Last week, the Colorado Department of Transportation was hit with the SamSam ransomware forcing it to shut down 2000 computers across its system. Believed to be a new variant of the previous SamSam ransomware, according to Talos Intelligence at Cisco, this ransomware has been observed across multiple industries including Government, Healthcare and ICS. These attacks do not appear to be highly targeted, and appear to be more opportunistic in nature. As we all know these ransomware can cripple critical systems such as those in the healthcare services impacting patients across the world.
Whats different this time?
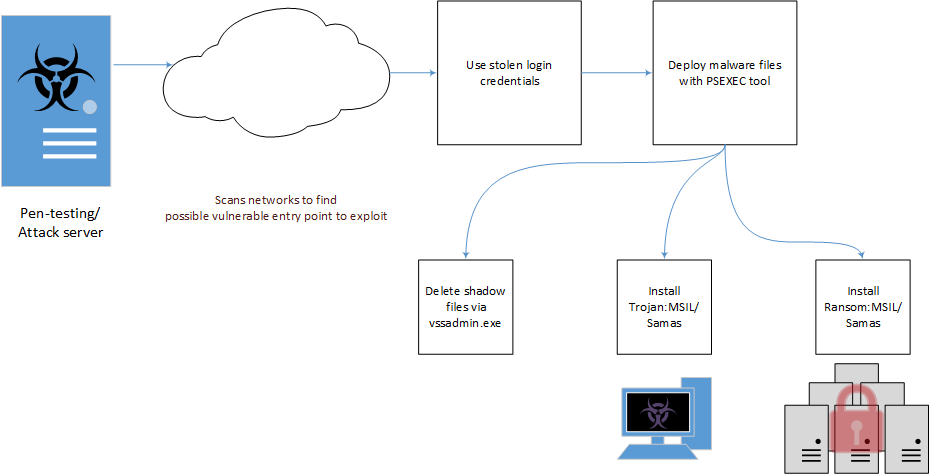
The SamSam or Samas infection chain diagram below illustrates how Ransom:MSIL/Samas gets into the system. There is a possibility that compromised RDP (Remote Desktop Protocol)/VNC (remote access software) servers have played a part in allowing the attackers to obtain an initial foothold. RDP/VNC software functionality allows a remote user to login to a system.
- Start with a pen-testing/attack server searching for potential vulnerable networks, looking for open RDP connections.
- Apply brute force password discovery methods to steal credentials and login into the system. A brute force attack consists of an attacker trying many passwords or passphrases with the hope of eventually guessing correctly
- Deploy, install and execute ransomware
Best practices to protect systems against this kind of Ransomware
- Turn off the RDP functionality if it’s not required
- Protocols like SMB or RDP should never be internet facing
- Minimize and restrict system administrative accounts. Remove default user accounts on the system
- Establish strong password policy and set lockouts in order prevent brute force attacks
- Consider VPN (virtual private connection) to connect to enterprise systems from outside.
- Opt for 2-factor authentication, an extra layer of security, with a 2-step verification that requires a piece of information that only, an authorized system user has.
- Disable loading of macros in Microsoft Office programs
- Disable macro loading via Group Policy settings
- Keep your systems up to date with relevant patches
- Establish a strong systems/data backup policy so that systems can be restored in the event of an attack
- Establish continuous security awareness among all employees and business partners
Sources:
http://blog.talosintelligence.com/2018/01/samsam-evolution-continues-netting-over.html
https://nakedsecurity.sophos.com/2017/11/15/ransomware-spreading-hackers-sneak-in-through-rdp/
https://cloudblogs.microsoft.com/microsoftsecure/2016/03/17/no-mas-samas-whats-in-this-ransomwares-modus-operandi/?source=mmpc
About RSI Security
RSI is the nation’s premier information security and compliance provider dedicated to helping organizations achieve risk-management success. We work with some of the world’s leading companies, institution and governments to ensure the safety of their information and their compliance with applicable regulation. We also are a security and compliance software ISV and stay at the forefront of innovative tools to save assessment time, increase compliance and provide additional safeguard assurance. With a unique blend of software based automation and managed services, RSI can assist all sizes of organizations in managing IT governance, Risk management and compliance efforts (GRC).


Get A Free Cyber Risk Report
Hackers don’t rest, neither should you. Identify your organization’s cybersecurity weaknesses before hackers do. Upon filling out this brief form you will be contacted by one of our representatives to generate a tailored report.

