In today’s business environment, a network serves as the operational glue holding the company together. It enables communication, collaboration, and data storage. However, if that “glue” isn’t strong, it weakens a company’s infrastructure, endangering critical assets. From remote workstations to personal devices, the multifaceted nature of a network means the threats are ever-evolving. Learn about the different components of network architecture with our informative guide. Discover more here.
Networks 101
Two or more computers that communicate to share resources, messages, or exchange files are considered a network. A typical example would be two computers sending emails over the network, but networks go beyond exchanging communicative messages to more command-like functions. For example, a wireless printer (a resource) may receive a command from a computer over a network, either with a direct connection or wirelessly. Networks enable shared storage across multiple devices.
Understanding different network types and what they share or store will help assess what potential targets and how a threat actor might conduct an attack. For example, infiltrating a minor network may lead to larger network access. The two most well-known types of networks are a Local Area Network (LAN) and a Wide Area Network (WAN), but more network options have emerged as technology has improved. Below is a quick guide to each type of network.
Basic Network Types
Local Area Networks
Local area networks cover small geographical areas, such as rooms or buildings. Servers, workstations/desktops, and laptops will be connected via cables or use Wireless Access Points (WAPs).
Wide Area Networks
Wide area networks extend between larger geographical swaths, like counties, states, and countries. Generally, WANs rely on transoceanic cabling or satellite uplinks. The equipment infrastructure necessary for WANs is more complex and utilizes many multiplexers, bridges, and routers. However, WANs are not independent of LANs; rather, WANs build off of LANs and metropolitan networks.
Assess your Network Security
Other Network Types
Beyond these common types, others include Personal Area Networks (PANs), Metropolitan Area Networks (MANs), Storage Area Networks (SANs), and Campus Area Networks (CANs). It’s important to cover the basic network terminology because many company networks are complex and include a variety of different network types.
Personal Area Network – PANs cover very small distances, even less than local networks, and, as the name indicates, are personal to a user. PANs can connect to other devices through Bluetooth, infrared, Near Field Communication (NFC), or a wired connection. PANs are suitable for small file-sharing, such as music.
Campus Area Network – CANs join two or more LANs together in a limited area that then forms a larger network. These may be present at college campuses or a company campus/complex.
Metropolitan Area Network – MANs span the distances between city government buildings. Connectivity stems from a high-speed connection, such as fiber-optic cables. Thus, city resources are easily shareable within different departmental facilities.
Storage Area Network – SANs refer to dedicated, high-speed networks used for data storage. They include multiple switches, servers, and disk arrays. Because of their partitioned nature, SANs offer the benefit of avoiding high-traffic backups that LANs sometimes experience.

Network Architecture Options
The architecture of a network depends on how computers are organized and how tasks are distributed to those devices. A network architecture rendering, often helpful when conducting a threat assessment, may include the transmission equipment, software, and communication protocols, and infrastructure (wired or wireless) that enables devices to communicate and transfer data. The two most common architecture types are Peer-to-Peer (P2P) and tiered, also referred to as client-server. However, thin-client networks are gaining popularity, especially when it comes to securing personal work devices.
Peer-to-Peer – This type of architecture treats all devices equally. Tasks are allocated equally without a hierarchy, which is why P2P can also be called a distributed network. Rather than relying on a central server, each computer possesses software enabling communication. One benefit of this arrangement is that if one device fails, others will still maintain the network of communication. Peer-to-peer architecture caters specifically to file sharing.
Tiered – In a tiered network, also known as a client-server network, the clients are the computers and the computers depend on the server. The network server(s) manages the data and distributes it based on client requests. Some servers focus on one type of task, such as email or printing, while others support multiple services. The network servers utilize their own operating systems and have more processing and storage capacity compared to regular computers. Within a tiered network, if a server goes down, clients are more vulnerable because the network is not as distributed as in a P2P network.
Thin-Client Network – This architecture gives the server more responsibilities, such as running applications for the clients. Rather than the software running on the client, the server runs the programs and the client’s main job is simply to display and accept inputs. For example, users would access a virtual machine on their device but none of the applications are actually run on the personal device. Because of this, thin-client architecture offers more security and protection for proprietary information. While the initial upfront cost of switching to a thin-client architecture can be significant, the manageability it provides makes it worth the cost for large companies.
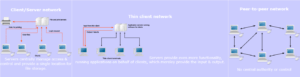
Image Source: https://sites.google.com/site/mrstevensonstechclassroom/home/strand-3-it-systems/3-3-networks/client-server-networks
Components of Network Architecture
Whether building a network or updating network security, knowing and assessing network architecture components will help IT teams evaluate the weak links or discover new ways to improve network functionality.
Essential Network Components
Switches – Switches connect devices, allowing them to communicate over the network. On-premise and cloud-based switches are the two main options. An on-premise switch requires a company/IT department to configure, maintain, and monitor the LAN, giving companies greater control over their network operations. For larger companies, this is completely feasible, but smaller companies may be better off using a cloud-based switch, where a cloud provider manages it, pushes updates, and provides a user interface.
Routers – Routers connect networks and devices on the networks to the Internet. This means instead of each device having a direct connection, multiple devices, via the router, share one Internet connection. A router also determines the best route for data transmission by analyzing other data traveling over the network. The router has the power to prioritize certain computers. More complex routers allow consumers and companies to use a built-in firewall or VPN.
Wireless Access Points (WAPs) – WAPs allow devices to connect to the Internet without a cable, making it easier to add multiple devices or move about within a building. Routers provide the initial bandwidth, but WAPs expand the covered area. Additionally, WAPs show data about connected devices, which can be used for security assessments.
Here are a few more articles to help you:
Other Odds and Ends
While the above three architecture components compose the core of a network, other components often come up when discussing network security.
Repeaters – Repeaters regenerate network signals that are distorted. They also relay messages between subnetworks and may be analog or digital. While an analog repeater mainly amplifies a signal, a digital repeater has better quality and can almost duplicate a signal to the original level.
Hubs – Hubs allow computers to talk with each other; however, they do not perform any complex tasks. Hubs must be physically plugged into the network with a wired connection.
Bridges – Bridges divide a LAN into multiple segments and assist in reducing traffic. They store the addresses of devices and know which segment they are in. As a result, when a computer tries to send information to another computer, the request is first sent to a bridge, which then determines the segment in which the recipient computer is located.
Evolving Network Architecture
Network architecture matters not just for internal operations but also for consumer interaction with companies. Consumerization and increased use of technology have made it crucial that companies provide platforms that are user-friendly and, for the most part, glitch-free. Consumers do not want slow and cumbersome shopping experiences or processes that require many steps. For example, many companies now offer auto fill-in capabilities so repeat customers have less hassle when checking out. Cloud architecture enables better market agility through traffic partitioning.

Cloud Architecture
When constructing a network, ORACLE recommends studying the different traffic patterns over the network. Cloud computing offers many benefits, but if constructed poorly, a cloud infrastructure can be inefficient. For example, a single network interface used with a multi-node configuration will not be able to accommodate high cloud network traffic. Utilizing different networks/subnetworks to isolate traffic maximizes efficiency and improves functionality. Types of traffic may include guests, storage, or management.
Benefits of Traffic Partitioning
Network reliability and availability – Integrating multiple networks reduces the likelihood of total network failure that can occur with single-network configurations. If an issue occurs in a single-network configuration, all traffic may cease or be compromised.
Performance and scalability – Unlike a single network interface, multiple interfaces guide network traffic routes while decreasing network congestion and improving overall performance, both qualities consumers highly value.
Security – Network separation is more beneficial than a single network traffic flow because that architecture enables IT managers to isolate a security issue more easily. Additionally, if a security breach occurs, some operations/traffic may remain functional while the vulnerable section is dealt with.
Manageability – Network management becomes easier the more organized you are. For example, a personal planner with daily columns and sections provides greater organization than one with only a large block of blank space. It’s easier to manage tasks when they are clearly categorized.
How to Design a Secure Network
Just as consumers highly value efficiency and reliability, they also expect companies to implement secure networks. The Internet is an integral part of any functioning business in modern society, but connecting to it adds a door for hackers to potentially enter. Consequently, security should be at the forefront when considering network infrastructure. The Infosec Institute offers the following suggestions when designing a network with security in mind.
- Don’t overlook the supposedly insignificant. This means that even simple information or policy pages can be weak links in a network’s architecture. Areas of a network that consumers overlook may be a prime target for hackers.
- Implement fail safes. When developing a network architecture, implement fail-safes so that if systems fail information and company applications do not become vulnerable at the same time.
- Limit access. While it may be easier to grant total access to an individual or entity, it’s not secure and goes against the least privilege model. If a third-party needs network access, only grant them access for what they need or the least amount of access necessary. Then, if a security risk occurs, the vulnerability will hopefully not endanger the entire network.
- Encryption – Encryption should be included in any network security model. Moreover, many compliance models list encryption as a requirement. Typically, encryption occurs over the network layer of the Open System Interconnection (OSI) model but on an IP-based network, the network encryption process will involve IP protocols and keys versus the OSI algorithm process.
- Test before total implementation. Once a network is set up the work isn’t over. Companies should run vulnerability tests to ensure major vulnerabilities are addressed prior to the network going live.
Network Security Checklist For Personal/Small Businesses
Network security isn’t just something for companies to consider. Consumers can also take proactive steps to safeguard their networks. PC Magazine recommends the following steps for securing a home network.
- Change your router admin username and password
- Change the network name
- Activate encryption
- Double up on firewalls
- Turn off guest networks
- Update router firmware
These considerations apply to small businesses as well. For example, a cafe offering WiFi should reset passwords frequently and use a separate network for business operations.
For Larger Companies
Penetration testing and computer forensics will help strengthen network security. The following categories provide a baseline for conducting a network security audit.
- Policies – including network configuration, patching
- Provisioning Servers
- Deploying Workstations
- Network Equipment
- Vulnerability Scans
- Redundancy
- Remote Access
- Wireless networking – such as guest networks, BYOD procedures, and encryption
- Internet Access
- File Sharing
- Server Log Monitoring
Need Help?
Insecure networks grant hackers access to company information, consumer PII, or government platforms. With network access, hackers have the opportunity to gain leverage and potentially blackmail or sell that information. Taking preventative measures to prevent unauthorized access to computers and information should be a core aspect of any well-rounded cybersecurity policy. If you need help implementing a secure network architecture, contact RSI Security today.

1 comment
I would like to thank author of this blog for representing the whole topic with meaningful content and insight. As a blogger i must say that you correctly described various network components here. So i would like hear more such content from you in upcoming days.