There were 1,579 data breaches with over 178 million records exposed in 2017 alone. That averages about four data breaches a day for the entire year of 2017. Let that sink in for a second. That amounts to a nearly 45% overall increase over 2016 figures. Thankfully, there are ways that you can avoid a data breach, but these figures still lend themselves to have a bit of sticker shock. One way that companies can protect themselves from payment card data breaches is protecting their cardholder data environment (CDE) via PCI (Payment Card Industry) DSS (Data Security Standard) compliance. Any organization or merchant that accepts, transmits or stores any cardholder data must comply with PCI DSS.
Thats where point-to-point encryption (P2PE) comes into play.
Considered the gold standard for encryption services, P2PE is the holy grail for companies looking for opportunities to secure their cardholder data environment (CDE) from potential phishing or malware threats while still remaining PCI compliant. But when searching for the holy grail of P2PE solutions, one must drink from the right chalice to receive eternal data protection. That P2PE solution may or may not need to be validated against Payment Application Data Security Standards (PA-DSS). How do you determine if it does or not? Read on to find out:
What is P2PE?
P2PE is an official program of the PCI Standards Council since 2011. The huge demand that spawned from the introduction of this program was led by the programs automatic compliance simplification (aka scope reduction). Although the use of P2PE solutions is not mandatory, compliance with The Councils standards reduces the P2PE Self-Assessment Questionnaire to only 26 requirements. Failure to comply leaves a merchant vulnerable to a data breach and the ensuing negative fallout including fines, fees, and reputational damage. The PCI DSS includes requirements for security policies, procedures, management, software design, network architecture, and other protective measures.
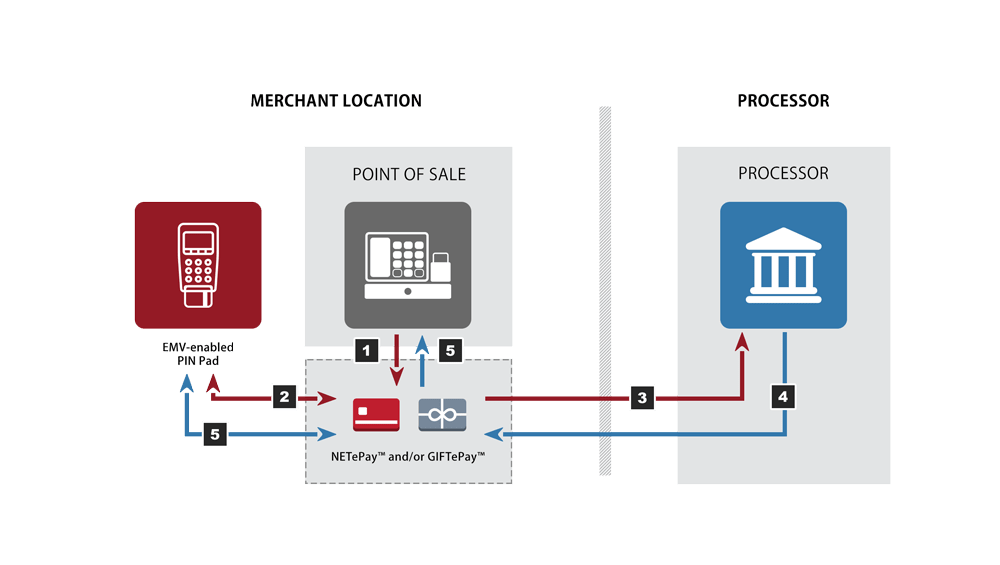
In card-present environments, including traditional and mobile points of sale, P2PE protects the merchants communication channels where tokenization cannot: between the payment device and the processing network. During transmission, P2PE can encrypt sensitive payment card data. That data remains encrypted until it reaches a safe decryption environment. P2PE adds an additional layer of security and protects consumers payment information (as well as the merchants payment processing environment) from a variety of attacks, including malware infections in the POS terminal or system.
Hackers are persistent in identifying and exploiting weaknesses in a merchants payment system. The way your customers provide their card information can also trip you up if you dont have a P2PE solution. Customers can swipe with a magnetic stripe reader, tap with an NFC or contactless reader, or dip with an EMV (chip) reader. Magnetic stripe information can be duplicated, but the EMV chip generates a one-time transaction code for each payment, which makes it extremely difficult for hackers to create a duplicate card.
P2PE encrypts CHD from the moment a card is dipped, swiped, tapped, or keyed at a payment terminal, meaning the card data never actually enters the point-of-sale system. The role that P2PE plays in the trifecta is to remove the CHD from the merchants payment processing environment entirely, leaving nothing behind that is of any use to hackers and rendering fruitless the criminals attempts at stealing CHD from the point of interaction. P2PE can protect payment data in the event of a breach. It also devalues the data, so it cant be used even if it is stolen. Thus, your organization would not only reduce its risk of a breach, but also limit its reputational and financial risk.
P2PE Validated Application
Merchants using PCI-validated P2PE solutions also have fewer applicable PCI DSS requirements, which helps simplify compliance efforts. However, a PCI P2PE solution is just one piece of PCI compliance. Merchants must also meet other requirements that include the key themes of education and awareness, increased flexibility, and security as a shared responsibility.
Implementing strong encryption solutions, device management, and key management practices allows P2PE to address CDE compromise. Whether the customer card data is in transit out of the merchant network or transmitted to the gateway/acquirer for processing, P2PE is the effective standard for combating malicious threats. A PCI-Validated P2PE solution includes validated hardware, software, and solution provider environment and processes:
| A PCI-validated P2PE solution must include all of the following |
| Secure encryption of payment card data at the POI / i.e., the payment terminal |
| P2PE-validated application(s) at the POI |
| Secure management of encryption and decryption devices |
| Management of the decryption environment and all decrypted account data |
| Use of secure encryption methodologies and cryptographic key operations, including key generation, distribution, loading/injection and administration |
PCI-validated P2PE solutions have been assessed by a P2PE QSA as having met the PCI P2PE standard and are therefore listed on the PCI website under Approved P2PE Solutions. In addition to meeting the P2PE standard, the decryption component of the solution must operate within a secure environment that is annually assessed to the full PCI DSS standard. Another key advantage to using a PCI-validated solution is that its been vetted by The Council. Validation is completed by an independent P2PE Qualified Security Assessor (P2PE-QSA). This means it stays relatively fixed as PCI-validated P2PE only expires after a few years.
Merchants who use a validated solution within their environment and keep this environment segmented from any card data from other channels (e.g., e-commerce) are eligible to complete the authorized self-assessment questionnaire SAQ P2PE that is known and accepted by all acquirers. Under PCI DSS v3.2, this represents a significant reduction of controls, reducing the number of questions by nearly 90% for merchants moving from the SAQ D (329 questions) to SAQ P2PE (33 questions).
The scope of the merchants PCI DSS assessments is dramatically reduced because their payment systems wont ever handle sensitive CHD. If P2PE cannot be implemented on existing hardware, vendors should at least consider securing the communication between their PIN pads and the POS software with TLS (Transport Layer Security) and to digitally sign all requests sent back to the PIN pad by the payment application.

SAQ P2PE-HW
There are eight different SAQs that organizations can take (A, A-EP, B, B-IP, C, C-VT, D, and P2PE-HW). SAQ P2PE-HW is only for merchants that use card-present type of transactions, meaning that SAQ P2PE-HW is not applicable to e-commerce organizations. SAQ P2PE-HW merchants may be either brick-and-mortar (card-present) or mail/telephone-order (card-not-present) merchants. For example, a mail/telephone-order merchant could be eligible for SAQ P2PE-HW if they receive cardholder data on paper or over a telephone, and key it directly and only into a validated P2PE hardware device.
To be eligible these merchants must not store any cardholder data and they must also protect cardholder data using a validated P2PE solution:
| Merchant qualifications for SAQ P2PE |
| All payment processing is through a validated PCI P2PE solution approved and listed by thePCI Security Standards Council. |
| The only systems in the merchant environment that store, process or transmit account data are the Point of Interaction (POI) devices which are approved for use with the validated and PCI-listed P2PE solution. |
| Your business doesn’t otherwise receive or transmit cardholder data electronically. |
| There’s no legacy storage of electronic cardholder data in the environment. |
| If your business stores cardholder data, that data is only in paper reports or copies of paper receipts and isn’t received electronically. |
| Your business has implemented all controls in the P2PE Instruction Manual (PIM) provided by the P2PE Solution Provider. |
Merchants can process card data via PCI SSC-listed, P2PE payment terminals that can include physical and remote transactions. With PCI Validated P2PE solutions, network segmentation is not necessary due to no clear-text, sensitive credit card data entering your system. Organizations that have failed to implement all the controls in the P2P encryption solutions manual provided by the vendor will not be eligible for this questionnaire.
What is PA-DSS?
Payment Application Data Security Standard (PA-DSS) is a set of requirements that are intended to help software vendors develop secure payment applications that support PCI DSS compliance. The PA-DSS is the standard that applies to software vendors and others who develop payment applications that store, process, or transmit cardholder data and/or sensitive authentication data. Software applications developed by merchants for in-house use only are exempt from PA-DSS but must comply with PCI DSS.
The Council specifies that:
The goal of PA-DSS is to help software vendors and others develop secure payment applications that do not store prohibited data, such as full magnetic stripe, CVV2 or PIN data, and ensure their payment applications support compliance with the PCI DSS. Payment applications that are sold, distributed or licensed to third parties are subject to the PA-DSS requirements. In-house payment applications developed by merchants or service providers that are not sold to a third party are not subject to the PA-DSS requirements, but must still be secured in accordance with the PCI DSS.
The PA-DSS can be used by your internal assessment team to validate a providers or partners payment application. The Council keeps a list of validated payment applications, but you may want to perform your own independent audit of the payment application by using PA-DSS as a kind of audit and assessment guide.

P2PE Validated Against PA-DSS?
The best thing about a P2PE solution from a company’s perspective is that all accountability for PCI DSS compliance is automatically the solution providers responsibility. Its down to the solution provider to ensure all the requirements of the standard are met and that they are providing a complete and secure system. One thing to note is that having a PCI Validated P2PE does not equate to the P2PE solution being PCI DSS compliant. PCI DSS and PCI Validated P2PE are two entirely separate standards and few companies in the world have met the PCI P2PE standard.
If fraud or a data breach does occur, the P2PE solution provider will be held accountable for any ensuing fines or penalties, rather than the merchant. Through leveraging a PCI-validated P2PE solution provider, your organization can confidently open more payment channels to collect payments including omni-channel payment solutions. This allows you to collect payments at every customer interaction point with the highest level of payment security and compliance.
Since the decryption is carried out electronically, the merchant or processor does not have to decrypt data manually nor do they need access to the secure key; therefore, they never have access to their customers personal card data. The P2PE solution will even supply a token to the merchant with each transaction, helping them to identify and refund or rectify a payment in the future, without ever revealing the card information. Merchants who accept at least 75% of their transactions through a PCI-validated P2PE service may qualify to apply through their acquirer for the Visa TIP program, which allows approved merchants the ability to discontinue their annual assessment process to revalidate PCI DSS compliance.
By the end of this year, 93% of retailers expect to have adopted P2PE with 61% of retailers also expecting to have adopted tokenization, which protects information while its being stored in a database. To require PA-DSS compliance, these applications must be sold, distributed or licensed to third parties. In other words, if you wrote your own payment application that you use in your organization, it must be PCI DSS compliant but not PA-DSS compliant. If you are a payment vendor that sells your payment application to customers, it MUST meet PA-DSS.
Closing Thoughts
With the number of available PCI-validated P2PE solutions growing by over 700% in the past 4 years and tremendous growth since the PCI Council announced P2PE in 2011, we can see that there is a fierce demand for these solutions amongst payment processors. The fact remains: 60% of small to medium-sized retailers at risk of going belly up within six months of a data breach and data breaches are growing in number and ferocity with no inkling of slowing down. Implementing a P2PE-validated solution that meets PA-DSS in your network infrastructure will make you sleep better at night knowing your CHD are safe at every point of interaction (POI) device.
Download Our PCI DSS Checklist
Assess where your organization currently stands with being PCI DSS compliant by completing this checklist. Upon filling out this brief form you will receive the checklist via email.




1 comment
Hi there, You have done a great job. I will certainly digg
it and personally suggest to my friends. I’m confident they’ll be
benefited from this site.