The times of vertical management no longer serve as the best option for efficiency and cost-effectiveness. Companies rarely control every aspect of their supply chains and now use third parties to fill knowledge, time, or money gaps. But with outside assistance comes more risk. In relation to cybersecurity, third parties have become especially helpful for conducting security assessments, monitoring networks, expanding services offered. However, establishing a third-party partnership doesn’t happen overnight. Learn about the third-party risk management process and lifecycle here.
Why Management Matters
Vetting a third party prior to signing a contract is not enough on its own. The process doesn’t end there. A third party partnership requires oversight and communication as long as the relationship exists. Companies that hire third parties assume responsibility for their actions and any mistakes or infractions that occur. The generally accepted position is that you know who they are, you have vetted them and you are in control of the activities for which you hired them. If a third party fails to comply with industry standards, engages in any unethical business practices, or experiences a security breach, the hiring firm will likely be impacted and even receive the majority of the blame for lack of third-party oversight.
Defining Third Parties
Today, a business’s environment includes an “extended enterprise.” Suppliers, support service providers, sales agents/distributors, and affiliated organizations. An extended enterprise encompasses anything from an alliance to a joint venture to a subsidiary. As globalization continues, the third-party network becomes more complex. The benefits of third parties are numerable including lower costs, access to scarce knowledge, and improved strategic agility, but with the benefits comes a responsibility to implement proper oversight.
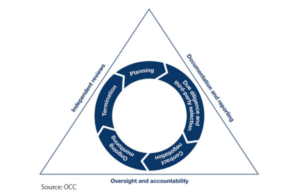
Third-Party Risk Management Lifecycle
Lifecycles are rarely identical because each entity has a different perspective, and it’s no different from a third-party risk management lifecycle. The OCC provides an outline targeting financial institutions, while other security experts provide a slightly broader lifecycle addressing global standards. Most of the published lifecycles use a five to eight-step process. The outline below follows this trend but broken down into three broad phases with sub-steps, for a more comprehensive explanation.
Assess your Third Party Risk Management
Documentation and reporting
- Planning – The first determination to make is whether a third party is necessary. Consider if hiring an outside partner will provide better efficiency, needed knowledge, objectivity, an expanded market, etc. Depending on your need, a third party may be completely valid, but they are not always necessary. Because more entities involved means greater security risk, it’s important to have a tangible list outlining the reasoning for hiring a third party. For example, will the third party be involved in a one-time transaction or should a long term collaboration be considered?
- Due diligence and third-party selection – Prior to selecting a third party, experts suggest evaluating the qualifications of the third party as well as their resources available for completing the needed tasks. For example, does a third party have the resources to scale to the size of your operations? Identify what information gaps need to be answered prior to hiring, and then address them in the questionnaire (see below).
- Business justification/sponsor – When HR presents a panel with potential candidates, reasons should be provided as to why each candidate was selected. For example, if considering a foreign partner, what are the opportunities in that region? Furthermore, identify which department will be in charge of the third party — who is the primary point of contact for communication?

Oversight and accountability
- Questionnaire to the Third Party – The Foreign Corrupt Practices Act (FCPA) recommends sending any prospective third parties a questionnaire to identify any potential red flags. At a minimum, a questionnaire should inquire about company ownership (board of directors, including the percentage of ownership by each), government ties (personal or business), compliance regime, and banking and credit references. Beyond these baseline questions, companies should address any other areas of concern or business associations that may pose a risk in the future.
- Contract – After conducting a due diligence review and resolving any red flag issues, a company can proceed to the contract phase. The FCPA states that contract considerations should cover the payment terms and how those payment terms compare to typical terms in that industry and country, as well as the timing of the third party’s introduction to the business. Before signing a contract, consider your business model, in-house capabilities, overlap, the volume of business, compliance risk, regulatory environment, and reputation (of the third party).
Management of the Relationship
- Ongoing monitoring – Without ongoing monitoring, the hard work of steps 1-5 will be less effective. Post contract, a third party may think the review process is over; however, it is important to make it clear that slackening security or compliance adherence will not be tolerated. Requiring or providing training on anti-corruption and cyber threats keep third parties current and alert. Monitoring extends to digital activity, such as who accesses data and any suspicious activity. If systems detect such activity, a clear chain of communication and action steps should be in place, as well as a professional investigation team, should the need arise.
- Independent reviews – In conjunction with monitoring, an internal audit on third-party activity provides an objective analysis of security and compliance. Diana Lutz, of The Steele Foundation, posits that every company should conduct in-office and field reviews to ensure third parties adhere to financial controls and policy provisions. Additionally, audits should ensure that any gaps or security flaws are dealt with and remediation double-checked. Furthermore, having a relationship manager designated to each third party partnership will provide streamlined communication and reporting.
- Termination – Giving onboarding more attention than termination is unwise, as regulators analyze termination reasoning and agreements thoroughly. Once a company determines that a contract should be terminated, access should be canceled and documentation. Transparency as to why a third party contract was terminated and the exit actions that were taken can only help a company’s position when an audit occurs in the future.
How Much Oversight Is Too Much Oversight?
There is a fine line between micromanaging and proper supervision. Companies must find a balance between allowing a third party to be efficient and still maintaining oversight over operations. Implementing an oversight committee to conduct a yearly (or bi-annual) audit of all third-party relationships will enable a more broad-perspective review in contrast to the day to day monitoring. During the audit process, an oversight committee may review the following to begin:
- How current compliance and conduct codes are impacting third parties
- Ensure all financial transactions, records and accounts are legitimate
- Work performance
- Third-party affiliates
- Disbursements
- Equipment or services provided
Why is a lifecycle necessary?
All the stages of the above lifecycle contribute equally toward strengthening a company’s security. Treat every part of the lifecycle as vital. For example, while it may be easy to put more emphasis on monitoring, a contract’s language can dictate how the third-party relationship will progress and whether the relationship will be an asset or a hazard.
Even if other companies in your industry have open-ended dealings with third-parties, implementing the above life cycle will give your company a strong foundation for expanding the future. Many times companies begin expanding operations and partnering with the single third party, but eventually, the company will rely on more and more outside partnerships. Having a well-established protocol for dealing with third parties is critical and will ensure that when an inquiry occurs, whether compliance-related or otherwise, your company can respond quickly and accurately, a true sign of a healthy risk management lifecycle.
Risk Score Drivers
At a 2014 SCCE Utility and Energy Conference, GE Oil & Gas outlined how it approaches third-party risk management. One part of GE’s process revolves around risk score drivers or key questions that will help determine how riskier it is to partner with the third party in question. Although the threat landscape has obviously evolved since 2014, the concept of risk score drives still holds value in 2020. Below is the list of questions GE uses, which can be adapted to almost any industry.
- Country channel where the third party is located in or where it sells into
- Experience by the third party with the sales channel
- Type of third party involved (agent, reseller, distributor)
- Standard v. non-standard commission rate
- Will any sub-‐third-‐party relationships be involved?
- Will the third party sell to a government entity or instrumentality?
- Do any of the third party’s principals, officers, or agents work for a foreign government, state-‐owned enterprise or political party?
- Was the third party mandated by the customer or the end-user?
- What is the third party’s contract duration?
- Is the third party involved in more than one project?
- Does the third party have any historical compliance issues?
- What is the percent of sales with products or services?
- What is GE’s annual revenue with the third party?
Healthcare and Third-Party Risk Management Tips
Healthcare entities store a significant amount of sensitive data and work with many third parties. As more companies rely on technology, healthcare cybersecurity risk management has become more expensive and bewildering. Recognizing this, the non-profit organization Healthcare Information and Management Systems Society, Inc. (HIMSS) recommends five cybersecurity strategy tips for managing third party risk:
- Take a holistic approach – Before offering a third-party a contract, determine what they can offer and what it will bring to the company. What is the value of their services or products? Even if the products are good, if the third party adds significant risk, it may not be the best partnership to make.
- Collaborate – Limiting cybersecurity teams to only their department puts them at a disadvantage. Collaborating with compliance, supply chain, and legal departments will create a uniform policy and identify any gaps in third party management.
- Strive for improvement – Perfection and cybersecurity don’t go hand in hand. Omar Khawaja, vice president, and chief information security officer at Highmark Health, believes trying to achieve perfection will likely lead to frustration; rather, he promotes striving for improvement. What it would take to achieve “perfection” in cybersecurity may not be feasible for many companies as every company has different amounts of resources. Khawaja further noted that a good first step for managing risk is requiring a third party to fill out a questionnaire or conduct a certification audit. Either of these options will document what security measures third-parties have in place.
- Verify and document – After a questionnaire is completed, companies must verify that the third party is truthfully representing the security and compliance measures in place. If a company fails to ensure this accuracy and a third party commits an infraction, the company will bear the responsibility.
- Continuously evaluate – Business partnerships aren’t stagnant just as cyber threats are not stagnant. If processes change, contracts and cybersecurity policies must be updated to accommodate. For example, if transaction platforms or methods change, the new risk level must be analyzed. Based on the risk, new security measures may be necessary that was not stipulated in the original contract. Other similar scenarios may include adding a new product or changing how data is stored. Before these changes occur, develop a plan for how to adapt a questionnaire when changes inevitably occur. Moreover, when a change occurs, have the third-party revisit the questionnaire and determine if their security measures still meet the thresholds required.
How to Adapt
Due diligence plays a large role in determining whether a company will assume the penalties for any third-party violations. However, customizing questionnaires for every third party may not be feasible for your company. Another option, as noted by HIMSS, is to rely on certifications. Using standardized outside certifications or audits, such as SOC 2 technical audit, puts less of a burden on companies to conduct their own internal investigations. This will assist smaller companies that have fewer resources but are looking to grow by utilizing third-party services. Lastly, even with these certifications, companies should still conduct a make sure third party mindsets on compliance and cybersecurity mirrors theirs.
Need Help?
At the end of the day, third party risk management involves three core factors: proactive policies, prevention, remediation tactics. If a third party comes under scrutiny, the first questions for your company will be what did you do to prevent this? and what did you do when you discovered the issue? Having organized documentation and a thorough third-party risk management process can only help a company facing potential legal repercussions. If you are interested in learning more about the third-party risk management lifecycle, contact RSI Security today.

