With 2020 here, it’s a good time to take stock of the cybersecurity environment and the lessons learned over the last year. According to Norton Security, there have been approximately four billion records compromised due to breaches in 2019. Attack tactics change and new vulnerabilities emerge as threat actors become more creative. There are several different types of data breaches that can affect your business.
Learn about your potential threats with our comprehensive guide.
What Exactly Is a Data Breach?
The term “data breach” gets thrown around quite a lot. However, there are differences between data breaches and incidents. It may seem trivial to debate what to call compromised systems or data, but clear definitions will help determine what remediation steps a company takes. Moreover, definitions and classification enable better notification systems, which departments assist in the remediation, as well as quicker resolution times. Below are the four classifications typically used in the cybersecurity environment.
Event/Adversevent – The National Institute of Standards and Technology (NIST) describes an event as “any observable occurrence in a system or network” and an adverse event as an event with “negative consequence, such as unauthorized use of system privileges, unauthorized access to sensitive data, and execution of malware that destroys data.” For example, a firewall blocking a malicious website that an employee tried to access falls under the event category. With spear phishing attacks increasing, events will likely increase as well. The security you have in place will determine whether an event becomes an adverse-event or not.
Security incident – Security incidents involve confidentiality, integrity, and availability of information. A security incident basically absorbs an event (like a malware attack) and progresses to the point that there is unauthorized information exposure. For example, a malware attack may compromise intellectual property and lead to stolen or copied blueprints.
Privacy incident – According to the U.S. Department of Homeland Security, a security incident upgrades to a privacy incident when Personally Identifiable Information (PII) or Personal Health Information (PHI) is affected. Additionally, privacy incidents can occur offline if physical documents containing PII/PHI are mishandled.
Data breach – A privacy breach magnifies to a data breach when it surpasses the thresholds set by federal/state legislation Under such legislation, entities must notify overseeing bodies, affected customers, and other necessary individuals. Data breaches can be avoided if mitigating steps are taken early on, such as when an event or incident occurs.
Different Types of Data Breaches
Data breaches can be viewed from two angles — how they were perpetrated or the target type. Thus, there is no general consensus on the types of data breaches. The points below look at both angles, including seven types of breaches by attack type and four by the target type. These points represent the common reasons data breaches occur, that is, where the attack progresses to the point that information is disclosed without authorization. However, they are by no means the only attack methods.
Assess your cybersecurity
Attack Types
Physical attack – Physical theft can result in many different outcomes. For example, hard copy data may be stolen directly from a building or an attacker may physically enter the building and connect an unauthorized device, allowing him/her to steal data. Regardless of the variations, the bottom line is that companies need to work just as hard at securing their offices as their cyber environment.
Ransomware – Ransomware is malicious software that blocks access to systems or data until the ransom is paid. Ransomware targets the “access” of information, not necessarily the integrity or confidentiality. However, once a machine or system is compromised by malware, other security issues can arise. Backing up data and implementing a redundancy plan mitigates the impact of ransomware attacks.
Insider threats – An insider threat involves someone internally compromising security. A common insider threat is a disgruntled or bribed employee tasked to steal information, insert malicious hardware, smuggle out devices with sensitive data, or grant physical access to an unauthorized individual. Motivations for these attacks may be emotional, calculated, opportunistic, or terror-related. Training employees to recognize the signs of a potential insider threat, such as working odd hours, nervous behavior, and bringing unrecognized devices to the office, helps identify potential attackers. However, it is also important to maintain a healthy work environment where concerns can be openly addressed. While this will not prevent all insider threats, it gives unsatisfied employees (still working in the office) an outlet to express their concerns rather than turn to illegal activities.
Phishing – Phishing occurs when employees receive emails that appear legitimate but, in reality, come from attackers seeking to exploit an employee’s trust in another company. For example, an attacker may utilize a UPS email address which consumers tend to click on, as they want to track their packages. Spoofing the contact information of trustworthy entities offers threat actors an opportunity to capitalize on consumer trust.
SQL Injection – Netwrix explains an SQL Injection as when an SQL query is sent to the database via the input data from client to server. This can lead to unauthorized modification, deletion, or even issue commands as the administrator.

Target Types
Cybersecurity – Cybersecurity safeguards are vulnerable when attackers target the methods in place that protect computers, networks, programs, etc and use those tools for unauthorized access. For example, a hacker may gain control over an access monitoring system and edit the logs so as to avoid detection. Another option is for an attacker to blatantly break past cybersecurity programs, leaving a company entirely vulnerable. The second option is more unlikely as avoiding detection and potential prosecution is preferable for threat actors.
IT network security – Targeting the network means affecting the rules that ensure the confidentiality, integrity, and accessibility of information. White Hat Security categorizes physical information, data links, networks, transport, sessions, and presentation and application as targets for threat actors looking to weaken network security. Security protocols should be designed to limit/monitor access, particularly when work is done from home or on unsecured networks.
Security information – Targeting the systems or processes that intake, organize, and store information serve as another attack vector. From an attacker’s perspective, this can lead to several end-goals, such as compromising information integrity, stalling operations, or holding information for ransom. The target in this scenario is the Information Security Management System (ISMS) which encompasses the policies and procedures in place to protect/manage data. ISMS not only includes the policies governing how employees handle data but also the threat analysis and asset categorization (i.e., which assets are the most valuable and potential high targets). Combatting a security information attack relies on a pro-active approach.
Protected health information – Protected Health Information (PHI) or Personal Health Information is a constant target because of its critical nature. For example, consider if a hospital’s health records were held hostage by a threat actor. Patient charts listing medication allergies or other vital information may result in lives lost, leading hospitals to try and pay off the perpetrators as soon as possible. However, a payoff is only a temporary fix and may not even succeed in releasing the information. PII, like PHI, is also targeted for similar reasons.
Simple Ways for Consumers to Protect Information
While tightening personal security will not protect your information completely, it will reduce the likelihood that your information is compromised, or it will mitigate the damage when your accounts are compromised. Whitehat Security recommends the following five security measures for consumers:
- Strong passwords – Do not repeat passwords. This point may be overstated, but it’s a simple way to improve the safety of your accounts. Experts suggest at least 8 character passwords with a variety of numbers, cases, and characters. Another option is to use a passphrase, which is often easier to remember. If using a passphrase, look for opportunities to substitute numbers for words within the phrase. For example, the password ItsR8ningCats&Dogs! uses a phrase that is easy to remember, yet includes the complexity requirements.
- Use a credit card – With the amount of online shopping taking place today, the security risks to consumer accounts increased exponentially. Using a credit card when shopping online reduces the risk to your bank accounts. Whereas a debit card connects directly to your main accounts, a credit card has less access and more restrictions. Another good idea if you don’t have a credit card is to use bank accounts, one with money for shopping online and the other for savings (basically a checking and savings account). That way, if one account is compromised, not all your savings are lost. If the online shopping account runs low, simply shift money from savings to checking accounts. In this way, you mitigate a threat actor’s access if your card information is stolen.
- Watch out for fraudulent websites – When shopping online make sure the website looks legitimate. Are there a lot of typos on the website, suggesting it may be a foreign, illegitimate website? Does your security software send a security alert pop-up when trying to access the website? Does the website have a privacy policy and contact information readily available? To learn more about recognizing a malicious website, check out Sitelock’s article on How Can I Tell If a Website Is Safe?
- Use HTTPS – Make sure the website URL shows https. This differs from HTTP in that the “s” means information is protected while in transit from one server to another. Https means the website has SSL (Secure Sockets Layer) certification.
- Set up account alerts – In the age of phone apps, monitoring accounts has never been easier. Banks and other financial institutions offer push notifications that alert you to any potential fraudulent activity. Furthermore, many of the applications enable consumers to shut off account access with a simple touch of a finger. Other services available, such as Google’s new password manager, allow consumers to check if their passwords have been compromised or appear on the Dark Web.
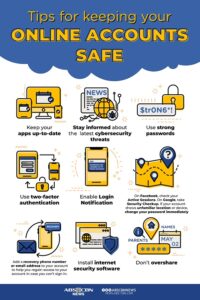
Graphic Source: https://news.abs-cbn.com/business/multimedia/infographic/04/03/19/9-tips-for-keeping-your-online-accounts-safe
How to Combat Data Breaches
Combatting data breaches is extremely difficult. It’s much harder to anticipate an attacker than to be an attacker. Therefore, companies have to be constantly vigilant by learning about the latest technology available and invest in robust security teams. Another first step is to take an asset inventory. Give each asset a vulnerability/threat rating. While anti-virus software is important, endpoint protection is also vital, such as encryption and consistent procedures for device usage. Furthermore, conducting a risk assessment and compliance audit ensures procedures are being followed and kept up-to-date. In conjunction with these reviews, utilize vulnerability and compliance management (VCM) tools. These tools allow for threat classification and easy classification updates. Lastly, training employees may sound less glamorous than the latest penetration testing or threat monitoring technology, but it is just as important. Human error leads to approximately one-quarter of all data breaches, according to a Ponemon Institute Cost of a Data Breach report. Training can range from how to identify suspicious activity to how to create strong password/memorization techniques. Developing materials about how to handle sensitive information and how to properly dispose of it will encourage a standard procedure for dealing with data and PII.
Need Help?
2019 has seen numerous attacks from Facebook’s breach in April compromising 540 million records to First American Financial Corp’s breach in May compromising 885 million users. CNET reported that breaches increased 33 percent in 2019, exposing approximately 7.9 billion records in total. The expenses companies face with these breaches continues to increase with damages including investigation expenses, damage control, repairs, lawsuits, and fines. Unfortunately, the new year will likely bring new attacks and, with more research, reveal the mistakes of the last year. So what can you do? Security breaches come in all shapes and sizes but knowing how attacks work, the potential extent of damage, and the target types will help you avoid data breaches. If you need help conducting a vulnerability assessment, contact RSI Security today for a consultation.
Get A Free Cyber Risk Report
Hackers don’t rest, neither should you. Identify your organization’s cybersecurity weaknesses before hackers do. Upon filling out this brief form you will be contacted by one of our representatives to generate a tailored report.
