Business owners should know the answer to the question, how prepared is your business to face cyber threats? However, most do not. The National Institute of Standards and Technologys (NIST) cybersecurity framework is one of the most recognized structures for improving sensitive data security against todays cyber threats from all devices. Meant to be a voluntary framework for taking security measures to identify and minimize cybersecurity risks, the NIST framework has been used in a wide variety of industries. In this article, well break down why the NIST framework was created, how it is structured, and how it helps to create a robust cybersecurity risk-management strategy. The NIST framework can be daunting at first, particularly for smaller organizations that may not be sure how to leverage the framework to create actionable insights into gaps in their cybersecurity. The information provided in this article should prove as a helpful starting place for organizations wishing to get a brief introduction to the NIST framework, as well as highlight some of the key advantages that adopting the NIST framework brings to organizations of any size.
Background of the NIST Framework
The NIST Cybersecurity Framework, often referred to simply as the Framework, was developed following Executive Order 13636. Signed by President Obama in 2013, Executive Order 13636 charged NIST with developing a comprehensive framework for helping both private and public sector entities in charge of critical infrastructure defend against cyber threats. The NIST Framework exists as an ongoing effort to figure out how to improve security of critical infrastructure against persistent and varied cyber threats from hackers and malware. During the year following EO 13636 the Framework was developed through a close partnership between the public and private sectors. At the same time that version 1.0 of the Framework was released, the developing partners also created a roadmap for future growth and development of the Framework. Version 1.1 of the Framework was adopted April 1st, 2018 following a lengthy period of continued development. The full text of the Framework can be found here, and will serve as a helpful reference point for organizations looking to incorporate the NIST Framework into their cybersecurity presence.
The Purpose of the NIST Framework
From the outset, the NIST Framework was developed to provide a roadmap towards an enhanced cybersecurity presence for critical infrastructure in the United States. Prior to the adoption of the NIST Framework, there was a wide recognition in the field of cybersecurity that both state and non-state actors could potentially cripple U.S. infrastructure through a cyber attack. This threat not only continues to be present, but increases with each passing year as the technology to stage attacks against infrastructure continue to become more available, more complex, and easier to use.
Although the NIST Framework is becoming an increasingly popular tool for organizations trying to figure out how to improve cybersecurity, there are some misconceptions about the Framework that can lead to confusion. Foremost among these is the belief that the NIST Framework is meant to replace an organizations existing cybersecurity plan. In reality, the NIST Framework is meant to be used as a guide towards a risk-management based approach to cybersecurity that can be incorporated into an organizations current cybersecurity efforts. The NIST Framework is intended to be a flexible roadmap and structure that can be applied to organizations in any industry and of any size, and be used to determine gaps in current cybersecurity efforts and develop strategies to close those gaps over time. Thus, embedded in the NIST Framework is a structure that can help organizations develop a cybersecurity presence centered on a recognition of the security risks that the organization faces.
A second misconception about the NISTsecurity model is that it is meant to be applied in the same way, regardless of the size or industry of the organization. In contrast to this, the Framework was not developed as a one-size-fits-all approach to cybersecurity. The Framework recognizes that this simply isnt realistic or ideal. Smaller organizations will not have the same risks, threat profiles, or vulnerabilities that large organizations have. The same is true across industries. Owners or operators of critical infrastructure must maintain a much more robust cybersecurity presence than organizations not responsible for critical infrastructure. Rather, the NIST Framework is intended to be flexibly applied in each organization as they see fit, given their specific vulnerabilities, security threats, and tolerance for risk. The voluntary structure of the NIST Framework allows organizations with fewer resources to apply the same industry-recognized cybersecurity best practices to their organization while allowing them the flexibility to adapt the implementation of the Framework to their unique cybersecurity situation.
Structure of the NIST Framework
The NIST Framework is broken down into three primary components which work together to help organizations transition to a risk-management based cybersecurity plan. These components are the: Framework Core, Framework Implementation Tiers, and Framework Profiles. Each of these components is meant to work together to help organizations develop a comprehensive cybersecurity strategy that incorporates their own unique business and mission goals with their cybersecurity presence. Not all organizations choose to use all three components of the Framework, and many organizations use these components to varying degrees depending on their own unique situation. Gaining a greater understanding of the Framework components can illuminate how the NIST Framework can be used to enhance your organizations cybersecurity presence over time.
Framework Core
The Framework Core provides a set of activities that are tied to desired cybersecurity outcomes for organizations. The Framework Core is broken down into elements and functions. The elements of the Framework Core work together to help organizations determine their current cybersecurity presence, and provide a helpful way to organize their cybersecurity efforts through an industry recognized model. The elements of the Framework Core are Functions, Categories, Subcategories, and Informative Resources. There are five Functions in the NIST Framework. These are Identify, Protect, Detect, Respond and Recover. These functions interact with the aforementioned elements of the Framework Core to help organizations better understand their current cybersecurity posture and organization.
An important note about the Framework Core is that the elements and functions are intended to work together. The functions set forth in the Framework Core are inherently broad and come with the recognition that each of these functions occurs simultaneously. If used as the Framework Core intended, each Core Function can be broken down into Categories that are tied to desired cybersecurity outcomes. For example, outcome Categories tied to the Protect Function would be: Data Security, Identity Management and Access Control, or Awareness and Training. Each of these Categories could be further broken down into subcategories with specific outcomes tied to them.
Framework Implementation Tiers
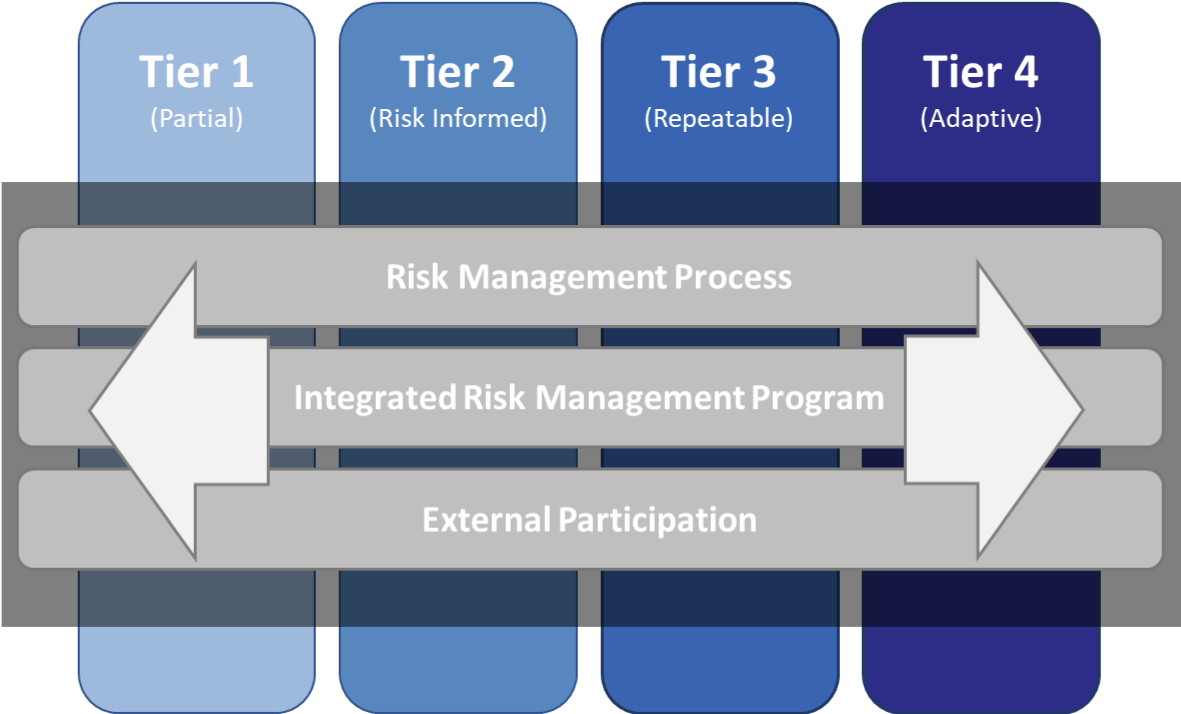 The second component of the NIST Framework is Framework Implementation Tiers. These Tiers serve as a method for organizations to assess their current cybersecurity posture. In particular, the Tiers are used to determine how an organization views their cybersecurity risks and the processes and systems the organization has in place to minimize those risks. There are four Tiers in the Framework that range from Tier 1 (Partial) to Tier 4 (Adaptive). Determining which Tier your organization falls into involves a selection process that incorporates key metrics for your organization. These include an organization’s threat environment, business objectives, risk management approach, cyber security policies for their supply chain, organizational resources, and legal and regulatory requirements.
The second component of the NIST Framework is Framework Implementation Tiers. These Tiers serve as a method for organizations to assess their current cybersecurity posture. In particular, the Tiers are used to determine how an organization views their cybersecurity risks and the processes and systems the organization has in place to minimize those risks. There are four Tiers in the Framework that range from Tier 1 (Partial) to Tier 4 (Adaptive). Determining which Tier your organization falls into involves a selection process that incorporates key metrics for your organization. These include an organization’s threat environment, business objectives, risk management approach, cyber security policies for their supply chain, organizational resources, and legal and regulatory requirements.
Although the Implementation Tiers outlined in the Framework correspond to levels of cybersecurity posture, there is no requirement for an organization to move up to a different Tier. While organizations that are considered in the Adaptive Tier 4 will have the most robust cybersecurity plan in place, that doesnt necessarily mean that every organization can, or even should, work to achieve a Tier 4 Implementation of the Framework. The Framework recognizes that this simply isnt realistic given the varied nature of the threat landscape facing organizations, as well as organizational constraints and appetite for risk. Instead, the Tiers are meant to be used as a goal for organizations. For example, an organization may find that their current cybersecurity posture places them in the Partial category. However, that organization desires to have a more comprehensive cybersecurity strategy in place that corresponds with Tier 2 (Risk-Informed). If that organization has the resources to implement processes that correspond to Tier 2, and their cost-benefit analysis finds that the minimized risk associated with a Tier 2 implementation would be beneficial, then they would most likely begin to work towards achieving a Risk-Informed implementation of the Framework. Each of the Tiers (Partial, Risk-Informed, Repeatable, Adaptive) is tied to the integration of the risk-management strategy into an organization’s operations. The higher the Tier, the more fully cybersecurity risk management decisions are made as part of the organization as a whole. This top-down approach to cybersecurity ensures that the executive and management levels of an organization are fully integrated into organizational cybersecurity decisions, leading to organizations that are more aware of their risks and proactive in addressing them.
Framework Profile
The Framework Profile brings together the functions and elements in the Framework Core with the specific and unique situation of an organization. The Framework Profile can be thought of a roadmap for organizations. Organizations implementing the NIST Framework will develop a Current Profile and a Target Profile. The Current Profile outlines the current state of an organizations cybersecurity activities, while the Target Profile outlines the desired state of cybersecurity activities that an organization wishes to achieve. The Functions, Categories, and Subcategories determined in the Framework Core are considered alongside an organizations appetite for risk, their resources, and their business requirements to provide an outline of both the current state of an organization’s risk and their desired state of risk.
Profiles fulfill a vital function in the NIST Framework. Current Profiles allow an organization to demonstrate exactly what cybersecurity outcomes they are achieving and what their security issues or risks are given their current cybersecurity posture. Target Profiles allow an organization to determine desired cybersecurity outcomes and to formulate a risk-management strategy to achieve those outcomes over time. Profiles are helpful to organizations because it allows them to accurately compare their current cybersecurity efforts with their desired cybersecurity efforts. This can illuminate gaps in cybersecurity that may open up the organization to greater risk, and thus gives a roadmap for organizations to triage working towards specific cybersecurity outcomes based on the risk associated with them. This process of prioritizing risk and development of a cybersecurity posture is tied to an organization’s business and mission requirements, resources, and management. A second advantage of the Framework Profiles is that they allow for organizations to communicate effectively between business groups or operational areas regarding cybersecurity risks. This creates a more seamless cybersecurity environment between different levels within an organization, as well as different operational sections of an organization itself.
The NIST Framework and Enhanced Cybersecurity
For organizations looking struggling to figure out how to improve cyber security or wondering how often to audit their current cyber security, implementing the NIST Framework may prove an ideal place to start. The NIST Framework is an excellent tool that can be used by organizations of all sizes, regardless of industry, to determine their current cybersecurity posture and map out a desired cybersecurity posture. The Framework is ideal for determining gaps within your current cybersecurity efforts and creating an organizational effort to mitigate those gaps over time. The Framework can supplement existing efforts at threat identification and vulnerability management. The Framework is voluntary, meaning there is no mandated compliance with the Framework. The advantage of the voluntary nature of the Framework, combined with its ability to be flexibly implemented, allows organizations to use the Framework to enhance their current cybersecurity efforts.
The Framework is a risk-management approach to cybersecurity, which is useful both as a means of engaging all levels of an organization in cybersecurity and as a means of determining your organization’s threat landscape and appetite for risk. Although the NIST Framework was designed for public and private owners and operators of critical infrastructure, any organization can use the best practices set forth in the Framework to enhance their cybersecurity posture. For smaller organizations that lack the resources to implement the NIST Framework as a whole or in part, reliance on third-party security assessors like RSI, with experience implementing the NIST Framework, can be invaluable. While there is no requirement to adopt the NIST Framework, the advantages of doing so are numerous. The NIST Framework helps organizations identify their current cybersecurity posture, compare that with their desired cybersecurity presence, and work to mitigate gaps that pose the greatest risk to their organization specifically. The risk-management approach outlined by the NIST Framework brings the executive and management levels of an organization into cybersecurity decisions, leading to an organization that is always mindful of cybersecurity risks and adopts a cybersecurity posture appropriate for those risks. Speak to an expert at RSI Security to find out more about how NIST have help improve your organizations security.



