Many different auditing processes exist, and companies increasingly face the challenge of choosing which type to conduct. Consumers and business partners demand data protection, so it is vital that companies understand the differences of each auditing process available. Are you aware of the Soc 2 compliance requirements? Find out how to be compliant from the experts at RSI Security.
What is SOC 2?
At its most basic, SOC 2 (System and Organizational Control) is an auditing process targeting inter-business relationships, not business-to-consumer relationships. SOC 2 principles focus on service organizations. The American Institute of Certified Public Accountants (AICPA) defines a service organization as:
The entity (or segment of an entity) that provides services to a user organization that is part of the user organization’s information system.
Here are a few more articles to help you learn more about SOC 2 :
Many of the security aspects SOC 2 addresses involves external interactions that could affect internal or customer data security. The AICPA developed SOC 2 as a way to encourage the implementation and oversight of proper security procedures. Similar to other security guidelines, SOC 2 outlines a basic structure for security measures, but then allows companies to customize those basic measures to their needs. This contrasts the more strict guidelines of the Payment Card Industry Data Security Standard (PCI DSS).
Assess your SOC 2 compliance
Report Types
SOC 2 is just one of three types. SOCs 1 and 3 also exist, but they each serve a different purpose. This sometimes makes report selection difficult for companies. A SOC 1 report is equivalent to a Statement on Standards for Attestation Engagements (SSAE 16) report. If a company’s operations can impact Internal Controls over Financial Reporting (ICFR), then it should conduct a SOC 1 report. ICFR is a process designed to provide reasonable assurance regarding the reliability of financial reporting and the preparation of financial statements for external purposes in accordance with generally accepted accounting principles.
Unlike SOC 1 reports, a SOC 2 report focuses on the five Trust Service Criteria (TSC) principles: security, availability, processing integrity, confidentiality, and privacy. As noted above, companies use these principles to assure their business partners and service organizations that proper security procedures are in place. A SOC 3 report is very similar to a SOC 2 report but differs in that it can be publicly distributed and provides fewer details.

Report Subcategories
Within SOC 2 there are two varieties of reports: Type 1 and Type 2. A type 1 report focuses on the Trust Services Criteria (TSC) a company chooses to use and other controls in place to mitigate security risks. A type 1 report reviews security controls based on a specified point in time (e.g., January 1). A type 2 report details how those controls are structured and implemented over a period of time (e.g., 6 months). All these categories may sound confusing, but CyberGuardian Compliance recommends the following trick to remember what each category involves:.
SOC = Scope
- SOC 1
- SOC 2
- SOC 3
Type = Time
- Type 1
- Type 2
Components of the Trust Service Criteria
Unlike a SOC 1 report which focuses more heavily on financial controls, the TSC principles, as noted above, are key aspects of a SOC 2 report. To ensure SOC 2 compliance, companies must analyze the following five principles and consider how they relate to current company operations.
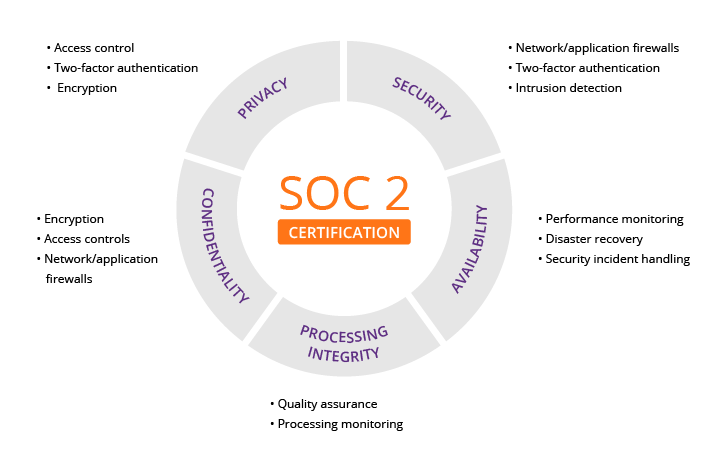
- Security: The security section of a SOC 2 audit examines both the physical and electronic forms of security in use. Are systems protected from unauthorized access, and are there controls in place to alert enterprises of any suspicious activity?
- Availability: Are clients able to access the system as per contractual specifications?
- Processing Integrity: If a company offers financial or e-commerce transactions, audit reports should include details on controls designed to safeguard transactions. For example, is a monetary transfer via a mobile device completed in an encrypted session? This also refers to services that are marketed to clients or services that are supposed to be available to service organizations. For example, are clients granted access to a data repository or hosting platform?
- Confidentiality: Are there any restrictions on how data is shared? For example, if companies have specific guidelines for dealing with Personally Identifiable Information (PII) or Protected Health Information (PHI), they should include them in audit documentation. Include how data is stored, transferred, and accessed as well as adherence procedures for privacy policies (e.g., employee procedures). The more detail the better.
- Privacy: Privacy, unlike confidentiality, focuses on how a company collects and uses customer information. A company’s privacy policy must align with actual operational procedures. For example, if a company claims it alerts customers every time it collects data, audit materials should explain how this is done (e.g., is there a pop-up message alerting users?). Privacy controls should, at a minimum, follow the AICPA’s Generally Accepted Privacy Principles (GAPP).
The graphic below details several different considerations relevant to each of the five principles:
What Are the Generally Accepted Privacy Principles (GAPP)?
The AICPA and the Canadian Institute of Chartered Accountants (CICA) designed the GAPP as a global privacy framework to help organizations create an effective privacy program that addresses privacy risks, obligations, and business opportunities. The following 10 principles are based on globally recognized good practices. For more complex principles, like management and information disposal, the AICPA provides more in-depth recommendations.
- Management: The entity should define, document, communicate, and assign accountability for its privacy policies and procedures. Consider taking a personal information survey to identify what information is being collected and how it is stored. Such a survey should specify who collects the information. Is collection done by a live person (and from which department) or an algorithm. In an age where information overload can result in less efficiency and security breaches, a survey helps managers determine if an excess or insufficient amount of data is collected.
Sample Survey:
- What PII is collected and why is it collected?
- What is the source of the PII (e.g., third party or direct from customer)?
- Which department collects the information?
- Which department uses the information?
- Who has access to the PII?
- Is the PII provided to external businesses (if yes, why)?
- Is only the minimum amount of PII (i.e., what is needed to fulfill a requirement/complete a task) disclosed?
- Notice – an entity should provide notice about its privacy policies and procedures and identify the purposes for which personal information is collected, used, retained and disclosed. Customers/service organizations want to know why their information is required, how it is used, and how long the company will retain the information. If a company does not need to store information for more than a week, then policies (see #5) should ensure that the information is properly removed from the system after that designated time period. The goal is to minimize a glut of unneeded data.
- Choice and consent – The entity describes the choices available to the individual and obtains implicit or explicit consent with respect to the collection, use and disclosure of personal information.
- Collection – The entity collects personal information only for the purposes identified in the notice.
- Use, retention, and disposal – The entity should limit the use of personal information to the purposes identified in the notice and for which the individual has provided implicit or explicit consent. Make sure information is utilized only in the manner specified by the privacy policy. Likewise, once information is no longer needed, dispose of it. Factors for retention periods include: current activities, access requests, legal/regulatory requirements, benefit of storing information, collection purpose, customer authentication requirements, potential legal risks (e.g., proof), industry guidelines, and contractual obligations. Other considerations include whether the disposal process will occur on-site or off-site. The disposal process should be irreversible.
Disposal Options:
- Physically rendering information on electronic storage devices unreadable via crushing, pulverizing, etc.
- For non-disposable devices (e.g., computers, tablets, etc.) use overwriting, wiping, or deleting
- Burn or shred paper records
- Access – The entity provides individuals with access to their personal information for review and update.
- Disclosure to third parties – The entity discloses personal information to third parties only for the purposes identified in the notice and with the implicit or explicit consent of the individual.
- Security for privacy – the entity protects personal information from unauthorized access (both physical and logical). Causes of data breaches range from lost laptops to social engineering. Conducting a PII storage inventory will help identify the weakest link in your storage practices. This includes reviewing physical and electronic means of storage. For example, make sure physical files are kept in locked filing cabinets in locked rooms. Papers lying on desks are easy targets for wandering eyes. For electronic storage, the AICPA suggests using a layered approach, meaning every electronic device has several different security measures (e.g., firewalls, encryption, wireless monitoring, unique system IDs, etc.). Other storage methods to consider include USBs, hard drives, or CDs.
- Quality – The entity maintains accurate, complete and relevant personal information for the purposes identified in the notice.
- Monitoring and enforcement – The organization should monitor compliance with its privacy policies and procedures and have procedures to address privacy-related complaints and disputes.

Privacy Classifications
One of the major aspects of audits like SOC 2 is ensuring the protection of customer and company data. The AICPA suggests each company create information-classification levels. The number of tiers will depend on a company’s scale and how much information/what type is collected. For example, a minimal classification system may include three levels: Public, Business Confidential, and Secret. Public information includes products for marketing or internal procedural documents. Business Confidential information would include basic customer information and should be protected with at least moderate security controls. Secret information would include highly sensitive PII, such as a Social Security Number (SSN) or bank account number.
In conjunction with information classification levels, a company should have an information request process and designations for personal access levels. For example, if an employee from PR or the Marketing team needs statistics on customers, that information would likely be classified under Business Confidential and only require a mid-level security authorization. Utilizing a request system will enable information sharing while minimizing the risk of “excessive” access (i.e., given more information than necessary to complete a task).
What Will Be Included in a SOC 2 Report?
So what’s the end result of all this hard work? After completing the compliance process, companies receive a report that verifies their efforts toward minimizing security risks. The following list provides a brief summarization of the seven-part report.
- The Assertion Report details a company’s security controls in relation to the six TSC.
- The Independent Auditor’s Report explains how effective auditors deemed the controls in place.
- The System Overview Report explains how service organizations interact with the company in question.
- The Infrastructure Report details all aspects of company operations — from employees to software to security procedures.
- The Relevant Aspects of Control Report analyzes how the risk assessment was conducted, the effectiveness of communication procedures, and the monitoring controls in place to track security systems/usage.
- The Complementary User-Entity Controls Report outlines the security protocols protecting the user environment (or the platform shared with a service organization).
- The Test of Controls Report analyzes how the controls performed after testing and verifies if the auditor found the controls effective enough to meet the TSC.
Audit Dissemination
Again, it’s worth noting that distribution of a SOC 2 report is limited in comparison with a SOC 3 report. SOC 2 reports may be distributed to user organizations involved with your company as a means of security assurance. However, companies cannot share SOC 2 reports with the general public. To reassure the public that proper procedures are in place, a SOC 3 report must be completed and subsequently distributed.

Need Help?
Audits simulate a trail, allowing companies to go forward but always have a record of their past actions. This “trail” acts as a safety net (in legal cases) and a means of strengthening trust between customers and businesses. If the process of auditing seems overwhelming, don’t worry! Many companies find it difficult to navigate the complex world of auditing. To learn more about SOC 2 compliance or receive help overhauling your current auditing process, contact RSI Security today.
Speak with a SOC 2 compliance expert today – Schedule a free consultation