Technological theft, espionage, “a threat to national security” – terms that are becoming all too familiar to the Department of Defence (DoD). In recent years with the increasing turbulence of cyberattacks, the DoD has been looking toward a more stringent compliance framework to quell the fires of cyberattacks along the Defence Industry Base (DIB) supply chain.
Enter the Cybersecurity Maturity Model Certification (CMMC).
For contractors that engage with the DoD, the CMMC is the new standard to abide by. In this article, we will discuss the Do’s and Don’ts of CMMC, but first a brief introduction to the model.
What is the CMMC?
The cybersecurity maturity model certification, is a cyber maturity assessment framework that aims to measure the overall cybersecurity maturity of an organization. The CMMC is replacing the current self-certification to the NIST 800-171 framework. Certification will now require a third party assessment audit from a Certified Third-Party Assessment Organization (C3PAO).
The model, and consequently the maturity, is measured on a 5 level basis. The levels range from “basic cyber hygiene” (level one) to “advanced cyber hygiene” (level 5). Compliance to the model is dependent on what DoD information your organization processes. Level 1 deals with federal contracts, and level 3 and above means your organization is processing controlled unclassified information (CUI); this will decide what level of maturity your organization must attain.
The security maturity assessment, within the model, is gauged by the organization’s implementation of the practices and the integration of the processes outlined by the model.
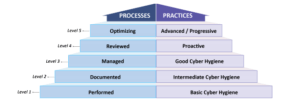
Image Source: Cybersecurity Maturity Model Certification (CMMC) Version 1.0, January 30, 2020, Page 4.
The model builds upon the NIST 800-171 and Defense Federal Acquisition Regulation Supplement (DFARS), so prior knowledge or self-certification to the NIST framework is a bonus, as a majority of the practices are taken from the framework. If you wish to learn about the model in greater detail, check out some of the articles on our blog.
But what are the Do’s and Don’ts to CMMC certification, let’s discuss.
Certified Third-Party Assessment Organization (C3PAO)
Do employ the services of a certified third-party assessment organization. Due to the nature of the new standard, engaging in business with the DoD now requires that a third-party conduct an audit of your organization concerning the implementation of the model as a whole. In the same vein, Do lookout for an organization that has C3PAO and specializes in cybersecurity services to ensure the best outcome.
Don’t self-certify using the NIST 800-171 framework. This will no longer be viable as the new standard requires C3PAO, as mentioned above. As the model is not in effect yet (at the time of writing this article), it would be prudent, and required, to continue NIST 800-171 self-certification until then.
Maturity Level
Do find out at what maturity level your organization wishes, or should, comply with. Finding out what kind of data you process along the DoD supply chain is a vital step. Is your organization simply processing federal contracts, or are they involved with controlled unclassified information? These types of questions will help you assess the appropriate level your organization should comply with, and potentially save a lot of time and resources.
In essence, you should be taking a data inventory of all potentially sensitive information that is being processed, along with regulations your industry might be beholden to, as this may also affect the level of maturity. When you have discovered what level your organization is aiming to comply with, the next step would be to begin integrating the process within the organizational culture.
Download our CMMC Whitepaper: Best Cybersecurity Practices for DoD Contractors
The process element within the model can demonstrate to the DoD, and subsequently the auditor, the level to which your organization has “institutionalized” the cybersecurity practices. By “institutionalized” the CMMC refers to how ingrained the practices have become. Is the organization operating at a level where the practices have become second nature to the business and the personnel operating within it? Or are they just a loose set of rules that are haphazardly followed.
In the latter case, it is unlikely any C3PAO will approve certification, so do make sure all levels of the organization are involved with the process, which brings us to the next point: don’t neglect your homework.
Read up on the model as a whole, do some research on the practices and the process. Even if the model seems complex, it is better to know something than nothing at all. A C3PAO can help you achieve compliance faster and more efficiently if you do some house cleaning first. Remember, they are there to help, not fight you.
Staff and Personnel
One aspect of the maturity model that you certainly do want to have in order is to have the organization’s staff and personnel involved in the process. An organization is formed and maintained by the people who run it, this is why, if you wish to have a security-conscious organization, you must have security-conscious people.
To institutionalize the models’ processes within the organization, there is a heavy reliance on the staff and personnel within the structure to adopt the security process into their daily activities. This ensures maximum effectiveness of the process, and, depending on the maturity level, it could be more or less involved.
In this case, do invest the resources necessary for adequate staff training. An often overlooked part of an organization’s cybersecurity architecture is how well do the staff practice cybersecurity awareness?
Your organization can invest a significant sum into implementing top of the line software and hardware, spend the resources for all the security configs on the market, and it could all mean nothing if an employee unwittingly gives away the keys to the castle. As mentioned previously, the foundation of an organization is the people, so do make sure the people want to maintain the security of the organization.
Conversely, don’t ignore the needs of your staff, it can be a challenging process managing a large or even small organization. Balancing the needs of your personnel and the responsibilities of the organization can lead to tricky situations, especially when something new is introduced to the organizational structure. Ensure that the staff is involved in the cyber maturity assessment framework, that way the processes within the model can become institutionalized.
General Cybersecurity Principles
Now that we have discussed specific areas and briefly addressed the do’s and don’ts, in the next section we will explore some general cybersecurity principles that should be known when looking to certify.
Keep in mind that these principles need not only apply to the CMMC, but are regarded by the wider cybersecurity community as essential practices.

Passwords
Passwords are the bare minimum for any secure network. Within the CMMC model it is no different, but not any old password will do.
Don’t use easily guessable passwords or PINs, you might be surprised to find out that one of the most common passwords in the world is simply 1234. Using this password for any system is not recommended and will certainly see your organization fail at attaining certification, or passing any cyber maturity assessment framework for that matter. Similarly, do not use default passwords.
Do use two-factor authentication and temporary passwords, this will double down on password security and demonstrate a willingness to any assessor. Also, ensure that all terminals and devices are locked when not in use and that they are password protected.
Accounts
The next big thing after passwords are accounts. This is, generally, meaning all sorts of accounts management.
Don’t use account sharing, do make sure each employee has his/her account. This might not seem obvious at first, but if multiple people know the passwords to a single account, if a data leak occurs, it would be difficult to determine the source of the leak if it was due to the account in question.
Under the same account bracket, do ensure that each account is checked for administrative privileges. Don’t give all accounts admin privileges, make sure you control the use of those privileges so only authorized accounts have admin privileges.
Cloud sharing Accounts
The cloud has increasingly become a staple for any business operating over the internet. Misuse of cloud accounts has also become a headache for the DoD. If your organization does use a cloud sharing platform, do make sure that document sharing has not been set to public, and the organizational accounts use strong password protections. Don’t allow employees to share documents outside the parameters of the organization’s network.
Software
The general use of software such as apps, operating systems, etc. is now a given within the daily activities of a business. A lot of the software used and bought rarely comes configured with security in mind, this can cause long term exploitable problems for the organization. With software being such a big topic here is a list of do’s and don’t when it comes to CMMC cyber maturity assessment framework.
Do’s:
- Apply security configuration to all apps and operating systems (default configs are insecure).
- Install updates to any app, operating system, etc. that is being utilized by the organization.
- Enable, install, patch anti-(virus, spyware, malware) on all devices.
- Use a firewall configured to limit access (communications coming from) the internet.
- Use audit logs and security incident and events management (SIEM) software to better understand the security environment of your network.
Don’ts
- Don’t use unsupported apps or operating systems (i.e the vendor no longer supports the software, and is not looking to update security vulnerabilities, an example of this would be Windows XP).
- Don’t try to self-host, if your organization does not have the resources or capacity to host an app or software on its servers it could compromise the entire organization. It is best to leave this to a third party who has the resources, dedication, and specialty to offer such services.
- Don’t leave updating to the last minute, often an emergency patch or update is released due to security issues found within the software. If you don’t have Auto-updates enabled, then you must manually update the software in a timely manner or attackers might be able to exploit the vulnerability before the update goes through.
Hardware and Physical Protection
Hardware assets and physical locations, documents, etc. must be protected. Physical protection, more so than hardware security, is an often overlooked aspect of cybersecurity but much like all the other general cybersecurity principles, it forms an integral part of the overall cybersecurity architecture.
The CMMC also places an important emphasis on physical protection as it forms one of the 17 domains, your organization mustn’t overlook this aspect.
Here is a list of do’s and don’ts of hardware and physical protection.
Do’s:
- Use public and private spaces within the physical location of the organization. Section off a private space for employees and personnel so that only authorized people have access to the devices and computers in that area, ensuring that this area is where the majority of the work is done.
- Utilize a keycard system if your organization can afford to do so. This kind of system also integrates a logging system so you can see who enters and leaves certain areas.
- Keep computer use limited to 1 person per terminal/device. Use company policy to ensure that only the authorized person is allowed near or logged on to the computer.
- Shred before disposing of all documents that are no longer needed, regardless of whether it contains sensitive information on it or not (in the business we call this “sanitize”). This method creates “noise” for any would-be attacker sifting through disposed documents (A method employed by attackers known as dumpster diving).
- Restrict who has access to the keys or access devices. Allow only select authorized individuals to have the ability to unlock doors and storage areas.
Don’ts
- Don’t allow access to any visitor, ensure that they are supervised during the visit. Check that the visitor is genuine.
- Don’t throw documentation without sanitizing it first.
- Don’t forget to change locks and access keycards, after an employee has left the organization.
- Don’t leave windows unlocked overnight.
- Don’t allow personnel to take certain hardware assets home without strict company policy ensuring that it is done securely.
- Don’t allow employees to use personal devices on the company network, set up a public wifi for recreational use, and don’t allow company devices to connect to said network.
Key Takeaways
The CMMC is now a requirement for any organization that engages with the DoD. This new standard must be certified by a third party (C3PAO). This does not mean it has to be a difficult process to attain certification. What it does mean is that the cybersecurity process has to become “institutionalized”; meaning it is fully integrated within the culture of the organization.
In this article, we have outlined some general do’s and don’ts pertinent to specific areas within the cyber maturity assessment framework and with general cybersecurity principles. This should jump-start the processes toward certification and give your organization a general guideline.
Be sure to employ the skills at RSI Security to get the best cybersecurity service. Whether it be full-stack cybersecurity architecture implementation or compliance service we are here to help, book a free consultation today!
