For the legal industry, the cybersecurity goals of protecting proprietary information, data, and systems go hand in hand with client confidentiality. Yet, one in four legal firms experiences a data breach, and many firms still do not understand law firm security requirements or cybersecurity policy requirements.
Without the guarantee that client privacy will be protected, legal firms lose their credibility. Cybersecurity has yet to become interwoven within the legal environment, which raises the question — should law firms consider working with a full-time cybersecurity partner?
The statistics below reveal the problematic cybersecurity trends emerging within the legal industry; however, many legal establishments still do not follow law firm security requirements or have comprehensive cybersecurity policies. Moreover, according to a 2019 American Bar Association tech report, one in four legal firms experience data breaches. These statistics underscore the need for greater cooperation between cybersecurity firms and legal firms in the policy development and implementation stages.
- 26% of law firms experienced a security breach
- 3% increase in breaches compared to 2017
- 36% encountered malware or viruses on their computers
- 9% of law firms had to contact their clients and law enforcement after a breach
- 42% of mid-sized law firms experienced breaches
Law Firm Security Requirements
While there isn’t a cybersecurity framework specifically tailored to the legal environment, there are certain cyber responsibilities legal firms must fulfill.
- Adequately protect client proprietary data by implementing, at a minimum, basic cybersecurity best practices
- Know what types of attacks commonly affect legal firms
- Know what data you have and the value of it. Ranking the risk associated with different types of data helps implement controls commensurate with the associated risk.
- Follow the American Bar Association’s (ABA) cybersecurity policies.
The Impact of Breaches on Legal Firms
Breaches aren’t just an internal issue. When breaches occur at non-legal companies, they begin to scrutinize their vendors/partners as part of due diligence. This includes law firms. Since law firms are repositories for sensitive and proprietary data, such as intellectual property and mergers and acquisitions, legal firms must take cybersecurity and compliance standards seriously if they wish to retain their clients. Business relationships rely on trust, and companies cannot trust a perceived weak link. Entities hiring a law firm do not want to be liable should any critical information be compromised or face repercussions for breaking cybersecurity compliance standards.
Two Cybersecurity Challenges for Law Firms
Cost: Whether implementing cyber safeguards before a breach occurs or after, law firms will face increased costs. A Robert Half survey in 2019 found that 76% of lawyers interviewed said they planned to increase their cybersecurity resource budget, with an average budget increase of 21%. To compete and attract security-aware clients, small to mid firms will likely need outside assistance when developing a cybersecurity strategy.
Information Overload: Many of the newer privacy standards like GDPR and CCPA require incident response plans and adequate security measures. With increased monitoring, law firms may become swamped in high computer log volume, making it difficult to manage. This is where a cyber partner can help. Law firms have a lot on their hands dealing with clients, so it’s not always easy to stay on top of cyber monitoring. The 2018 ABA Legal Technology Survey Report found that 18 percent of respondents said they didn’t know if their security was breached and 61 percent of firms with over 500 attorneys also said they didn’t know if their security infrastructure was breached.

How to Choose a Cyber Partner
Before jumping headlong into the cybersecurity market, here are some basic questions to help law firms fine-tune their strategy for hiring a cyber partner.
Assess your cybersecurity
What size is your firm?
The size of your firm will determine whether you need to use cybersecurity services outside your firm. For example, a small firm is unlikely to have an IT team, much less a cybersecurity team. Consequently, small firms will need partners to conduct an initial risk assessment, suggest tools, and potentially manage those cyber tools.
Do you have internal IT knowledge?
Leveraging employees with IT or cyber knowledge may mean a law firm requires less outside assistance. For example, a risk assessment could be conducted using internal personnel, although it is always a good idea to have an external assessor review the findings. Likewise, if a third-party assists with setting up cyber monitoring tools, an internal team could oversee the controls. Using a cyber partner allows for flexibility and gives law firms the ability to fill the gaps in personnel knowledge base and time available. If a law firm has an internal cyber or IT team, the best cyber partner may involve tools only. In contrast, a firm with no internal cyber knowledge will likely require consulting and security control implementation services.
What’s your budget?
Consulting with a cyber partner will help identify the most cost-effective methods available to provide the minimum necessary cyber protection. A budget breakdown will help law firms determine where to funnel the most money to get the most significant return. For example, there are free tools available that can be used for data inventory, self-assessments, or monitoring. Using free but highly recommended tools where possible, frees up financing for one or two expensive cybersecurity measures.
What kind of information do you have?
Not all information needs the same level of protection. Law firms need to take stock of what information they collect, store, or transmit and then determine which types of data require greater protection. A cyber partner can help with this process, or a law firm can do it. In May of 2020, LegalTechNews reported that 193 law firms exposed information on an open database due to lax security practices. The compromised data, including user IDs and passport information, was available for anyone who knew where to look. This example highlights how essential data inventories are. If you don’t know where your data goes, you can’t adequately protect it.
Sample Cybersecurity Policy for Law Firms
Below are a few questions to guide law firms in developing a cybersecurity policy. A well-rounded approach should address compliance, infrastructure, and employees.
- Do you have a vulnerability management program? Large clients often request attestation of vulnerability management in cybersecurity frameworks (e.g., PCI DSS, CMMC).
- Is vulnerability testing a common practice? Pen testing, risk assessments, and process reviews will help law firms determine if existing practices are putting their data at risk.
- Do you have an Incident Response Plan? Incident response plans should outline backup procedures should a breach occur and how to mitigate an ongoing cyber attack. For example, if a law firm loses data, how will it represent its clients?
- Are monitoring tool licenses current? If a law firm is using licensed tools, it must ensure all licenses are up to date. Expired monitoring tools leave company systems vulnerable and prolong the discovery stage, a stage crucial for mitigating impact. Additionally, avoid pirated software, which may be a temptation for solo lawyers with minimal funds, because it may not have automatic license updates.
- What are the best defense mechanisms for your law firm? Review the types of firewalls, email security measures, encryption, authentication, anti-virus software, and endpoint security in place.
- Do you have an awareness training program? Cybersecurity awareness should cover management from top to bottom. In other words, leadership must prioritize cybersecurity and make sure employees follow suit.
- What compliance regulations apply to law firms? Before finalizing a cyber policy, law firms need to research what compliance frameworks apply to them.
- Do you have proper documentation and enforcement protocols? Having a policy isn’t helpful unless it’s documented and implemented correctly. Documentation helps ensure that employees have a document to refer to should they have questions.
Cybersecurity for Small Law firms
Mid-sized law firms, between 10-49 attorneys, experience more data security breaches than larger law firms. This fact may not come as a shock considering they likely have fewer resources for cybersecurity safety measures. To attackers, small companies don’t have enough valuable data to be a worthwhile target, and large firms have more stringent security measures. This leaves mid-sized businesses as the optimal target — enough data to make the attack profitable and marginal cybersecurity. Although small law firms don’t attract the most attacks, they should still take an active cybersecurity approach. Small to mid-sized legal firms need to take a new approach by:
- Leveraging free tools;
- Considering cyber liability insurance;
- Running risk assessments to identify the areas that require the most security resources; and
- Partnering with a cybersecurity firm to provide industry advice or services
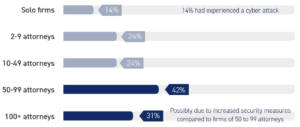
Image Source: data from 2018, https://atlantsecurity.com/cybersecurity-for-law-firms/
How a Multi-Layer Approach can Improve Cybersecurity
Developing a robust and adaptive cybersecurity plan requires a proactive approach. The attack lifecycle can be broken down into three categories: preattack, during an attack (prevention and detection), and post-attack.
Phase 1: The pre-attack stage is not the time companies should be waiting, dreading an attack; instead, it’s the phase in which companies should prepare, use predictive tools, conduct threat assessments, and rank attack likelihood. This phase is also the time to reinforce security awareness training. If a law firm doesn’t have an internal cybersecurity team to provide training, it can bring in a third party team or host a webinar for employees cyber awareness training. Lastly, during this phase, consider cyber liability insurance and data breach insurance.
Phase 2: A preventative stage refers to preventing (during the attack) how far an intruder can penetrate. For example, using next-generation firewalls, email security, and encryption can slow down or stop an attacker from accessing the most sensitive data. Again, awareness and training can help in this phase. If an employee knows how to recognize suspicious activity, an attack can be stopped more quickly, preventing significant damage. Detection tools/procedures, such as Intrusion Detection System (IDS) or threat hunting, help alert cybersecurity teams about the path of the attack or what information the attacker may be seeking. The faster a breach is detected, the faster teams can mitigate the damage.
Phase 3: The post-attack or retrospective phase (after the attack) is the time to learn from your (or others’) mistakes. Taking the time and effort to analyze what went wrong and how an attack can be prevented or minimized is part of a well-rounded cybersecurity plan.
Post-attack questions to consider:
- Where did the initial intrusion occur, and was it a known vulnerability?
- What information or systems were affected?
- Was the recovery plan followed, and how fast was recovery time?
- How can a similar attack be prevented?
Process of Infiltration
Understanding the hacking process will help law firms decide what type of tools and security partners to choose from. By analyzing past attacks, cybersecurity analysts have estimated how long each step of the infiltration process takes. Having this information empowers companies to know how long they have to shut down a hacker and minimize the damage.
- Initial Foothold – According to the 2018 Verizon Data Breach Investigations Report, 70 percent of initial attacks take minutes to execute.
- Network Propagation – Propagation refers to the steps in between the intrusion and execution of the primary objective. Depending on the complexity of the attack and the defenses a law firm has, this phase can take anywhere from minutes to hours to days. For example, a malicious program may spend a significant amount of time trawling through a law firm’s systems to see what can be accessed or find the most valuable information, underscoring the need for effective detection tools.
- Active Objectives – Once the hacker or malicious program has found the target, the final step is to exfiltrate the information or lock the law firm out if the primary objective is to obtain a ransom payout. The majority of data exfiltration takes only minutes to execute.
Tips For Effective Monitoring
Leverage automation – Just 100 devices can generate 1 GB or more of log data per day. With an extensive collection of logs accumulating quickly, companies should leverage automated monitoring tools. Using tools and partnering with a cybersecurity firm can be cheaper than hiring an internal team.
Don’t just monitor internal traffic and activity. Sweeping the deep web and dark web, in addition to the surface web, to determine if employee credentials have been compromised can be an effective early detection tactic. In 2019, 80 percent of hacking-related breaches stemmed from compromised credentials. Many companies are now using artificial intelligence technology rather than hiring individuals to run essential tools to conduct stolen credentials or PII searches.
Key Takeaways
- Don’t wait until an attack occurs to take cybersecurity seriously.
- You can’t fix what you don’t know is broken, so understand what information you have and where it goes.
- More cybersecurity and privacy compliance standards are emerging, meaning law firms will likely face more penalties should a breach occur in their systems.
Need Help?
Whether you are a small, medium, or large law firm, investing in cybersecurity improves client confidence and reduces the risk to your company’s data. To learn more about law firm security requirements and how to craft law firm cybersecurity policies contact RSI Security for a consultation.
