPAA Compliance Officer and HIPAA Security Officer. Due to the overlapping nature of these positions, some of the responsibilities appear the same; however, any overlapping aspects provide a safety net in case one officer misses an important detail.
5) Partner Compliance
After receiving consent from patients, entities may legally transfer data to other healthcare entities; however, the recipients must also be HIPAA compliant. The responsibility lies with the healthcare enterprise (i.e., company sending data) to ensure the receiving office/business follows correct privacy procedures (e.g., encrypting data). The term partner refers to any entity receiving, processing, or storing (externally) data. Examples include legal firms, financial analysts, or data aggregation centers.
Helpful Tip: Creating a generic HIPAA compliance contract will save time as employees can quickly add the necessary, more specific details when transfers occur. The HHS provides a sample business associate contract.
HIPAA Help
To assist in formulating a compliance strategy, the Office of the National Coordinator for Health Information Technology (ONC) provides numerous resources. For small businesses, the ONC created a 7-step template for improving security with only minimal resources. Additionally, the ONC provides a downloadable Security Risk Assessment (SRA) tool with accompanying videos. For improving technical compliance (i.e., utilizing secure electronic devices and software), the Certified Health IT Product List allows entities to compare products, identify de-certified products, search for products currently in use, and various other tasks.
Importance of Compliance
Not complying with HIPAAs Privacy Rule results in both legal consequences and public relation nightmares. Furthermore, violating HIPAA standards can result in significant fines, based on the level of negligence. Worst case, non-compliant entities may receive a $50,000 fine per violation (maximum $1.5 million/year). Credibility remains a vital cornerstone of the health industry, as society seeks trustworthy companies to handle personal data.
The expanding market for health applications and the shift toward electronic health information makes accessibility easier for consumers but also expands the threat surface. Consequently, entities must analyze current computer security and physical security measures, adjusting such privacy practices to comply with HIPAA Privacy and Security Rule. For more information on cyber security solutions, contact RSI Security today.
Download FREE HIPAA Compliance Checklist
 |