Compliance Guide To Payment Card Industry Data Security Standard (PCI DSS)
Data Security is Good Business
Keeping cardholder data safe and secure is an important part of your business as well as your agreement with your payment card brands and acquirers in order to accept the credit card based payments . Compromised data has a negative impact on everyone involved. Protecting data can help:
- Improve customer relationships
- Increase overall profitability
- Prevent damage to your business’s reputation
Starting with this part I of multi-part series of articles, we will address frequently asked questions and provide a comprehensive guide on PCI DSS requirements and compliance.
What is PCI DSS?
PCI security standards are technical and operational requirements set by the Payment Card Industry Security Standards Council to protect cardholder data. The standards globally govern all merchants and organizations that store, process or transmit this data, and include specific requirements for software developers and manufacturers of applications and devices used in the transaction process.
PCI DSS is the global data security standard that any business of any size must adhere to in order to accept payment cards, store, process, and/or transmit cardholder data. Standard PCI DSS presents common sense steps that mirror best security practices you can follow toward minimizing the threat of data compromise and maintaining customer trust.
Many organizations treat compliance as a one-time, annual event. But only focusing on an annual compliance assessment can create a false sense of security.Its only by achieving and maintaining compliance that your cyber defenses will be adequately primed against attacks aimed at stealing cardholder data.
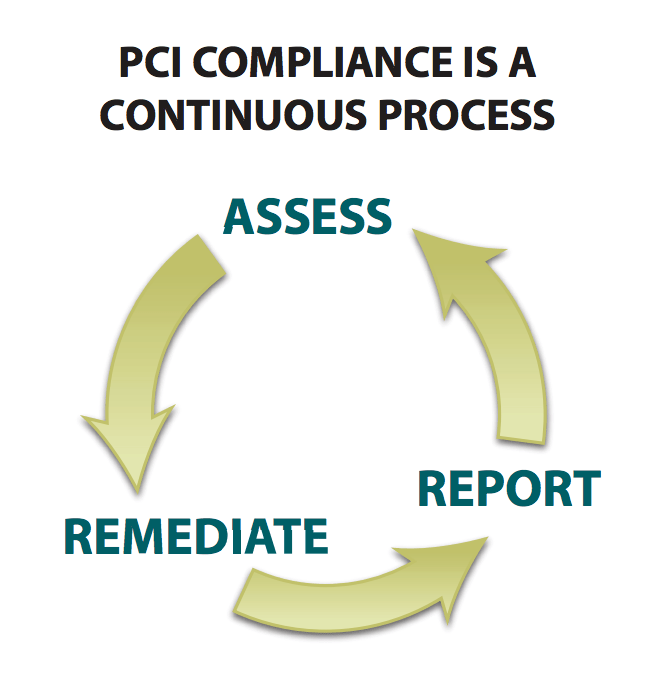
PCI Compliance is a continuous process as show in the table below.
|
 |
Who is responsible for defining and enforcing PCI DSS standard and compliance?
 PCI Security Standards Council (PCI SSC), formed in 2006 and comprised of American Express, Discover, JCB International, MasterCard and Visa Inc, collectively called Payment Brands, share equally in governance and execution of councils work.
PCI Security Standards Council (PCI SSC), formed in 2006 and comprised of American Express, Discover, JCB International, MasterCard and Visa Inc, collectively called Payment Brands, share equally in governance and execution of councils work.
PCI SSC is responsible for defining and implementing PCI security standards.
Compliance with the PCI security standards is enforced by the major payment card brands who established the Council: American Express, Discover Financial Services, JCB International, MasterCard Worldwide and Visa Inc.
Is PCI Compliance applicable to your business?
The PCI DSS applies to any entity that stores, processes, and/or transmits cardholder data. It covers technical and operational system components included in or connected to cardholder data. If your business accepts or processes payment cards, it must comply with the PCI DSS.
- All merchants that store, process or transmit cardholder data must be PCI compliant.
- All credit card based payment processing service providers must be PCI compliant.
What PCI Compliance reporting requirements are applicable to your organization?
Before you undertake the process of becoming PCI Compliant, you will need to determine the PCI Compliance reporting requirements for your business. The table below provides a general guide to determine the requirements. Please contact your acquiring bank or payment brand (for service providers) for the level and reporting requirements specific to your organization.
Table 1 – General Merchant Levels and PCI reporting requirements
| Criteria | Merchant Level | PCI Compliance Requirements |
| 6M or more card transactions
Or
If the acquirer or payment brand determines |
Level 1 |
|
| More than 1M and less than 6M card transactions | Level 2 |
|
| More than 20,000 and less than 1M card transactions | Level 3 |
|
| All others | Level 4 |
|
Service Provider Levels and PCI reporting requirements
A service provider is a business entity that is directly involved in the processing, storage, or transmission of cardholder data on behalf of another business. This also includes companies that provide services that control or could impact the security of cardholder data. Examples include managed service providers that provide managed firewalls, IDS and other services, as well as hosting providers and other entities.
Table 2 – Service Provider Levels and PCI reporting requirements
| Criteria | Service Provider Level | PCI Compliance Requirements |
| store, process, or transmit more than 300,000 credit card transactions annually | Level 1 |
|
| store, process, or transmit less than 300,000 credit card transactions annually | Level 2 |
|
Who is a Qualified Assessor?
 The PCI Security Standards Council provides programs for two kinds of certifications: Qualified Security Assessor (QSA) and Approved Scanning Vendor (ASV).
The PCI Security Standards Council provides programs for two kinds of certifications: Qualified Security Assessor (QSA) and Approved Scanning Vendor (ASV).
QSAs are companies that assist organizations in reviewing the security of its payments transaction systems and have trained personnel and processes to assess and validate compliance with PCI DSS.
PCI ASVs provide commercial software tools and analysis services to perform certified vulnerability scans for your systems. The PCI SSC also provides educational resources to further security awareness for merchants and service providers, including training for Internal Security Assessors (ISAs).
Do you require an Qualified Assessor (QSA)?
Because most large merchants have complex IT environments, many hire a QSA to glean their specialized value for on-site security assessments required by PCI DSS. The QSA also assesses and validates compensating controls. However, the payment card brands provide the option of doing an internal assessment with an officer sign-off if your acquirer and/or merchant bank agrees. The PCI SSC also provides training for Internal Security Assessors (ISAs). Smaller merchants may be eligible to self-assess their compliance and validate using the Self-Assessment Questionnaire (SAQ) found on the PCI SSC website.
What is a Self-Assessment Questionnaire (SAQ)?
The SAQ is a validation tool for eligible merchants and service providers who self-evaluate their PCI DSS compliance and who are not required to submit a Report on Compliance (ROC). A number of SAQs are available for different environments as shown in the table below.

Table 3 – Types of SAQ
| SAQ |
Description |
| A | Card-not-present (e-commerce or mail/telephone-order) merchants, all cardholder data functions outsourced. This would never apply to face-to-face merchants. |
| B | Imprint-only merchants with no electronic cardholder data storage, or standalone, dial-out terminal merchants with no electronic cardholder data storage |
| C-VT | Merchants using only web-based virtual terminals, no electronic cardholder data storage |
| C | Merchants with payment application systems connected to the Internet, no electronic cardholder data storage |
| D | All other merchants not included in descriptions for SAQ types A through C above, and all service providers defined by a payment card brand as eligible to complete an SAQ |
What are a few quick steps you can take to ensure card data security?
- Buy and use only approved PIN entry devices at your points-of-sale.
- Buy and use only validated payment software at your POS or website shopping cart.
- Do not store any sensitive cardholder data in computers or on paper.
- Use a firewall on your network and PCs.
- Make sure your wireless router is password-protected and uses encryption.
- Use strong passwords. Be sure to change default passwords on hardware and software most are unsafe.
- Regularly check PIN entry devices and PCs to make sure no one has installed rogue software or skimming devices.
- Teach your employees about security and protecting cardholder data.
- Follow the PCI Data Security Standard.
What data can you store or must not store in your environment?
Remember if you don’t need it, don’t store it!
For merchants who have a legitimate business reason to store cardholder data, it is important to understand what data elements PCI DSS allows them to store and what measures they must take to protect those data.
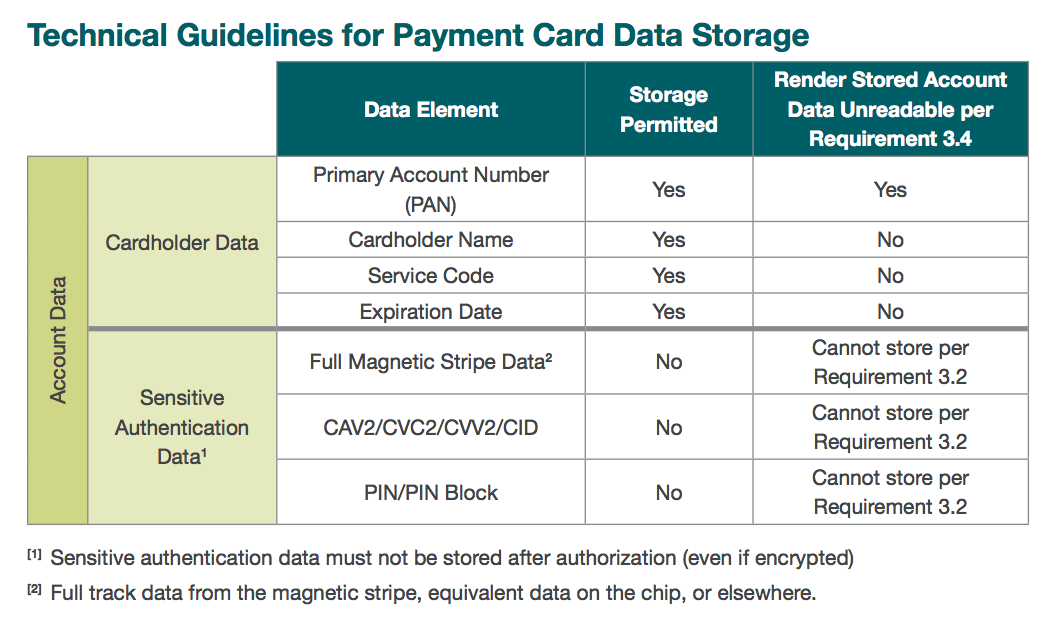
 Cardholder data refers to any information contained on a customers payment card. The data is printed on either side of the card and is contained in digital format on the magnetic stripe embedded in the backside of the card. Some payment cards store data in chips embedded on the front side. The front side usually has the primary account number (PAN), cardholder name and expiration date. The magnetic stripe or chip holds these plus other sensitive data for authentication and authorization. In general, no payment card data should ever be stored by a merchant unless its necessary to meet the needs of the business. Sensitive authentication data on the magnetic stripe or chip must never be stored. Only the PAN, expiration date, service code, or cardholder name may be stored, and merchants must use technical precautions for safe storage.
Cardholder data refers to any information contained on a customers payment card. The data is printed on either side of the card and is contained in digital format on the magnetic stripe embedded in the backside of the card. Some payment cards store data in chips embedded on the front side. The front side usually has the primary account number (PAN), cardholder name and expiration date. The magnetic stripe or chip holds these plus other sensitive data for authentication and authorization. In general, no payment card data should ever be stored by a merchant unless its necessary to meet the needs of the business. Sensitive authentication data on the magnetic stripe or chip must never be stored. Only the PAN, expiration date, service code, or cardholder name may be stored, and merchants must use technical precautions for safe storage.
| Data Dos | Data Donts |
| Do understand where payment card data flows for the entire transaction process | Do not store cardholder data unless its absolutely necessary |
| Do verify that your payment card terminals comply with the PCI Personal Identification Number (PIN) Transaction Security (PTS) requirements | Do not store sensitive authentication data contained in a payment cards chip or magnetic stripe, including the 3-4 digit card verification code or value printed on the front or back of the payment card, after authorization. |
| Do verify that your payment applications comply with the Payment Application Data Security Standard (PA-DSS) | Do not have payment terminals print out personally identifiable payment card data; printouts should be truncated or masked |
| Do retain (if you have a legitimate business need) cardholder data only if authorized, and ensure its protected. | Do not store any payment card data in payment card terminals or other unprotected endpoint devices, such as PCs, laptops or smart phones |
| Do use strong cryptography to render unreadable cardholder data that you store, and use other layered security technologies to minimize the risk of exploits by criminals | Do not locate servers or other payment card system storage devices outside of a locked, fully secured and access-controlled room |
| Do ensure that third parties who process your customers payment cards comply with PCI DSS, PTS and/or PA-DSS as applicable. Have clear access and password protection policies. | Do not permit any unauthorized personnel to access stored cardholder data |
Merchants should develop a data retention and storage policy that strictly limits storage amount and retention time to that which is required for business, legal, and/or regulatory purposes.
What are PCI guidelines to protect stored cardholder data?
PCI DSS requires Primary Account Number (PAN) to be rendered unreadable anywhere it is stored including portable digital media, backup media, and in logs.
Solutions for this requirement may include one of the following:
- One-way hash functions based on strong cryptography converts the entire PAN into a unique, fixed-length cryptographic value.
- Truncation permanently removes a segment of the data (for example, retaining only the last four digits).
- Index tokens and securely stored pads encryption algorithm that combines sensitive plain text data with a random key or pad that works only once.
- Strong cryptography with associated key management processes and procedures.
What are the technical and operational goals for PCI DSS compliance?
- Build and Maintain a Secure Network
- Protect Cardholder Data
- Maintain a Vulnerability Management Program
- Implement Strong Access Control Measures
- Regularly Monitor and Test Networks
- Maintain an Information Security Policy
Does outsourcing card processing make you compliant?
Your organization is responsible for protecting your customers card data. Outsourcing simplifies payment card processing but does not provide automatic compliance. Don’t forget to address policies and procedures for cardholder transactions and data processing. Your business must protect cardholder data when you receive it, and when you process chargebacks and refunds. You must also ensure that providers applications and card payment terminals comply with respective PCI standards and do not store sensitive cardholder data. You should request proof of compliance annually from providers.
In the next part of the PCI DSS guide series, we will look at specific technical and operational DSS requirements for an organization to be PCI Compliant.
Download Our PCI DSS Checklist
Assess where your organization currently stands with being PCI DSS compliant by completing this checklist. Upon filling out this brief form you will receive the checklist via email.
About RSI Security
RSI is the nation’s premier information security and compliance provider dedicated to helping organizations achieve risk-management success. We work with some of the world’s leading companies, institution and governments to ensure the safety of their information and their compliance with applicable regulation. We also are a security and compliance software ISV and stay at the forefront of innovative tools to save assessment time, increase compliance and provide additional safeguard assurance. With a unique blend of software based automation and managed services, RSI can assist all sizes of organizations in managing IT governance, Risk management and compliance efforts (GRC).






