It only took Clark Kent a pair of glasses to keep his identity a secret, but in today’s world, identities are complex webs of digital and physical items. You can’t do much of anything without your identity, whether that’s withdrawing money from a bank or logging into your phone. When you walk into a bank and request money from the teller, they’ll ask you for a series of things to prove that you are indeed who you say you are. It might be a combination of things from physical identification to a password or information that only you would know.
An identity and access management system (IAM) is designed to grant access to the right individual(s) at the right time and under the right context of the enterprise. Whether the IAM system is designed for external users such as customers or business partners, or internal users such as employees or contractors, each user should have a single digital entity that defines the role and privileges of that user. Whether you have ten employees, five hundred employees, or thousands of customers, and Identity & access management tool helps manage each unique user.
Identity and Access Management Tools and Systems
There are many IAM tools to choose from when deciding how to protect identity and access. Identity repositories, provisioning software, password-management tools, security-policy enforcement applications, and reporting and monitoring apps are a few IAM tools.
Many major companies, of course, provide IAM services that can easily be used if you do not have an in-house IT team. Knowing what tool to use is about understanding cybersecurity trends, considering costs, user experience ease, and level of communication with the tool’s creator(s).
An identity and access management system might include single sign-on, multi-factor authentication, or privileged access management (PAM). An IAM system can be created internally by your company and integrated on-site, managed by a third-party company, or rely on a cloud service.
- Single sign-on: This system allows users to access a service using one unique login credentials (e.g. a password or a biometric tool). Additionally, this sign on can then be used to access any network or service owned by the business. For example, a single sign-on is used to access both a Google account as well as a YouTube account.
- Multi-factor authentication: This system requires users to employ two or more forms of login credentials to access information. This is often referred to as two-factor authentication. This would include using a password and a biometric tool or using a biometric tool and a pin, using a password and verifying authenticity by replying to a text/email/phone call.
- Privileged access management: This system is the most secure requiring that a user requests access to a system with a specific set of privileges. Microsoft indicates that PAM “adds more monitoring, more visibility, and more fine-grained controls. This allows organizations to see who their privileged administrators are and what they are doing. PAM gives organizations more insight into how administrative accounts are used in the environment.”
Assess your cybersecurity
Identity and access management solutions do not need to be difficult; here are ten reasons why you need an identity and access management system.
1. Security Management
Identity and access management systems are a crucial part of maintaining a business’ network security. It seems like every day there’s yet another data breach in the headlines. And while the news often focuses on the larger companies such as Yahoo or Equifax, Verizon reports in their 2019 Data Breach Investigations Report that 43 percent of breaches involved small businesses. Nefarious actors may find smaller targets are easier to breach. as small business owners focus on growing their company in other ways and ignore cybersecurity.
Strong identity and access management solutions focus on tackling this problem from both ends protecting you from nefarious actors and from inside threats or unauthorized users. By putting controls in place that protect multiple systems across the business or deny access to those who do not need it, an IAM system improves overall security. Implementing an IAM system effectively lowers the risk of falling prey to a data breach.
2. Identity Management
A large portion of security threats come from insiders. This includes both those begrudged employees and unauthorized users. In fact, most industries fall victim to either human error or privilege misuse; the Data Breach Investigations Report indicated that 34 percent of breaches were a result of internal actors. Note that the large majority of retailers have already experienced a data breach and among the top three threat patterns, two are related to human error.
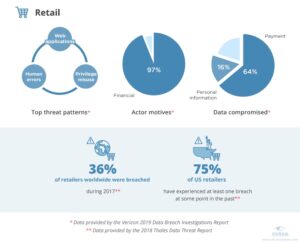
Image source: https://www.ekransystem.com/en/blog/5-industries-most-risk-of-data-breaches
An IAM system can control which users have access to information and deny access to those who don’t need it. If an employee falls prey to something such as a phishing scam, the nefarious actor will not be able to use the stolen credentials to access all your company’s information. The ability to grant access to employees or users also allows you to track and keep a record of activities by those users. This information is especially useful for internal or external audits to help prevent data leaks or breaches.
3. Segregated Tasks
Sometimes a company doesn’t properly delegate specific access to employees instead of giving them unimpeded access to files they don’t need as part of their job. This later creates issues of a breach should an employee who isn’t properly trained on information security be hacked or purposefully wish the company harm. In a Data Breach Study conducted by cybersecurity company Veronis, “in 2019, on average, every employee had access to 17 million files and 1.21 million folders.” Furthermore, a majority of them had access to sensitive files.

Image source: https://www.varonis.com/blog/data-breach-statistics/
The question is why these employees had access to such information in the first place. Identity and access management solutions serve to control the level of access granted to employees which can more efficiently segregate tasks. With this in mind, businesses can manage identities while strategically aligning employees to their respective expertise and tasks.
4. Reduce Costs
In addition to maximizing employee output by using Identity and Access Management Systems to segregate tasks, companies can save costs employing an IAM system. If you think paying for a good IT solution is expensive, think about how much an average data breach costs. IBM’s Cost of Data Breach Report found that the average cost of a data breach is $3.92 million dollars.
With more and more hackers targeting smaller businesses and human error causing significant data breaches, implementing IAM tools is an effective way to save money. Combined with expert advice from RSI Security about all your cybersecurity needs, you can significantly reduce the likelihood and expenses of a breach.

Image Source: https://newsroom.ibm.com
Customers certainly don’t want to stick with a company that experiences a data breach and will take their money elsewhere if they believe their data is not safe.
5. Attract More Users
In a data breach survey conducted by the secure payments provider PCI Pal, they found that “in the US, 83 percent of consumers claim they will stop spending with a business for several months in the immediate aftermath of a security breach, and over a fifth (21%) of consumers claim they will never return to a business post-breach.” Thus, by marketing your business as one that prioritizes data security, you can gain the trust of customers.
One particular identity and access management solution is to employ a single sign-on service that allows users to gain access to information through their social media profiles. Creating ease of access means more users are likely to engage with a service that does not require a multitude of hoops through which to jump. An IAM system guarantees that user data remains safe and provides access to multiple platforms.
6. Improve User Experience
Attracting more customers means improving the user’s experience. Tools like social media logins facilitate easy access to your own service. Take, for instance, a user who is looking to fill out a job application. If the user is given the opportunity to link their account to a social profile instead of generating a unique username and password, they are more likely to apply to the job due to ease of access.
Users are also looking for ways to more easily share the content they create. By allowing users to access multiple platforms with single-factor authentication, users can focus on producing content and not feeling shut out from platforms to which they cannot remember their login credentials.

7. Supports Business Growth
Naturally, attracting more users and improving the experience users have while working with your company is a great way to support business growth. While identity and access management solutions may not be the core component of your business’ growth, consider how using efficient systems provides time to focus on other issues or creative ventures within the company.
If an IT team must manually grant all employees access to systems or maintain that access, precious time could be lost to backlogs of employees waiting to begin their work. As a small business, linking all your myriad of systems with an easy single sign-on service can be confusing or take precious time. As a large business, it may feel completely overwhelming to have to sign up hundreds of individual employees. An IAM system can manage both login credentials while maintaining a secure environment in which employees can work.
8. Performance
Good performance in a company is more than just hiring excellent employees to handle the task at hand. A brilliant typist would be seriously impaired with one hand tied behind their back. Likewise, removing the responsibility of your IT team to grant system access or reset passwords allows them to use their talents on more pertinent projects. Employing an identity and access management system allows your teams to effectively do what they do best without hindering them.
Identity and access management systems lift the burden from humans — reducing the number of errors that can happen as a result and thus saving you money — and place it on an efficient machine that provides protection and ease of use.
9. Increased Mobility
While a pandemic like COVID-19 has pushed almost all employees to work from home, mobility was already frequently a large part of many operations. Working from home, on the road or even overseas requires a strong security system. Using an IAM system to mitigate threats from outside the office allows a flexible work environment in which employees can still perform at high levels and companies can protect their information.
Additionally, more individuals are using cellphones to access their information whether this is for banking, social media, or communication. This mobility requires significant identity and access management solutions to ensure that customers’ data is safeguarded against internal employee error or outside threats.
10. Automatic Deprovisioning
Finally, an IAM system will help track and manage user information in a non-intrusive way that can point out old or expired users. Many hackers seek to exploit infrequently used or expired accounts because the user would not be aware of suspicious behavior. Since many users have been granted access to even sensitive files, a hacker would be able to gain a lot of information by exploiting this weakness.
An automatic de-provisioning of these old accounts through an IAM tool is a helpful way that does not require the intervention of your IT team which allows them to focus on other tasks.
Conclusion
There are other reasons you might invest in an IAM system but this nearly comprehensive list gives you the information you need to better understand IAM systems. From here, you have the base to seek out the right IAM tool and the language to understand your needs and expectations when you have a free consultation from a cybersecurity expert with RSI Security.
Small and large businesses alike are the targets of outside threats with the costs and frequency of a breach too high to gamble customer and employee data by not safeguarding login credentials and other access. IAM systems, even when relying on third-party companies, give you back the control by keeping careful track of your employees or customers.
Yes, you might need more than just a pair of glasses to maintain user’s “secret identities” but this element of your business should certainly not be overlooked. A proper IAM tool can protect users from any villain. Additionally, IAM can help your business maintain the necessary levels of security needed to meet compliance requirements.
