With the rise of credit cards and online banking, financial theft has gradually shifted away from physical bank robberies to electronic payment fraud. Although payment cards facilitate convenient financial transactions for society, they also offer an ideal opportunity for threat actors to remotely steal a person’s identity or breach a companys information database. While all cybersecurity solutions are important, we want to first dive into how to increase your security across the payment card industry.
Understanding this high risk, the Payment Card Industry Security Standards Council (PCI SSC) formulated the PCI Data Security Standards (PCI DSS), composed of 12 requirements designed to mitigate customer/company information vulnerability. The first requirement focuses on ensuring a strong firewall configuration. Unfortunately, firewall security is sometimes neglected when companies favor speed over security. However, deploying a strong firewall configuration to protect the Cardholder Data Environment (CDE) is crucial. Check out this article to learn more about PCI firewall requirements.
Download Our PCI DSS Checklist
The Goal behind the Requirements
The PCI SSC serves as a global forum exploring the threats and solutions within the payment card industry. In addition to encouraging open dialogue, the council also provides resources for assessing and improving systems, processes, and physical security.
American Express, Discover Financial Services, JCB International, Mastercard, and Visa Inc. are the founding members of the council and hold themselves, as much as the vendors and software developers, to the PCI standards. Furthermore, the council encourages banks, processors, developers, and point-of-sale vendors to provide input on any PCI data security standard modifications or additions. With industry-wide and international input, the PCI SSC hopes to bolster security for the physical and electronic payment security environment; however, this goal only achieves its fullest potential if every applicable company strives to achieve PCI DSS compliance.
Assess your PCI compliance
PCI DSS Requirements Summary
The PCI DSS guidelines apply to all entities that store, process, or transmit cardholder data and/or sensitive authentication data. This includes merchants, service providers, and financial institutions across the globe. The guidelines span many sectors of the industry from point-of-sale devices to paper storage systems to remote connections. Below is a quick explanation of each PCI DSS requirement to provide a foundation before more closely examining firewall compliance the first requirement.
- Firewalls:PCI DSS requires compliant entities to implement firewalls at any internet connection and between any demilitarized zones (DMZs). The PCI SSC defines firewalls as devices that control computer traffic allowed into and out of an organization’s network and into sensitive areas within its internal network. Basically, it is a gatekeeper for inbound and outbound traffic. Requirement one encompasses not only network flow, but also any devices involved in Internet connection, such as routers.
- Secure PINs and Passwords: Although most devices come with pre-set passwords, it is vital to change them before any device connects to public networks. Pre-set passwords are easily obtained (e.g., device manual) and generally designed for convenient configuration, not security. NIST recommends 16-64 character passwords when possible, using a variety of symbols, numbers, and letters.
- Protect Cardholder Data:This requirement focuses on how data is stored. According to PCI SSC, the best option for merchants involves avoiding any data storage. If, however, a company has a legitimate need to store card data, the PCI standard permits only the storage of a primary account number (PAN), expiration date, service code, or cardholder name. Additionally, PCI compliance requires that entry devices and application be certified devices.
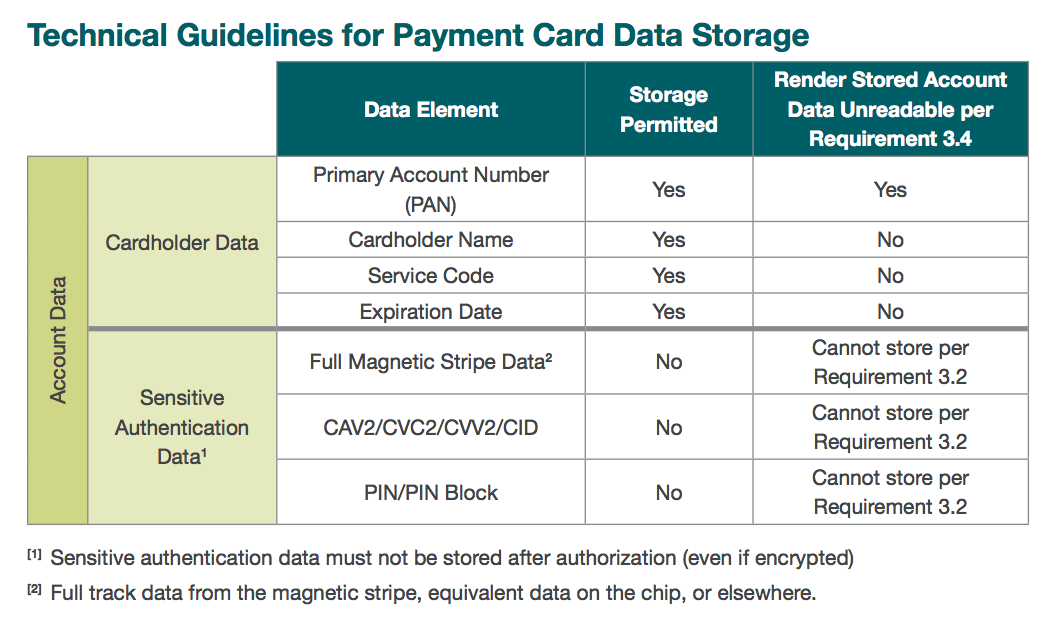
- Encryption:Cardholder data must be encrypted while in a transfer, especially over public networks. PCI standards recommend SSL/TLS, SSH or IPSec security protocols.
- Updates:In order to mitigate the infiltration of malicious software, PCI standards require companies to actively update all network device software in a timely manner.
- Assessment Processes:Companies must develop a unique plan for implementing security measures, both physical and technical. Documentation is also a key component, allowing for outside assessment and internal review.
- Access:Restrict access to the system and any premise storing cardholder data. Only personnel or outside entities classified as need-to-know should have access. Additionally, it is important to periodically review who is categorized as need-to-know. New employees or projects will dictate who still needs access and who does not.
- Authentication: PCI standards require each individual or entity accessing cardholder data to utilize a unique ID and Personal Identification Number (PIN). This is considered two-factor authentication. If a breach occurs, and detailed logs were kept, the attack point of origin may be easier to identify with such IDs in place. To aid in the process, the PCI SSC outlined PIN Transaction Security (PTS) and Point of Interaction (POI) standards.
- Restriction: Restricting physical access to facilities, devices, and networks storing cardholder data is vital. Additionally, if a device provides access but does not actually store any cardholder data, it is still beneficial to limit access. The primary goal of this requirement focuses on preventing threat actors from physically obtaining Sensitive Authentication Data (SAD).
- Monitor: Regularly monitor and fix vulnerabilities. PCI compliance requires closely reviewing logs, system components, and policy adherence.
- Test: Test old and new software using vulnerability scans, both internally and externally. After passing the first PCI compliance test, entities must then complete external testing scans on a quarterly basis; these external scans can only be conducted by Approved Scanning Vendors (ASV).
- Policy: Implement a policy for information security controls and procedures and create an incident response plan. Make sure to distribute the security policy and educate employees on how to utilize any related platforms/alert systems.
PCI Compliance Firewall Requirements
Firewall compliance encompasses both technical specifications (requirement 1) and, to some extent, physical access (requirement 9).
From a technical standpoint: PCI SSC recommends formulating standards for firewall and router implementation. This includes a plan for any future updates or reconfiguration. The plan must detail points of connection, technical specifications, and the justification behind the specified security methods. Firewalls must limit inbound network traffic to only necessary traffic (i.e., what the CDE requires for functionality). They must extend across all sectors of an entity including data repositories, public, and private devices.
From a physical standpoint:Even with a strong firewall, companies must limit physical access to the CDE. The PCI DSS details sub-requirements for securing any cardholder data environment and/or device. Inspect card reading devices for tampering, as card skimmers or other devices may have been installed to steal cardholder data. It is also advised to install monitoring devices (e.g., security cameras) and frequently review the logs. Additionally, secure entry points of CDEs by confirming that any individual entering the premises containing cardholder data receives a unique ID (i.e., easier to trace movement). Verify visitors have been granted authorized access (e.g., visitor badge) and keep a visitor log. Lastly, completely dispose of information when it is no longer needed.
PCI Firewall Review Checklist
Although it’s impossible to completely safeguard the CDE, certain firewall measures will significantly minimize security risk. Follow the five steps below to begin PCI DSS compliance.
- Implementation – Firewalls operate by receiving instructions from underlying rules. The goal of the rule and the order in which it occurs in the firewall execution list will determine efficiency. Consider which rules are used most often (i.e., what needs to be blocked most frequently) and put those rules first. Taking the time to analyze rule order will maximize speed.
- Testing – Firewalls are not foolproof; even an out-of-date firewall can pose a significant risk to a company. Consequently, entities must actively test firewalls. This may be handled internally or contracted out to white hats. Either way, the goal is to find vulnerabilities before threat actors exploit them. If a vulnerability surfaces, it is vital to patch the security hole immediately.
- Verify Operations Sometimes inquiries and rules do not execute properly. Rather than discovering a malfunctioning rule via a data breach, PCI compliant entities should actively verify that the rules work and continually update them as needed. As additional precautions, eSecurityPlanet recommends documenting the purpose of each rule, the implementation period (if it is a temporary rule), and who created the rule.
- Monitor Keep a close eye on irregularities in firewall traffic. Using built-in firewall reporting tools will ease the task of self-auditing. Look for suspicious incoming or outgoing transmissions. Make sure to investigate even the smallest anomaly as it may be an indicator of a larger security breach (e.g., malware or worm infiltration). The more frequent the monitoring, the more likely an entity will minimize the damage of a system breach.
- Update/Assess Although it is a constantly repeated point, companies must update software as soon as patches release. Gartner reported that 99 percent of firewall breaches occurred as a result of faulty configuration (e.g., failure to update). The massive Equifax breach of 2017 resulted from a failure to update a web-application in a timely manner. In addition to updates, PCI compliant entities would benefit from self-auditing; this involves compiling all the above steps and analyzing what worked and what did not. Additionally, any discoveries from self-auditing should be disseminated to business leaders, as a clear line of communication will aid in allocating security resources.
Other Firewall Tips: If firewall performance still significantly slows down operations, eSecurityPlanet notes transferring some traffic-blocking to routers may alleviate a rule overload; however, such a set-up would require additional monitoring and testing.
Firewall Security for the Cloud
As more companies turn to cloud-based services, especially Software-as-a-Service (SaaS) applications, it is important to make sure security measures expand to include such platforms. PCI DSS compliance requirements do extend to cloud environments storing cardholder data, particularly how businesses and customers use the cloud platform. Consequently, firewall planning must also take into account any cloud-based platforms storing or allowing access to cardholder data.
Cloud firewalls protect either networks/users or the cloud’s infrastructure and servers. Protecting networks and users often takes the form of SaaS, Security-as-a-Service (SECaaS), or Firewall-as-a-Service (FWaaS). The other type of cloud firewalls focuses on protecting the inbound and outbound traffic transmitted between applications via the cloud Platform-as-a-Service (PaaS) or Infrastructure-as-a-Service(IaaS). The major difference is that one cloud firewall is operated more internally (i.e., on the premises) and the other runs in cloud applications.
FWaaS or SaaS are typically offered by telecom providers and then configured (e.g., create dashboard) by the paying entity. One benefit of a provided firewall includes ease of travel easily securing remote employee devices. Furthermore, a provided firewall somewhat shields a company from debilitating DDoS attacks. However, it also means companies must trust the standards of the firewall provider. If using these firewall systems, it is important to make sure the provider is PCI DSS compliant or that the setup process adheres to PCI security standards. Additionally, if a third-party provides FWaaS or SaaS, additional review must be taken.
In contrast, IaaS and PaaS require virtual firewalls, as companies are renting a platform. A virtual firewall refers to licensed firewall applications, either added to a virtual machine (VM) or packaged with the VM. Virtual firewalls allow for extremely quick modifications and an easier configuration process. However, security precautions with IaaS and PaaS lie with the user/company. Basic cloud security is not enough protection; entities must install additional virtual firewalls for maximum protection.

Security Compliance
Overall, security compliance relies on the implementation of all the aforementioned security precautions in the CDE. Going step by step and taking the time to make sure security measures are properly configured will help entities successfully achieve PCI DSS compliance. To help with this process, just keep three steps in mind:
- Assess
Internal security scans may be conducted by an internal review or by utilizing a thoroughly vetted security contracting company. For external security scans, an ASV must be hired. ASVs are approved by the PCI SSC and scan customers/vendors to make sure they are in PCI compliance. ASV services include scanning, testing tools, and reports. Remember, assessment is a process encompassing personnel, cardholder data locations, IT assets, and administrative processes, so it will take time to adequately complete this step.
- Repair
Any vulnerabilities discovered must be fixed quickly but also thoroughly. It is sometimes easy to rush a security patch to appear on top of the issue; however, a hasty patch could lead to more issues at a later time.
- Report
Document self-assessments and any external assessments. Keep a detailed list of business partners or any entity that has access to cardholder data.
Reliability and trust serve as vital cornerstones in the financial industry, more specifically for PCI. For financial institutions, vendors, and merchants, PCI DSS compliance helps achieve and maintain the stability of these two cornerstones. Just one misstep can undo the long process of implementing strong security measures and cause irrevocable consequences. To better understand all the PCI firewall requirements and start ensuring your company is PCI DSS compliant, contact RSI Security for a consultation today.

