Security measures are never foolproof. No matter how many precautions companies and users take, threat actors always find a new point of entry to exploit. Identifying and fixing vulnerabilities requires time, and there lies one of the greatest challenges — deploying sound fixes within a tight time constraint.
Imagine you get a deep cut on your arm that will likely require stitches. While on the way to the hospital, you try to reduce blood loss by using a BAND-AID. Even though the BAND-AID might not be the ideal fix, it mitigates the immediate concern – blood loss. Patches are kind of like a cut; you have to know whether a patch will fix the problem or decide if the problem requires “stitches,” all within a short time window.
Whether a patch fixes a small problem or serves as a temporary security measure while a more viable solution is designed, developing a strong patch management plan will help enterprises stay more secure and better serve their customers. Does your business know how to test and install patches for your computer system? Read on to learn what is patch management and how it can help you today.
What is patch management?
Patching refers to the insertion of code to “patch” a vulnerability or functionality issue in a system. Patch implementation usually takes place via a system update (e.g., removing old features, updating drivers). Patch Management refers to how a company identifies, develops, and implements those patches. Rather than starting from scratch, patches serve as a relatively expedient fix. If necessary, a more lasting solution to the bug may come later in the form of a new product release. For example, operating system (OS) software updates become available as companies identify vulnerabilities (like Microsoft’s Patch Tuesdays) but a completely new version of an OS offers new functionality aspects (e.g., Windows 8 vs 10).
Approaches to patch management generally encompass a combination of tools — internal methods, managing products, and outsourcing. Internal development refers to companies, like Microsoft, developing and launching patches for their products (e.g., Windows OS). The vendor provides the patch. In contrast, patch management systems are products that identify, manage, and, in some cases, fix the bugs in the code. Patch products range from fully autonomous systems to scalable management tools. It is up to the entity to choose a patch management product(s) that best fits the company’s needs. Automated patch products reduce the necessary manpower and offer customization to an institution’s needs.
Assess your Patch Management program
Why Is Patch Management Important?
The Equifax breach in 2017 compromised the personally identifiable information (PII) of over 146 million customers. One of the causes of this breach stemmed from a known vulnerability that went unpatched, allowing the hackers to sift through data for approximately 76 days. Vulnerabilities in code, when identified, require swift action. Ignoring or postponing a patch can result in loss of revenue and seriously damage a company’s reputation. The ultimate goal of patching is to mitigate the window of attack once a vulnerability is identified.
While it may sound like a simple issue of time, patching requires coordination and resources. Since patching first emerged in the 1970s, coding has evolved. Subsequently, patching evolved. In the past, entities implemented patches on a set schedule. However, that patching process enables hackers to better plan their attacks. The technology environment today requires a different approach to patch management. The greatest hurdle today remains the factor of time – time to identify, time to develop a fix, time to deploy the patch. The accelerating pace of technological advancements increasingly forces companies to shift from a reactive to proactive patch management strategy.

Patching Recommendations and Regulations
Most government regulations (e.g., NIST Cyber Security Framework, PCI DSS) mention patch management in their requirements, but the specificity of each framework varies. Part of the problem is that each enterprise and sector requires a different approach. A software company will need to approach security patch management from a different angle than a financial institution. The National Institution for Standards and Technology (NIST) updated its patch recommendations in 2013. NIST’s Guide to Enterprise Patch Management Technologies addresses the growth of automated patching versus manual patching. The guide provides implementation examples, highlights the challenges of patch management, and notes certain best practices. For example, the guide recommends the following two points for improving efficiency when it comes to patch management:
- Use a phased approach
- Establish standard security techniques when implementing new applications within a company
Likewise, the Department of Homeland Security (DHS) published recommendations for Patch Management Control Systems in 2008. Although somewhat outdated, the guidelines still serve as a viable stepping stone on which to develop newer patch management practices. Overall, the DHS outlined a seven-phase process which includes a configuration management program, patch management plan, backup/archive plan, patch testing schedule, incident response plan, disaster recovery plan, and unit patching operation outline. Some specific best practices in those steps include exposure reviews and maintaining a software/code library. The DHS guide serves as a helpful resource that offers valuable reference materials and tips for developing a tailored patch management strategy.
Moreover, considering international policies provides broader insight into global patch management practices. In France, the CSSF published three circulars addressing patch concerns in the cloud computing environment and outsourcing standards within the financial industry. The standards acknowledge a shift from physical to electronic monetary transactions and highlight issues regarding credit, e-payment, and investment institutions.
NNIT Security Insights, based in Denmark, suggests a 10-step process for developing a patch management strategy.
- Identify the requirements or policies that govern the industry (whether by region, country, etc.).
- Develop a prioritization scale. What targets are deemed most valuable or deserve the most patch attention? Then, use that scale to outline the frequency at which patches should occur.
- Consolidate the systems running. The goal is to minimize the threat surface by system hardening. Make sure systems run only the necessary services/applications. Consolidating the systems/services running will reduce the extent of patching required and better utilize available resources.
- Outline a backup plan. Conducting risk assessments and noting alternative controls will help improve recovery time when patching doesn’t go exactly to plan.
- Review internal and external vulnerabilities. It is sometimes easy to focus only on internal operations, but any interactions with outside vendors increase the level of risk a company faces.
- Write activation and maintenance guidelines that specify system configuration policies. For example, outline item identification and registration policies as well as update procedures.
- Outline a decommission policy. Much like experts warn you to shred any valuable documents before throwing them away, it is important to thoroughly deactivate devices or programs before retiring them. For example, make sure a device no longer has access to a system and cannot be accidentally reactivated. Furthermore, this stage encompasses monitoring and compliance reporting.
- Develop general patch procedures including when to service a system, how to report security or functionality issues, and how to implement patches as quickly as possible.
- Create a technical patch checklist for technicians (e.g., a list including checking back-ups, disk usage, and hardware malfunctions). This list should be similar to a pre-flight checklist that pilots follow before takeoff. It is not designed for all employees; rather, it focuses solely on the technical aspect of patching.
- Evaluate key performance indicators (KPI) and designate a chain of communication for reporting.
Observing other patch management practices nationally and internationally will help enterprises pick the best tools and methods for their needs. No one plan will fit all institutions; rather, it’s figuring out which combination uses resources most efficiently and produces the highest quality outcome.

Patch Management Plan
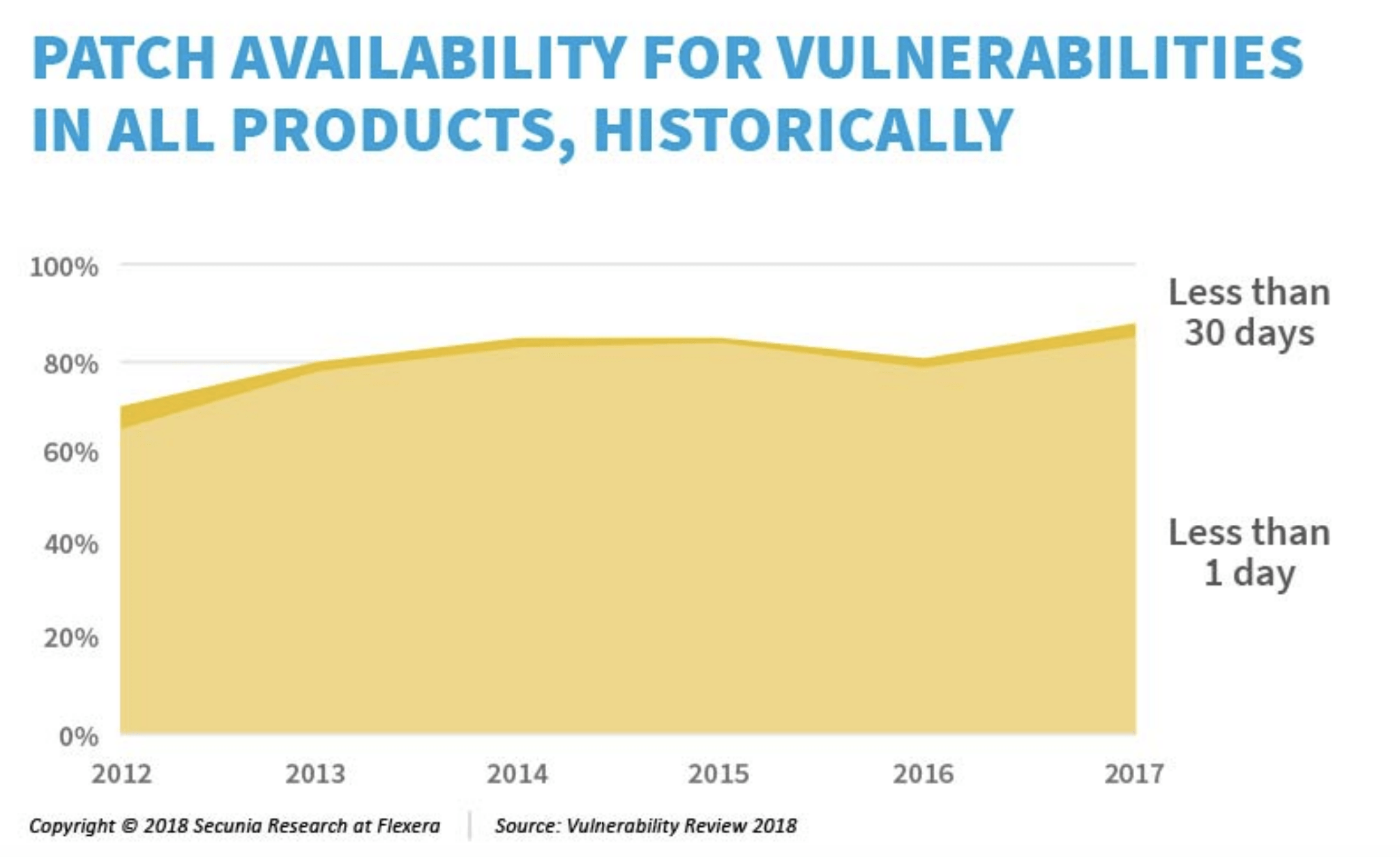
A 2018 report found that 86 percent of product vulnerabilities have a patch available within 24 hours of identification. This percentage increased from 2012 likely due to improved communication channels. When institutions share their knowledge about vulnerabilities and solutions, time-to-patch becomes quicker and the impact more widespread. The following general tips will help each entity tailor a patch management plan to best fit their needs.
-
Stay on top of patch news
The longer vulnerabilities remain unpatched, the more likely an attacker will breach a system. In fact, most security vulnerabilities are not zero-day exploits; rather, they are vulnerabilities already discovered. It’s important to educate employees on the importance of updating systems. For example, if the update alert occurs at an inconvenient time, they should set a reminder to update their systems later. Even more importantly, enterprises should maintain and update contact information so the correct system administrators receive vulnerability notices when an exploit surfaces. In the Equifax breach, a government report found that the employee contact list was out-of-date, which caused certain individuals to not receive notification of the vulnerability. In other words, entities must not only consume news, but also be able to disseminate news quickly when required.
-
Be adaptable
If a patch is ready to launch, don’t wait for a scheduled update day to launch the fix. Waiting will only increase the exposure time of the vulnerability and counteract the goal of minimizing the threat window. Many companies are turning to automated patch system (e.g., JUpdater, StableUpdate or Visual Patch.) as they become more reliant on technology for everyday interactions. Experts believe patching will shift from downloadable updates to a continuous, automated patch process, where, ultimately, the end-user plays no role in installing the security updates. With information flying faster than a thought can pass through the human brain, it’s logical that patch management will eventually surpass the human management process. The current patch management system requires a balance between the advancing automated patch programs and the human patch management processes. Consequently, enterprises should develop an agile patch strategy and continually review it as new methods emerge.
-
Create a patch “tool belt”
Computer Weekly notes that every company will require a different approach to patching. Unlike software developers, companies that purchase and utilize software will likely need to institute an entirely different method, as they are not the ones writing the patches. Furthermore, companies that understand their resources possess the capabilities to better deploy patches or fix security patches (e.g., choosing to outsource versus an internal fix). Research the available patch tools and services prior to developing a patch management strategy, so as to choose the tools that best fit the company’s needs and available assets.
-
Cooperation
Cooperation involves internal and external effort. Patches work best when implemented in a coordinated manner. On the one hand, this requires internal communication between departments and employees. Smooth channels of communication ensure the patch launches successfully and reaches the intended devices. On the other hand, cooperation across industries (external communication) aid in improving the overall success and time-to-patch rates. Forbes reported that attackers increasingly target industries using the same techniques or variations on multiple entities within an industry. Thus, understanding emerging threats and discussing potential solutions enables companies to be better prepared when an attack occurs. In an offensive sense, cyber security presents a significant challenge. It’s difficult to anticipate when and where a future attack will occur. Collaborating with other businesses and industries allows all involved to gain greater insight on threat indicators. Moreover, collaborating benefits both small and large companies. Sharing security trends helps entities with limited resources that cannot invest more in industry research. Even companies with significant resources benefit, as they can each specialize their research, to an extent, on a certain type of threat. In the payment card industry, the National Credit Union Information Sharing and Analysis Organization (NCU-ISAO) works to share threat intelligence among the credit union community. Likewise, the ISAO monitors cyber threats and standards by industry with the goal of connecting and informing companies.
-
Consider the end user
Is the patch at the scale that it requires a new product release or simply an update? Patch management, at this point, generally requires end-user permission, so it’s important to consider how/when to launch a patch and how to notify end-users when a patch becomes available.
Need Patch Help?
Patch management sometimes seems like an unwinnable race, one in which the runner, no matter how hard he tries, will always be several steps behind his opponent. Despite the fact that hackers will always seek to exploit new vulnerabilities, new patch management tools and methods continue to improve the patch management environment. Staying current with the latest patch news, employing automated patch management tools, and establishing a designated patch management team will aid institutions in shifting from a reactive to a proactive patching strategy. For help with your patch management policy and cybersecurity solutions, contact RSI Security and request a demo today.