History shows that societies with the best cryptography dominate the world. From the ancient Persians, to Germany, to England and the USA, there is at least a strong correlation between the robustness of a societys information security and their resultant global influence & success.
But what does that mean for you and your business? Are you aware that you probably use (or should use) encryption every single day? Data stored on your PCs hard drive is considered at rest – residing in one physical location for most of the time.
Data in Motion is information encrypted & decrypted in transit, over a network, in an authorized session — just as when you connect to your banks website to conduct private / secure transactions.
For Data at Rest, file encryption or Whole Disk Encryption (WDE) is employed. If you use a mobile device such as a smartphone, tablet, or laptop (a near certainty at the time of this writing), we cant stress enough the importance of enabling WDE via (Windows OS) Bitlocker or some other encryption protocol.
That said, a common retort is: I use a strong Windows password, so why do I need to encrypt my device?
The reason your Windows password is insufficient to protect the information stored on the hard drive is because it is only a login password to access the Windows environment.
If your laptop is lost or stolen, the thief / hacker doesnt need your Windows password to get at the data on the hard drive. All they have to do is physically remove the hard drive from the device, connect it to their own computer, and access it as a secondary storage to then read everything on the drive.
Consider whats at risk to your personal or companys security and privacy. Beyond your resume or photos of pets and kids, there exists other data repositories and access points on the hard drive that could provide an onramp to a critical breach.
- Your browser history, cached files, & saved passwords
- The Excel spreadsheet with all login and password credentials to your banks, the IRS, TurboTax, and master Google Account. At this level, thieves can not only access your sensitive accounts, but also control them, given resets to email accounts, 2-factor authentication, etc.
(What of the password that protects your Excel spreadsheet? A determined hacker can crack it under 2 minutes.)
Now that weve convinced you to enable Whole Disk Encryption, heres a primer on how it protects your data.Data is stored on a computer in binary form, 1s and 0s. For instance, the word Security converts to:
0101001101100101011000110111010101110010011010010111010001111001
Now we need a key, for this example Ill use the word Password which converts to:
0111000001100001011100110111001101110111011011110111001001100100
To encrypt, a function called XOR compares 2 digits in the column – if they are the same, make it a 0, if they are different, its a 1.
It looks like this:
0101001101100101011000110111010101110010011010010111010001111001
# Original Data
0111000001100001011100110111001101110111011011110111001001100100
# Key Value
0010001100000100000100000000011000000101000001100000011000011101
# Encrypted value
The encrypted value does not convert to any useful information until you XOR the key again:
0010001100000100000100000000011000000101000001100000011000011101
# Encrypted value
0111000001100001011100110111001101110111011011110111001001100100
# Key value
0101001101100101011000110111010101110010011010010111010001111001
# Original data
This example is very small scale (8 bytes) but your computer does it on large scale and ultimately makes the entire hard drive unreadable. You can tie your encryption password to your windows login so that the whole process is invisible to you, the user.
The process is a little different when encrypting Data in Motion. Since the data is moving and not static, instead of XORing with a key, we XOR with a key-stream. It looks a bit like this:
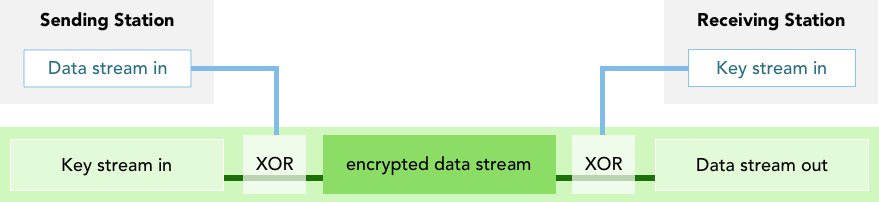
If the data stream is intercepted, its encryption renders it useless to any entity other than the intended receiving station, be it your bank, Amazon, or any site requiring secure communication.
The primary protocol for browser security is called Transport Layer Security (TLS) and its use / implementation is confirmed via display of the padlock icon on the left of the website address.
The current version of TLS is 1.3 and is the most secure. It used to be called Secure Socket Layer or SSL but has been re-branded to TLS. All versions of SSL have been deprecated as well as earlier v1.0-v1.1 of TLS. We recommend to only enable TLS v1.2 (or higher) unless the receiving web site doesnt support it.
Heres how to enable TLS through your browser settings:
https://www.ssl.com/how-to/turn-off-ssl-3-0-and-tls-1-0-in-your-browser/#IE
Until encryption discussions become mainstream, people will continue to think of this vital process as some sort of magical enigma, not well understood and too difficult to implement. By reading this, you now know way more than your friends about encryption and the potential dire consequences if we do without. Spread the word!
About RSI Security
RSI Security is the nation’s premier cybersecurity and compliance provider dedicated to helping organizations achieve risk-management success. We work with some of the world’s leading companies, institution and governments to ensure the safety of their information and their compliance with applicable regulation. We also are a security and compliance software ISV and stay at the forefront of innovative tools to save assessment time, increase compliance and provide additional safeguard assurance. With a unique blend of software based automation and managed services, RSI Security can assist all sizes of organizations in managing IT governance, Risk management and compliance efforts (GRC).



