In theory, Bring Your Own Device (BYOD) policies sound great, but companies now face the security challenges that come with less control over employee technology. There are many security issues to consider when it comes to integrating personal devices into the workplace environment. Learn about the BYOD challenges with this complete guide.
BYOD Explained
In the past, companies typically provided devices for employees. Before laptops and other portable devices became mainstream, it would have been absurd to expect an employee to bring a desktop computer to work much less a desk phone. But with the portability of today’s electronics, most employees will likely bring at least a phone to work, even if it isn’t integral to conducting work.
This brings up an important point: the difference between devices at work and devices for work. Employees bringing devices for personal use, like a cell phone or tablet, present a moderate security risk. However, if those personal devices are used to access company files or networks, the risk increases significantly. According to recent data, 82 percent of companies allowed employees to use personal devices for work in 2018, compared with 74 percent in 2014. Consequently, companies would be wise to outline BYOD policies and, to every extent possible, enforce the line between personal use and work devices.
Assess your BYOD plan
The Generational Shift
As technology has improved at an exponential rate, the BYOD movement has largely been tailored toward attracting the younger generation. Yet, one of the hurdles BYOD policies face involves the concept of “consent.” What falls under the private domain when work and personal activities are mixed on a device? Younger generations are much more willing to relinquish a certain level of their privacy than older ones; this does not necessarily bode well for companies implementing a BYOD policy. Managers need to know that their employees are taking the necessary precautions to protect proprietary information.
In a comprehensive report looking at the increase of BYOD policies in the workplace, SANS Institute succinctly noted the concept of “build it and they will come” has shifted to “build it and we’ll fix it in release 2.0.” There is a constant need for innovation, like BYOD, to attract and retain millennials. However, with this new workplace environment there are four major concerns: how to maintain/store data on personal devices, dealing with breaches on personal devices, secure destruction of data, and legal proceedings (e.g., an audit).

Benefits of BYOD
- Flexibility and Mobility – Allowing employees to have devices that can leave the office and be used for personal activities makes it easier for employees who travel or commute. Instead of bringing a backpack full of laptops, cell phones, and tablets, employees can consolidate.
- Cost – One recent study found that by 2017, at least half of employers would require employees to bring their own devices. Why? Well, put simply, it’s cheaper. Companies save on hardware, telecommunications, support, and training. Technology is expensive; replacing broken or outdated devices cost companies hundreds or thousands of dollars. In terms of telecommunication, some companies no longer foot the bill for cell/data plans. Furthermore, if a company lets its employees bring devices, it may need to pay less for licensing software (e.g., the Microsoft suite). The bottom line is that BYOD policies, in theory, should reduce operating costs.
- Productivity – Using a device that an employee already knows how to operate enables better efficiency. Using customized devices that users are comfortable with cuts back on the time needed to learn a different operating system (OS). Subsequently, companies are able to invest less in employee OS training and more in higher-level courses. Using one device simplifies communication and enables employees to seamlessly transition between work and personal time.
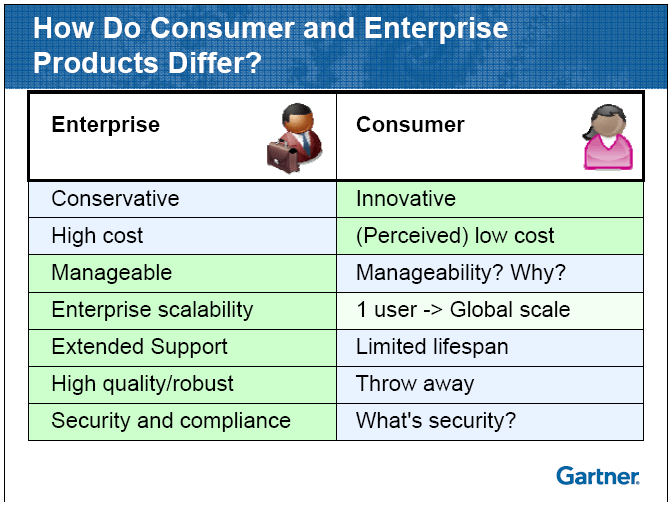
Credit: Gartner (Monica Basso and Nick Jones)
The Drawbacks
Although BYOD policies may at first appear cost-effective, the ultimate savings depends on how companies implement such plans. An Oxford Economic study found that companies increasingly pay stipends to their employees for mobile devices. This is in large part a result of mobile devices increasing flexibility. For example, smartphones now possess the power and memory to run many business programs (e.g., Word, Excel, Adobe, etc.). With these capabilities, more tasks are completed on devices requiring paid data plans.
Additionally, with many employees using their own devices, a more robust remote IT and cybersecurity team or department is needed to oversee them. Depending on a company’s size, BYOD policies may not provide the same value to employees or IT departments.
Lastly, personal productivity may be increased by BYOD policies, but such programs can also inhibit inter-office collaboration. For example, if an employee uses his iPhone to send a document to his co-worker, an Android phone user, he will likely need to change the format. While this may seem like a minor step, given all the applications available to convert formats, the time will add-up if many documents must be exchanged. If, in contrast, companies purchase the same phones for all their employees, file formats will be consistent. This is not the same in every scenario, but such an example highlights the logistical issues employees may face under a BYOD policy.
How to Implement a BYOD Plan
Do you deem the BYOD benefits greater than the risks? If so, then consider these seven tips for starting a BYOD policy:
- Define what “bring your own device” means in the context of your company. For example, are all devices acceptable or are Apple products preferred? Make sure that if all devices are accepted, the IT department is prepared to support them.
- Implement a list of security policies for BYOD devices. For example, include a clause on passwords. If an employee brings his/her own phone, uses it for work, but still fails to use a strong password to limit device access, company information is likely at risk. Specify whether a 6-digit PIN is acceptable or whether an alphanumeric password is required. It may also help to provide resources for your employees to learn what a “strong” password really means.
- Outline device services available. Will devices have access to all work networks? Will IT be able to assist if personal devices break? For example, if an employee’s laptop breaks and it must be serviced outside the company, will the company provide a spare computer? All these questions should be outlined in a BYOD policy so employees are aware of the potential expenses they may incur.
- Mixing personal and work-related tasks may blur the line concerning who actually owns the data stored on a device. For example, if a device is compromised, and a company wants to wipe the device, should the personal data be considered before wiping the device? If the information isn’t stored in the “Cloud,” an employee’s personal data may be permanently lost. The question is difficult, but from a company’s perspective, the risk may be too high to not wipe a device. For this reason, it’s important to be transparent about this aspect in a BYOD contract.
- Decide whether there should be limitations on applications. Any device utilizing the company network is a potential threat, whether it be a personal device or company-provided device. Really, any device with company information or access to the network poses a threat. How does this relate to apps? Well, consider that an employee just downloaded the SHAREit app. This app allows individuals to transfer files, photos, etc.to different devices. However, the app, unbeknownst to downloaders, has a security flaw — it allows threat actors to bypass the authentication method. If an employee downloaded this app on his/her device for personal use or, worse, used it to transfer work files, the company system may have been breached. While this may sound hypothetical, the actual vulnerability of the SHAREit app was just recently revealed, making it vital that companies specify which apps are sanctioned or provide a list of apps that are sanctioned for work activities.
- Next up, align your Acceptable Use Policy (AUP) with BYOD policies. Like applications, it would be wise to implement other restraints on network and Internet access. Are there any restrictions on what employees view on personal devices? What are the ramifications of using a Virtual Private Network (VPN) to access social media sites?
- Lastly, what do you do if an employee leaves the company or is let go? Upwards of 60 percent of companies fail to remove company data from ex-employee devices. If not specified in a BYOD contract, companies can’t completely wipe personal devices, and it also seems unethical to allow IT to sift through all the content on a personal device. With the widespread use of Cloud storage and services, revoking access to company platforms is easier, but downloaded content presents further problems. For this reason, it’s vital to outline an employee exit strategy in any BYOD policy/contract.

How to Write a BYOD Policy
There are three components to a good BYOD policy: written terms of use, software for oversight, and an agreement to be signed by employees. Prior to writing a BYOD policy, it will likely help to bring together a round table of managers from each department. Taking advice from IT, accounting, and legal will enable HR to write a holistic BYOD policy — one that covers the minutiae and flexibility of devices. So, what do you include in the written section? Below is a basic list to consider, although each company will have to tweak their policies to fit their scale and type of environment (e.g., small, dispersed offices vs. large corporate offices).
- Acceptable Use – Specify if websites will be blocked, personal use parameters, camera functionality (i.e., is it on at all times?), what devices may not be used (e.g., proprietary data transfers), which apps are allowed/not allowed, what company platforms may be accessed.
- Devices and Support – Outline what phone models, operating systems, and versions are supported. Are phones, tablets, and laptops allowed, or does the BYOD policy apply to only certain devices? Is remote IT available to help with issues other than connectivity? Does IT have the right to configure devices prior to allowing employees to access the network?
- Reimbursement – If the company pays for a data plan, what are the limitations?
- Security Program – Specify any BYOD security precautions (e.g., passwords), list approved apps, and note device wiping scenarios.
- Risks/Liabilities/Disclaimers – Lost device information [40 percent of large data breaches in 2018 resulted from stolen or lost devices], right to disciplinary action, etc.

How to Monitor Personal Devices
Even though most experts would agree that monitoring personal devices used at work is necessary, the more difficult question is how to go about it. The first step to vulnerability monitoring is to catalog who is using what on the network. Once these statistics are established, the next step is to consider if a management software agent should be installed on devices. The goal is to be able to track which applications employees primarily use and what bandwidth is consumed. Lastly, conduct research on how to enforce the BYOD policies your company supports. Accountability is key when it comes to a decentralized network of personal devices.
Need Help?
In all likelihood, most companies probably have some form of BYOD in operation, since employees rely on their cell phones for everything — calendars, communication, music, exercise. In the age of communication, denying personal devices at work is virtually impossible. However, letting a BYOD environment “grow” naturally (i.e., as a company expands) can cause some serious security threats down the road. Consequently, it’s important for companies to get ahead of the game and closely examine current policies for personal devices. If none exists, it is imperative that IT or another department develop a plan. Even with a policy in place, managers should review it and make sure it covers all the necessary topics and potential loopholes. For help with devising a BYOD policy or reviewing an already existing policy, contact RSI Security today.
