RSI Security recently partnered with FortifyData on the podcast “Guardians of Cyber Galaxy: Mastering Third-Party Risk with RSI Security and FortifyData’s Shielded Solutions.” Nico Giatrelis, Senior Marketing Coordinator at RSI Security, began by introducing the speakers:
- Eric Smith, Director of Technical Services Delivery at FortifyData, leverages 20+ years of experience across industries to manage customer implementations of FortifyData’s Cyber Risk Management software and provide expert demonstrations on the platform.
- Jeff Messer, vCISO Security Assessor at RSI Security, has also amassed over 20 years of experience in cyberdefense and risk management. He applies his expertise to audits for compliance and more across telecommunications, banking, and other industries.
Eric and Jeff then began the conversation by defining the scope and stakes of third-party risk.
Understanding Third-Party Risks
Often, decision-makers operate on misconceptions about third-party risks, wondering “why do I need this” about third-party risk management (TPRM). Eric explained that they’ll point to things like a well-secured perimeter, firewalls, and vulnerability management that they have in place and wonder, given those safeguards, “why is third-party risk management important?”
But a critical point these parties often overlook is that vendor management and IT teams are out of sync when it comes to third-party environments, infrastructure, and the risks they entail.
Jeff noted here that, often, leaders are surprised by how many breaches are caused by third-party risks rather than internal misconfigurations. And Eric added that cybercriminals often think of an organization’s third parties as an extension of their attack surface. However, organizations rarely see them this way, and third-party risks are often neglected or wind up in feedback loops of sending out questionnaires, not verifying answers, and filing them away.
Instead, it’s critical to seek out and remediate third-party risks before attackers get to them.
Commenting on how the three pillars of security are often considered to be People, Process, and Technology, Jeff said that there should be two more Ps introduced: Proactive and Prepared.
Assess your Third Party Risk Management
RSI Security’s Managed Service Suite
A great practice decision-makers at any organization can take up is scanning through recent news for stories about breaches. Many will have some understanding of how their teams would react if it happened to them. But equally important are questions about what they’d do if the incident impacted one or more of their third-party vendors or other strategic partners.
That’s exactly the kind of insight RSI Security’s third-party risk assessments deliver.
Eric noted that, any time an incident occurs, a lightbulb goes off. Stakeholders always have a realization that if they only knew a certain detail, they’d have taken the right action. He joked that the two things we always wish we’d had, post-facto, are a crystal ball and a time machine.
In the absence of those fantastical tools, the next best things in the real world are continuous monitoring solutions that allow for a constant eyeball on everything going on. And, even more importantly, you need to approach that data with active analysis. Just generating endless amounts of data about third-party risks is not enough; you need to empower action.
Jeff talked about how important RSI Security’s additional support is to the success of supplier risk assessment. RSI Security’s experts provide guidance beyond the portal and platform, working with internal teams to understand and mobilize assessments. Whether through resource augmentation or regular meetings, we help you get the most out of your scans.

The Benefits of Collaborating with FortifyData
One of the most beneficial elements of RSI Security’s collaboration with FortifyData is that it powers flexible, continuous monitoring of third-party risks. That starts with scalability, giving organizations the option to start with just a handful of their vendors rather than all at once.
Jeff talked about the possibility of starting from true brass tacks, looking at the vendor risk assessment questionnaires provided to the most critical third parties. RSI Security helps organizations identify which entities are most critical by digging into questions about what would happen if they were compromised. Then, RSI Security also helps generate questionnaires, if there isn’t one in place, or customize and tailor any existing questions to provide actionable insights in an efficient, timely manner—whether it’s weekly, monthly, or at other intervals.
Effective vendor risk assessment starts with effective scoping or assigning vendors into tiers:
- Uber-critical – These are vendors, suppliers, and other third parties for whom, if something were to happen, it would put your organization at dire risk immediately.
- Mid-tier – These third parties carry moderate levels of risk; they may not require the same level of scrutiny, but they should be addressed after the prior group is exhausted.
- Other folks – These are low-stakes third parties (i.e., coffee suppliers) who may not need coverage. However, some risks are always present if they have physical access.
Eric noted that, especially at first, you don’t need to approach every vendor with the same level of care. Often, organizations are stuck with an overwhelming amount of data and lack a sense of direction about what to address. A big factor here is lapses in communication between vendor management and IT teams, where the latter is often not updated on vendors that are being on or off-boarded, which leads to the former lacking information about risks inherent to them.
Working together, RSI Security and FortifyData simplify the supplier risk assessment process, making actionable insights more readily available and easy to understand across all parties.
FortifyData’s Third-Party Risk Dashboard
One of the specific tools that power FortifyData’s insights (and, by extension, RSI Security’s TPRM services) is the innovative Third-Party Risk Dashboard. It allows organizations to see where vendors fall in terms of priority at a glance, along with several other functionalities.
Namely, the dashboard empowers a high-level overview of all third parties in an organization’s IT environment, along with details about them. The dashboard’s visualization options include:
- Breaking down third parties into scoring bands to see where each (or a group) falls
- Displaying third parties on a heat map to signify the relative importance of each’s risks
- Enabling a tile-based interface to monitor select, granular details across all parties
- Restricting access to select portions of the dashboard based on a stakeholder’s role
- Populating detailed information about new vulnerabilities in real time as they emerge
- Cross-referencing against applicable regulatory compliance standards and rulesets
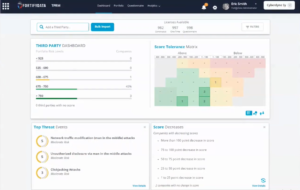
These are just some of the features that make the FortifyData dashboard impactful; another element operating on the backend is how it populates through a dynamic fillable form system.
Eric talked about how he takes great pride in the FortifyData platform because he was involved in designing its core function, which is removing agonizing back-and-forths and unintelligible spreadsheets from the TPRM equation. Instead, organizations get the information they need from vendors through a seamless validation system. Third parties are sent a link where they fill out the data about their dark web vulnerabilities, breach histories, exposures, etc., which is fully verifiable within the platform. Best of all, evidentiary documents submitted always stay with the specific questions to which they relate, removing confusion about file misplacement or illegibility.
Given the importance of third-party risk management, making document tracking and verification as easy as possible is a win-win for all parties. Eric stressed the value this system brings to organizations and their partners: “If their security improves, your security improves.”

Optimize Your Third-Party Risk Management
Closing out, Nico thanked Eric and Jeff for participating. He also thanked the audience for their attention and encouraged listeners to reach out for more information about RSI Security’s and FortifyData’s third-party risk assessment and overall third-party risk management solutions.
FortifyData is a cyber risk management company that facilitates automated cybersecurity threat assessments to manage cyber risk across an organization. Combining attack surface audits, asset classification, and more, FortifyData offers an all-in-one cyber risk management platform.
RSI Security is a premier managed security service provider (MSSP) offering comprehensive cyberdefense services. Our subject matter experts cover fields including but not limited to data privacy regulatory compliance, penetration testing, and threat and vulnerability management.
To learn more about our third-party risk management services with FortifyData, check out the podcast—or schedule a consultation to learn how we can help you rethink your security.
