The Cybersecurity Maturity Model Certification (CMMC certification) is designed to simplify compliance for companies handling Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) across the Department of Defense (DoD) supply chain. For a detailed explanation of what qualifies as CUI, refer to the Organization Index Grouping of Defense.
Currently, Draft v0.7 of the CMMC is available, with the final version (v1.0) expected in January 2020. Companies are encouraged to review v0.7 to begin preparing for the level of DoD CMMC certification required for project bids.
Draft v0.7 is accessible online in its entirety. Below is a concise summary of its contents, along with insights from Katie Arrington, Special Assistant to the Assistant Secretary of Defense for Acquisition for Cyber, as presented in her webinar “What Contractors Need to Know About DoD’s CMMC” (July 17, 2019). Note: You must be signed in to view the webinar.
During the webinar with the Professional Services Council, Katie Arrington highlighted that losses from inadequate cybersecurity controls leading to CUI breaches amount to over $600 billion annually. While achieving DoD CMMC certification may incur costs, the long-term savings outweigh these expenses. Additionally, the government considers CMMC certification costs as allowable expenses in its bidding process. The Request For Information (RFI) and Request For Proposal (RFP) Sections L and M outline the required level of CMMC certification, which can determine eligibility for project bids.
CMMC Certification Levels: What DoD Contractors Need to Know
The CMMC certification process requires companies to comply at different levels depending on the sensitivity of the information and products they handle along the DoD supply chain. It is estimated that over 300,000 businesses, both small and large, will need this certification. This includes any company directly contracting with the DoD or subcontracted by a DoD contractor.
The new process aims to simplify compliance by consolidating existing standards such as NIST SP 800-171, NIST SP 800-53, FedRAMP, ISO 9000, and others.
As stated in CMMC Draft Version 0.7 (Dec 6, 2019):
“The CMMC effort builds upon existing regulation, specifically 48 Code of Federal Regulations (CFR) 52.204-21 and Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012, and incorporates practices from multiple sources such as NIST SP 800-171 rev 1, Draft NIST SP 800-171B, the United Kingdom’s Cyber Essentials, and Australia’s Essential Eight.”
Third-party companies will offer DoD CMMC certification, under the oversight of an independent nonprofit designated by the DoD. Although the nonprofit designation has not yet been announced, it is expected that companies already certifying compliance with existing standards will participate in this new process. The nonprofit will train auditors and certifiers to ensure adherence to CMMC certification requirements.
Companies like RSI Security, which specialize in remediation and standards implementation, can assist other businesses in achieving the required level of certification. CMMC levels range from 1 to 5, with Level 5 being the most stringent and Level 1 the least.
The levels are designed to align certification requirements with the type of CUI handled. For instance:
- A vendor sewing eyelets onto military boots may only need Level 1 certification.
- A manufacturer producing and shipping the complete boots would require a higher-level certification to protect the associated CUI.
It’s important to note that both practices and processes must meet the same certification level. If they differ, the overall CMMC certification is awarded at the lower level. Additionally, each level builds upon the previous one: all requirements from lower levels must be met in addition to the new requirements for the desired higher level.
Download our CMMC Whitepaper: Best Cybersecurity Practices for DoD Contractors
Level 1: Basic Cyber Hygiene
CMMC certification Level 1 focuses on basic cyber hygiene and is grounded in 48 CFR 52.204-21. This level establishes foundational requirements that all companies in the DoD contractor supply chain within the Defense Industrial Base (DIB) must meet.
At Level 1, there is no process maturity requirement, the emphasis is on implementing essential cybersecurity practices to protect Federal Contract Information (FCI) and other sensitive data.
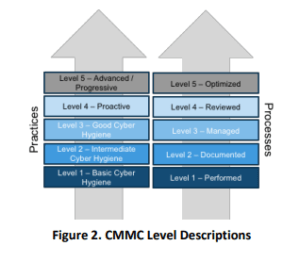
Image is from Cybersecurity Maturity Model Certification (CMMC) DRAFT Version 0.7 December 6, 2019, page 2.
Level 2: Intermediate Cyber Hygiene
CMMC certification Level 2 builds upon Level 1 and introduces a higher degree of cyber hygiene. At this level, companies must not only implement security practices but also document their processes, including Standard Operating Procedures (SOPs), policies, and strategic plans.
This documentation ensures that cybersecurity measures are repeatable, measurable, and auditable, providing a more mature approach to protecting Controlled Unclassified Information (CUI) within the DoD contractor supply chain.
Level 3: Good Cyber Hygiene
CMMC certification Level 3 requires companies to adhere to all security control requirements outlined in NIST SP 800-171 Rev 1. Any organization that handles Controlled Unclassified Information (CUI) must achieve Level 3 certification. Additionally, companies subject to DFARS clause 252.204-7012 must comply with those requirements, including incident reporting.
At this level, companies also follow a CMMC process maturity model, which ensures that audits of policies and procedures are in place. This combination of technical controls and process maturity provides a robust framework for protecting sensitive DoD information.
Level 4: Proactive Cybersecurity
CMMC certification Level 4 is for companies that demonstrate a proactive approach to cybersecurity. At this level, organizations adapt their protection and sustainment activities to defend against Advanced Persistent Threat (APT) tactics, techniques, and procedures.
Level 4 also emphasizes process maturity through reviews. Documentation from these reviews informs upper management of security gaps or issues requiring remediation, helping the organization continuously strengthen its cybersecurity posture.
Level 5: Advanced Cybersecurity
CMMC certification Level 5 represents the most advanced level of cybersecurity maturity. Companies at this level are responsive and adaptable, using optimized cybersecurity controls to defend against Advanced Persistent Threats (APTs).
At Level 5, process maturity is fully achieved. Organizations that are DoD CMMC certified at this level have standardized and uniformly implemented processes across their entire company, ensuring maximum protection and operational consistency.
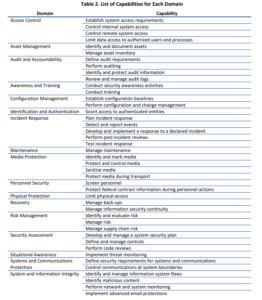
Image is from Cybersecurity Maturity Model Certification (CMMC) DRAFT Version 0.7 December 6, 2019, page 6.
Organization and Compliance to DoD CMMC Certification Requirements – Domains
CMMC certification requires companies to implement practices and processes across 17 domains, each critical to protecting Controlled Unclassified Information (CUI). These domains include:
- Access Control (AC)
- Asset Management (AM)
- Audit and Accountability (AA)
- Awareness and Training (AT)
- Configuration Management (CM)
- Identification and Authentication (IDA)
- Incident Response (IR)
- Maintenance (MA)
- Media Protection (MP)
- Personnel Security (PS)
- Physical Protection (PP)
- Recovery (RE)
- Risk Management (RM)
- Security Assessment (SAS)
- Situational Awareness (SA)
- System and Communications Protection (SCP)
- System and Information Integrity (SII)
Each domain contains cybersecurity capabilities, though not all capabilities require practices at every level of DoD CMMC certification.
The specific practices required for each domain are detailed in Appendix A of the CMMC Draft Version 0.7 (Dec 6, 2019). This blog highlights a few examples to help companies understand the types of practices required at different certification levels.
To interpret Appendix A charts:
- Locate the control domain of interest.
- Scroll down to find the capability requiring compliance.
- Move across to identify the DoD CMMC certification level sought.
- Record all practices for that capability at every level, remembering that higher-level certifications include all lower-level practices.
Some capabilities may not require practices at all levels, so blank cells are normal.

Example: Domain AC – Access Control Practices
An example of preparing for DoD CMMC certification could focus on Domain AC (Access Control), specifically the capability C002: Control Internal System Access. For instance, a company handling nonpublic sensitive FCI and CUI may aim for Level 5 certification.
Level 1 practices for this capability include:
- P1002: “Limit information system access to the types of transactions and functions that authorized users are permitted to execute.”
- Informed by FAR Clause 52.204-21 b.1.ii and NIST SP 800-171 3.1.2.
All Level 1 practices must be included in higher levels (Levels 2–5).
Level 2 practices add five more requirements:
- P1007: Employ the principle of least privilege, including for privileged accounts (informed by NIST SP 800-171 3.1.5, UK NCSC Cyber Essentials).
- P1008: Use non-privileged accounts when assessing non security functions (NIST SP 800-171 3.1.6, UK NCSC Cyber Essentials).
- P1009: Limit unsuccessful login attempts (NIST SP 800-171 3.1.8).
- P1010: Use session lock with pattern-hiding displays after inactivity (NIST SP 800-171 3.1.10).
- P1011: Authorize wireless access prior to connections (NIST SP 800-171 3.1.16).
Level 3 practices include:
- P1017: Separate duties to reduce risk of malevolent activity (NIST SP 800-171 3.1.4).
- P1018: Prevent non-privileged users from executing privileged functions and capture these actions in audit logs (NIST SP 800-171 3.1.7).
- P1019: Terminate user sessions automatically after a defined condition (NIST SP 800-171 3.1.11).
- P1012: Protect wireless access using authentication and encryption (NIST SP 800-171 3.1.17).
- P1020: Control the connection of mobile devices (NIST SP 800-171 3.1.18, UK NCSC Cyber Essentials).
Level 4 practices include:
- P1023: Control information flows between security domains on connected systems (NIST SP 800-171B Partial 3.1.3e).
- P1025: Periodically review and update CUI program access permissions (CMMC committee guidance).
Level 5 practices include:
- P1024: Identify and mitigate risks associated with unidentified wireless access points connected to the network (CIS Controls v7.1 15.3).
This example demonstrates how CMMC certification builds upon practices incrementally from Level 1 through Level 5, ensuring comprehensive security controls aligned with NIST SP 800-171 and other recognized standards.
Example: Domain AM – Asset Management Practices
Another example of DoD CMMC certification preparation is Domain AM (Asset Management), specifically Capability C006: Manage Asset Inventory.
For this capability:
- Levels 1–3: No practices are required. Companies seeking CMMC certification at these levels do not need to implement any practices for this capability.
- Level 4: Practice P1226 is required. This practice instructs companies to:“Employ automated capability to discover and identify systems with specific component attributes (e.g., firmware level, OS type) within your inventory.”
This practice is informed by CMMC modifications of NIST SP 800-171 3.4.3e.
- Level 5: No additional practices are required beyond Level 4. Companies seeking Level 5 certification for this capability only need to adhere to P1226.
This example illustrates that CMMC certification requirements vary by domain and capability, and not all levels require practices for every capability. Understanding which practices apply at each level is essential for efficient compliance planning.
Get Help with DoD CMMC Certification Requirements
The goal of CMMC certification is not to add unnecessary burdens to private-sector contractors in the Defense Industrial Base (DIB). Instead, it is designed to simplify and streamline compliance, making the process more efficient for everyone involved. With implementation starting in some RFIs as early as June 2020, and the final regulations coming in January 2020, the time to begin certification preparations is now.
It is important to note that the CMMC outlines WHAT practices companies must implement, but it does not explain HOW to implement them. That’s where cybersecurity solutions experts like RSI Security become essential. RSI Security specializes in preparing companies for CMMC certification, guiding them to achieve the desired DoD CMMC certification level efficiently and effectively.
Contact RSI Security today to learn how you can make your business more secure and profitable while meeting all necessary CMMC compliance requirements.
Download Our CMMC Checklist
