Consumers and employees expect access at all times, which relies on data centers operating 24/7. But if data center security measures aren’t strong, operational reliability is called into question. Over the years, the methods for establishing, monitoring, and upkeeping data centers should have evolved as technology did. Yet, a 2018 Gartner report found that approximately 70 percent of data center networking tasks are performed manually, which increases time, cost, and the likelihood of errors, and reduces flexibility. Foregoing automation and other new safeguards in exchange for outdated methods put data centers at risk. Learn about the critical data center security requirements that will keep hackers out now – and well into the future.
Data Centers 101
Data centers, sometimes called server farms, house computer and network equipment in a centralized location. These centers assist in storing, transmitting, collecting, and processing data. Early data centers housed one or two supercomputers, but today, these centers house thousands of servers connected to networks all operating on a 24/7 basis. Because of their storage capacity, data centers play a critical role in redundancy and data recovery.
Types of Data Centers
Data centers are used by everybody, but how they are implemented and monitored varies. Some companies build and maintain data centers internally. A second option is to rent servers at colocation centers or colos. A third option relies on public cloud-based services, such as Amazon or Microsoft. Data centers exist on all different scales. Those operating tens of thousands of servers are referred to as hyper-scale data centers, often operated by large tech companies and the government. As the hunger for information grows, the number of hyper-scale centers grows. According to 2019 data, over 500 hyper-scale data centers now exist globally, with the greatest concentration in the US.
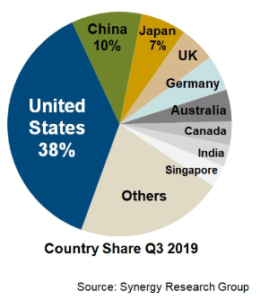
Image Source: Distribution of hyper-scale centers around the world. https://www.datacenterknowledge.com/cloud/analysts-there-are-now-more-500-hyperscale-data-centers-world
Building and Maintaining a Data Center
The security of data centers depends on logical thinking and projections as to how a company may expand in the future. The various options in scale and structure of data centers mean companies must choose carefully before endeavoring to build or rent a data center. Things to consider are:
- Size
- Location
- Type of content
- Security
- Cooling
- Power
- Redundancy
How to Choose a Location
The first question to answer is, would it be more beneficial to build a data center or rent space? If you decide to build your own data center, the next question to answer is, where? Depending on budget limitations, companies can either construct a brand new facility or retrofit an existing building.
- Companies should survey areas closely to avoid flood plains or areas prone to seismic activity.
- Make sure to choose a location that addresses any plans to expand in the future
- If retrofitting an existing building, engineers should confirm the structural integrity and load-bearing capacity of the floor and roof, which will hold the weight of cooling units.
Schedule a Free Consultation!
Protecting Energy Sources
Without a secure power source, data centers become vulnerable. Powering a data center involves dedicated transformers, uninterrupted power supplies (UPS units), and Automatic Transfer Switches (APS). UPS units provide power if commercial power fails, while also providing surge protection, even electricity distribution, and electrical load optimization. Backup systems serve as the baseline tenant for securing data centers, such as a diesel generator connected to the APS or batteries attached to the UPS units.
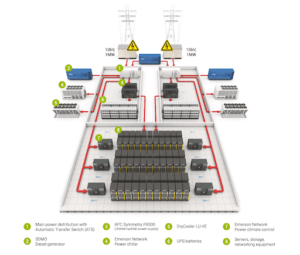
Image: Example of Data Center Power Distribution
Source: https://www.deac.eu/data-centers/power-supply/power-supply-2/en/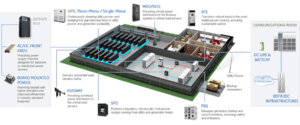 Image: GE’s Critical Power Data Center Application
Image: GE’s Critical Power Data Center Application
Source: https://industrialsolutions.ca.abb.com/print/node/4742
Cooling Optimization
Since data centers house thousands of machines, keeping temperatures stable is vital to maintaining normal operations. Some common optimization options are hot/cold aisles, double flooring, and the free-cooling method.
Hot/Cold Aisles: Aligning server racks to create cold and hot aisles, also called, the front-to-back system, improves cooling efficiency and lowers cooling costs. This design is more practical if building a data center from scratch rather than retrofitting one. Retrofitting will cost more because companies will have to re-align the layout to accommodate hot and cold airflow.
Double flooring: Another common optimization technique is double flooring, which channels the cool air to the necessary areas and protects metallic cabling.
Free-Cooling: The free-cooling method, a current trend in data center construction, utilizes the cold air outside the facility to lower internal temperatures. This method works particularly well when a facility is in a region with cool temperatures. The equipment needed for the free-cooling method may reach beyond that of small companies. In such cases, using a standard direct expansion (DX) air conditioning unit will suffice. However, DX units are not cost-effective in the long-term. Monitoring energy consumption and temperature fluctuations help determine how to improve the design and maximize energy consumption.
Natural Disaster Considerations
Regardless of where a data center is located, natural disasters can occur. To protect against environmental damage use fire alarms, fire extinguishers, and heat detection systems. Higher-end systems auto-detect fire and disperse inert gases to extinguish the fire, which protects the machines, unlike other water-based extinguishing systems.
Data Center Security Requirements
Data center security focuses on three goals: prevent unauthorized access, inhibit data manipulation, and maintain operations. Ransomware, external human threats, advanced persistent threats, internal human threats, and DDoS attacks are just a few of the common attack methods used to breach data center security. The bottom line is, criminals will always target the applications and information in data centers. As a result, it’s crucial that data center security standards evolve as threats evolve.
Physical Security
Since data centers are first and foremost physical entities, any security strategy should start with physical security measures. These measures must protect the integrity and structure of the machines operating in the data centers. Threats against data centers are not always malicious. Although espionage or terror attacks may target data centers, a natural disaster could also disrupt operations. Although companies should tailor their security policies and procedures to their needs, File Bridge recommends the following physical security measures as a starting point:
- Three-Factor authentication: Proximity Card/Biometric fingerprint reader/facial geometry scanner
- Anti-tailgating/Anti-pass-back turnstile gate. Only permits one person to pass through after authentication
- Single entry point into colocation facility
- Access to a private cage requires additional two-factor authentication consisting of biometric fingerprint scan and proximity card
- SSAE 16 (formerly SAS70 Type II) compliant facilities
- 24/7 on-site security
- High definition CCTV of all interior and exterior strategic locations and access points with 90-day video retention
Digital/Virtual Security
One of the leaders in security standards is the National Institute of Standards and Technology (NIST). NIST’s data center cybersecurity recommendations are woven throughout several different publications. They apply to both government agencies and private sector entities.
- NIST 800-53 covers security controls for real-time monitoring and privacy considerations.
- NIST 800-30 provides steps for conducting a risk assessment and understanding how high a threat is and what the impact would be if it occurred.
- Other NIST publications relating to data centers include ISO 27001 and Federal Risk and Authorization Management Program (FedRAMP).
Beyond NIST’s in-depth guides, there are several minimum security measures all data centers should implement, focusing on monitoring, access, and testing. In addition to its physical security checklist, File Bridge also published a digital security checklist broken down into two categories: data-at-rest and data-in-transit.
Data In Transit
- 256-bit SSL encryption for web applications
- .1024-bit RSA public keys for data transfers
Data At Rest
- AES 256-bit encryption for files and databases
- Audit logs for all user activities
- Secure usernames and passwords
- Encrypted via 256-bit SSL
- Password complexity requirements
- Scheduled expiration
- Restricted password reuse.
- Role-based access controls
- AD/LDAP integration
- IP address-based access control
- Encrypted session ID cookies to uniquely identify each user
- Two-factor authentication availability
- Third-party penetration testing performed annually
Data Center Security Tips
- Implement a layered security approach. Using this process forces intruders to penetrate multiple layers of security, taking more time and effort and will potentially alert security teams to a breach.
- The “Zero Trust” security philosophy means that every individual faces the same access scrutiny no matter their status. Keeping meticulous access lists and continuously updating them as needed aids in identifying any suspicious activity.
- Take advantage of existing and emerging technology. Biometrics, RFID tagging, and CCTV surveillance are just a few of the options to secure data centers. As technology and authentication methods evolve, companies should upgrade their systems and hardware when possible.
Data Center Compliance
Since each data center houses different applications and information, not every data center will need to follow the same compliance standards.
Progression of Standards
In 2010, the industry retired standard SAS 70 in exchange for SSAE 16 and later SSAE 18. SAS 70 was largely an auditing process, whereas SSAE 16 was a written affirmation confirming that security controls were effective and resulted in a SOC 1 report. It was not a certification to be achieved but lends credibility.
In 107, SSAE 18 became the new standard and provided a more rigorous certification process.
- Uses the risk assessment process similar to SOC 2 certification
- Includes a clause addressing Sub service Organization Controls and third-party vendors
- Stresses the importance of monitoring programs
Is Compliance Optional or Required?
Some compliance certifications, such as SOC 1, 2, and 3, are optional. Which of these a company chooses to conduct will largely depend on what its data center is used for. In contrast, HIPAA and PCI DSS compliance are required when health data or financial data are involved, respectively.
SOC 1 – Defines internal controls and maps a data center’s control structure. This report would be beneficial for SaaS and technology companies who interact closely with their clients, but it does not apply to colocation centers. The involvement of customer financial applications or underlying infrastructure requires a SOC 1 report to be conducted.
SOC 2 – If financial applications are not involved but colocation centers or environmental controls are, a company should conduct a SOC 2 report. A SOC 2 report follows the Five Trust Service Principles and is more complex than a SOC 1 report.
SOC 2 compliance reviews:
- Internal access controls
- Monitoring tools
- Reporting tools
- Requires an audit
SOC 3 – Like SOC 2, SOC 3 certification requires an audit but does not include a report or testing tables. Consumer-oriented data centers should consider this report as it allows them to use the SOC 3 logo and thereby boost consumer confidence.
Payment Card Industry Data Security Standard (PCI DSS) – PCI DSS protects cardholder information. Companies conducting online monetary transactions must be PCI DSS compliant. PCI DSS follows 12 principles all of which must be followed by data centers and verified by providing an independent audit to the PCI Security Standards Council. The Council released an updated version 3.2 in 2016.
Health Insurance Portability and Accountability Act (HIPAA) – Data centers must comply with HIPAA if they store or handle Protected Health Information (PHI) or Electronic Protected Health Information (ePHI). This includes Business Associates. HIPAA’s Privacy Rule, Security Rule, and HITECH Act address cloud storage and data management best practices.
The Cloud and Data Centers
With cloud computing, a company relies on the cloud provider’s data centers and does not have control over data center security. Cloud providers often partner with third parties to manage data centers, adding another layer of risk. This risk does not negate the many benefits of cloud services, but it does change how you should approach cybersecurity measures.
- Make sure that the cloud provider you choose offers the level of security you need.
- Inquire about third party usage, which may affect internal risk assessments.
- Determine which type of cloud best fits with your needs. Private clouds, when compared to public clouds, offer companies more control and typically more security oversight.
- Consider cost benefits. Cloud services cost far less than building and maintaining an on-prem data center.
Need Help?
Data center security requirements will vary based on what the center is used for, the location, and the size. Whether building a data center from scratch, renting space, or retrofitting, it’s vital that companies take a holistic and measured approach to the process. If you need help developing a security plan for your data center, whether already constructed or at the conceptual stage, contact RSI Security today.
