Auditing laws cover various topics and industries from social media privacy to financial transactions. Each auditing process targets different weaknesses in order to tackle the risks that accompany technological advancements. In particular, the multi-faceted Sarbanes-Oxley Act (SOX) deals with corporate operations and publicly traded companies. The 404 section requirement addresses financial documentation.
Are you aware of the SOX 404 requirements? Find out everything you need to know about compliance with our comprehensive guide.
An Overview of SOX
The SOX Act, passed in 2002, affects all companies, regardless of industry. It addresses corporate governance and financial practices with a particular focus on records. SOX includes 11 titles with the primary audit-related sections being 302, 401, 404, 409, and 802. Although this article mainly covers section 404, below is a brief summary of each main section:
- 302 – Requires periodic statutory financial reports. The reports must present an honest accounting of a firm’s financial stability, any fraud incidents, ineffective control methods, and changes/improvements to internal controls.
- 401 – Addresses full financial disclosures, including liabilities, transactions, and accounting practices.
- 404 – Analyzes internal controls and financial reporting procedures.
- 409 – Requires companies to inform the public of changes in financial operations or significant changes in the company’s financial position.
- 802 – Addresses fraudulent documentation (e.g., falsifying records) and consequent penalties.
SOX and Security Procedures
While all of the above sections review financial operations and documentation, companies should already have strong security procedures in place. The goal of audits like SOX is to assess these controls; however, if a company lacks major internal controls, the audit process will be less beneficial. Furthermore, if overall company security is weak, financial operations will also be weakened. Good security controls will maintain data integrity in collection, transfer, and storage. Utilizing systems that categorize and tag data will help regulate and organize internal and consumer data.
Assess your SOX 404 compliance
What Are Internal Controls?
According to the Federal Deposit Insurance Corporation (FDIC), internal controls:
Include the policies and procedures that financial institutions establish to reduce risks and ensure they meet operating, reporting, and compliance objectives.
But why are they so important? Internal controls safeguard company assets, maintain the integrity of financial data/transactions, ensure compliance, support daily operations, and assist companies in achieving their objectives. The controls may be electronic or physical in nature. For example, physical controls may be the segregation of duties.
The fewer people/processes involved in a financial transaction, the lower the risk level. Electronic controls range from simple two-factor authentication to complex algorithms monitoring computer systems for suspicious activity. For more information, the FDIC provides a comprehensive list of internal routines and controls.

Sox 404 Specifications
This section requires that:
“All annual financial reports must include an Internal Control Report stating that management is responsible for an ‘adequate’ internal control structure, and an assessment by management of the effectiveness of the control structure.”
Basically, the section addresses auditor attestation or verifying the auditing process was completed thoroughly. Section 404 of the act requires an auditor to attest and report on a company’s assessment of its internal controls. This process allows an “outsider” to look at internal operations/reviews from an objective perspective. The 404 clause increases transparency, particularly regarding financial reporting. Furthermore, it focuses on the likelihood of material misstatements. Although SOX 404 increases auditing costs, many experts believe the information and insights the audit provides for investors is well worth the extra expense.
Exemptions
Realizing the cost of auditing is too much for some companies, the SEC does not require non-accelerated filers or companies with less than USD 75 million in public float [i.e., the portion of shares held by public investors] to comply with section 404. The exemption also encompasses Emerging Growth Companies (EGCs) for up to a five year period.
Although not yet passed, in early 2019, a group of senators proposed a new bill focusing on Emerging Growth Companies (EGCs). The new bill relates to companies that have issued an IPO but are still earning low revenues. If passed, the bill would provide another five-year extension for companies that “earn annual average revenue of less than USD 50 million and less than USD 700 million in public float.”
Control Management
Out of all the SOX specifications, the control testing process will likely cost the most in terms of both time and money, but in the end, it is well worth it. The following points summarize a skeletal structure for assessing controls, but each company will have to adapt them to its particular needs.
- To start, create a list of currently in-use security controls. With each security control, including information on its purpose and expected outcome. Use the five components of internal controls (see below) to begin.
- Run diagnostic tests to determine if expected outcomes are met.
- Document the process and actual outcomes. As with most auditing, the more documentation the better. The SEC requires that companies “provide reasonable support for management’s assessment of the effectiveness of the company’s internal control over financial reporting.”
- Review the findings to identify which controls are not functioning properly. Document any deficiencies.
- Adjust controls to fix security holes/deficiencies and document those changes.
These control assessments must be done on a yearly basis and completed prior to the end of a company’s fiscal year.

The Five Components of Internal Control
When conducting risk assessments, companies should use the five components of internal control as a baseline framework. The Committee of Sponsoring Organizations of the Treadway Commission (COSO) created the five-layer model in 1992 (later updated), and it is now widely accepted as a good starting point for evaluating internal controls.
- Control Environment – The control environment encompasses the interactions between all levels within a company — from the Board of Directors to managers, to general employees. The standards and processes in place serve as the foundation for the other components of control management. The environmental framework should detail the chain of authority and be a reflection of a company’s core values.
- Risk Assessment – At its core, a risk assessment is an iterative process that examines threats to a company’s goals/operations. A thorough assessment examines operations, reporting, and compliance. Companies should repeat and tweak risk assessments as their objectives evolve. Furthermore, risk assessments need not focus only on the past/present, they can also be used to assess if future changes will likely have a positive or negative impact on company operations.
- Control Activities – After understanding the threat landscape via a risk assessment, controls act like battle reinforcements, strengthening each identified weakness to mitigate or prevent a successful attack. The concept of control activities encompasses a slew of different options from manual controls to automated controls; from preventative measures to reactive procedures. For example, a simple automated control may be monitoring for multiple unsuccessful login attempts.
- Information and Communication – Information and communication are like the car and infrastructure relationship. Cars are necessary to travel or achieve objectives. But, without a good “road” system (i.e., communication channel), you can’t go anywhere, or at least not efficiently. Collecting information and monitoring activities require timely reporting and clear communication with managers. Companies should have a secure way of obtaining and disseminating information, both publicly and internally.
- Monitoring Activities – It is essential that companies have different levels of monitoring. For example, a company may have a system monitoring for malicious code. However, there should also be a monitoring process in place to evaluate if the malicious code tracker is also operating correctly. In other words, there should be macro and micro monitoring activity for electronic systems as well as internal personal interactions (e.g., are employees following security procedures?).
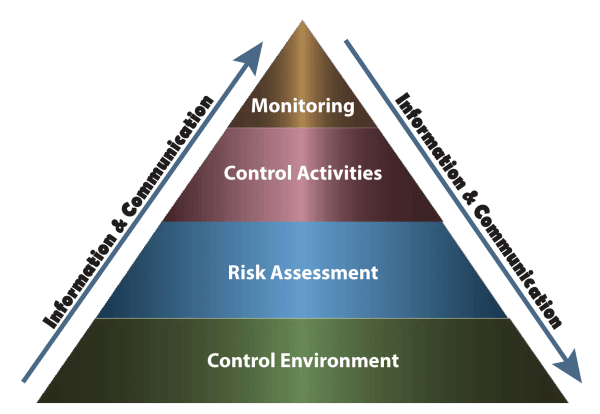
Image Source: University of North Carolina at Chapel Hill
Sox Compliance Testing & TDRA
As briefly mentioned above, a major part of the Sox 404 attestation includes a Top-Down Risk Assessment (TDRA). But what exactly is a TDRA? The TDRA approach is a step-by-step process designed to address past omission/oversights in the auditing process and prevent such oversights in the future.
More formally, the U.S. Public Company Accounting Oversight Board (PCAOB) defines [in Auditing Standard No. 5] the TDRA process as follows:
A top-down approach begins at the financial statement level and with the auditor’s understanding of the overall risks to internal control over financial reporting. The auditor then focuses on entity-level controls and works down to significant accounts and disclosures and their relevant assertions. This approach directs the auditor’s attention to accounts, disclosures, and assertions that present a reasonable possibility of material misstatement to the financial statements and related disclosures. The auditor then verifies his or her understanding of the risks in the company’s processes and selects for testing those controls that sufficiently address the assessed risk of misstatement to each relevant assertion.
Common SOX 404 Audit Mistakes
It’s easy to become overwhelmed or distracted by various tasks during the audit process. This can lead to what Norman Marks, a risk management expert, calls “scope creep” or when distractions cause management to lose focus on the two key questions of risk management: What is the risk? and Where is the risk?
Marks goes on to note five common mistakes companies make when conducting SOX audits.
- Companies tend to overestimate what qualifies as a “key controls.” If a malfunctioning control is unlikely to cause a material misstatement, then it is not a key control. In other words, companies fail to adequately rank risk levels.
- Misinterpretation SOX requires auditing only if control weaknesses could result in material errors. However, if the term “material” is misunderstood, companies can waste money and time on unnecessary review. The term “material” is not an automatic percentage of net income. It is what is important to a reasonable investor in making their buy/sell decision. SOX focuses on external reporting and less on fraud, despite the major operational threat fraud poses.
- The tendency to over-audit. It is common for companies to not differentiate between IT General Controls (ITGC) and business processing controls. Again, only those controls that could result in a financial error/misstatement must be evaluated under SOX guidelines. Lumping ITGC in with relevant SOX 404 controls increases the auditing cost and overextends the scope. For example, back-up procedures, while critical for ITGC, are unlikely to cause a material financial error. Consequently, back-up controls do not need to be evaluated for SOX compliance. Consider if a control failure results in a change in a financial statement balance that is material and unnoticed. If yes, then include that control in the list of those to audit. If not, remove that control from the SOX audit list.
- Failing to evaluate reliance. Entities often do not determine to what extent the external auditor will rely on internal management testing. Auditors do not innately maximize reliance; rather, it often falls to the companies to set reliance targets. Outlining the current level of reliance and then seeking to improve it will help companies reduce SOX auditing costs.
- Forgetting that controls operate beyond the entity-level. The COSO specifies that controls exist on corporate, regional, and international levels. Furthermore, indirect and direct approaches exist for evaluating controls across all levels [e.g., running diagnostics (direct control) versus distributing training videos on security procedures (indirect)].
Avoiding these five mistakes, while by no means the only ones, will help reduce costs, provide more constructive results, and improve the likelihood of obtaining SOX compliance. If the concept of risk analysis frameworks is still a bit unclear, check out COSO’s 2013 integrated-framework suggestions.
Principles to Determine the Extent of Reliance
As noted in Marks’ top five SOX mistakes, companies tend to overlook the importance of reliance. Financial experts define audit reliance as reducing the volume or extent of internal audit work when the work performed by others meets certain standards. While reliance isn’t always considered a positive quality, in the auditing world, reliance can significantly reduce the costs of obtaining compliance, particularly if a company must adhere to numerous compliance policies. The Institute of Internal Auditors (IIA) outlines five principles for determining the extent of reliance:
- Purpose
- Independence and Objectivity
- Competence
- Elements of Practice
- Communication of Results and Remediation
Since each unique case will likely require a different level of reliance, creating a ranking system will prove beneficial. When it’s time to audit, a company will review the criteria listed for a specific case and choose the reliance level that fits the best within the context.
Need Help?
There are numerous resources out there for achieving SOX compliance. Many experts in the financial industry offer constructive insight that will help when it comes to SOX auditing. For additional assistance with SOX compliance, contact RSI Security today.
