In 2019, the Payment Card Industry Security Standards Council (PCI SSC) began taking feedback for improving version 3 (v3.2) of the Payment Card Industry Data Security Standards (PCI DSS). With the new feedback, PCI SSC hopes to publish the final version 4 (v4.0) by 2021. Wondering how PCI DSS 4.0 will work? Get all your questions answered with our comprehensive guide.
PCI DSS Purpose
The Payment Card Industry Security Standards Council (PCI SSC) developed the first version PCI DSS in 2004. Since the initial release, the PCI SCC, composed of major industry players like Mastercard, Visa, and American Express, has worked to improve the Standard to better fit industry needs and account for changing technology. PCI DSS 4.0, expected later this year, will build on the three core tenets of the past standard versions: data security, transaction security, and application data security.
The PCI DSS controls and best practices are designed to do the following.
- Help entities build and maintain a secure data network
- Protect cardholder data
- Establish and maintain a risk/vulnerability management program
- Implement access control measures
- Encourage companies to monitor and test networks on a regular basis
- Create and maintain a security policy
Payment card industry leaders agree on the above general goals, but compliance specifics will vary per provider. PCI DSS documentation recommends that entities contact the financial institutions with which they are affiliated to verify what requirements must be fulfilled prior to starting the compliance process, as well as later in the process to confirm if any changes are necessary.
The Three PCI Standard Categories
PCI Standards include not only DSS, but also PIN Transaction (PTS) and Payment Application Data Security Standard (PA-DSS). PTS protects the entry process and stored information related to user PINs, which impacts both systems and physical machines (such as ATMs). PA-DSS involves software developers and integrators of payment applications that sell payment card industry software. The PCI SSC provides a list of tested and validated applications on its official website.
Schedule a Free Consultation
Stages of PCI DSS Compliance
Stage 1: Assess
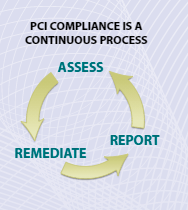
Image source: https://www.pcisecuritystandards.org/pdfs/pci_ssc_quick_guide.pdf
The Council defines the assessment phase as, “identifying cardholder data, taking an inventory of your IT assets and business processes for payment card processing, and analyzing them for vulnerabilities that could expose cardholder data.” The Assessing phase includes both a self-assessment and an assessment by a Qualified Assessor. The extent of an assessment depends on if cardholder data is stored and how many transactions an entity processes on a yearly basis.
Stage 2: Remediate
The remediation phase focuses on fixing any security holes identified in the assessment phase and removing excess cardholder data from storage or collection. Unsafe practices also fall under the remediation phase, such as improper handling of payment card data or a vulnerability in the flow of cardholder data. During this phase, the PCI SSC suggests performing a network scan, addressing gaps identified in the self-assessment, ranking vulnerabilities, and applying patches or other necessary fixes. Once these steps are complete, companies should re-scan to verify the fixes, solve the identified issues, and reduce overall vulnerability.
Stage 3: Report
Companies are expected to regularly report to the acquiring bank and card payment brands involved with business transactions. Although the PCI SCC oversees and guides the policies in PCI DSS, it does not ensure compliance. Rather, merchants submit a quarterly scan report, completed by an Approved Scanning Vendor (ASV), to the financial institutions with which they do business. All fixes must be documented and compliance reports submitted to banks and/or card brands.
The QSA assessments may vary by company size. For large companies, or those handling large amounts of cardholder data, a QSA will conduct an on-site assessment every year and convey the findings to each acquirer. Companies handling less cardholder data may only be expected to submit an annual Attestation within the Self-Assessment Questionnaire. To determine which category your company falls into, contact your acquirer or a compliance specialist. Failure to comply and report may result in fines, equipment upgrades, revenue loss, internal system overhauls. If a fine should be deemed appropriate, the payment card brands determine the level of fines.
PCI DSS Compliance Levels
Depending on the number of yearly transactions a company processes, it will fall into one of four PCI DSS levels. From level one, the number of yearly transactions decreases, with level four having the least number of transactions. Based on these levels, the extent of compliance changes. However, all companies within the levels must complete an assessment, conduct a quarterly network scan, and complete an attestation form. The levels mainly impact the minutiae of the assessment.
Level 1 – Upwards of six million card transactions per year
Level 2 – one to six million
Level 3 – 20,000 to one million
Level 4 – less than 20,000 card transactions
PCI DSS 4.0 Timeline
After receiving 3,000 comments in 2019’s round of Request for Comments (RFC), the PCI SCC plans to publish the version 4.0 draft in late 2020. Once that draft is available, the Council will open another RFCs to receive feedback on the initial v4.0 draft. According to a PCI SSC press release, the final draft is expected mid-2021. In terms of a compliance transition phase, entities that must comply will have 18 months in which PCI DSS v3.2.1 will remain active, giving them plenty of time to thoroughly read the new documentation and adjust security measures. Version 4.0 will become the only valid active requirements two years from its final release.
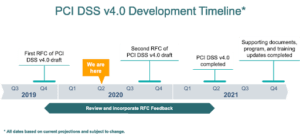
Image Source: https://blog.pcisecuritystandards.org/pci-dss-v4-0-anticipated-timelines-and-latest-updates
PCI v4.0 vs PCI v3.2
Version four grants stakeholders a more substantial voice in the standard development process. Previous versions gleaned feedback from Participating Organizations and assessors. The main source of revisions comes from RFC periods. The PCI SSC wants a robust set of guidelines, but acknowledges that if guidelines are too strenuous or impractical, companies are less likely to attain compliance.Consequently, the two overarching goals for v4.0 are security and flexibility.
According to the PCI DSS website, during the draft development process, the four top priorities were to:
- Ensure the standard continues to meet the security needs of the payments industry
- Add flexibility and support of additional methodologies to achieve security
- Promote security as a continuous process
- Enhance validation methods and procedures.
What to Expect in the PCI DSS v4.0 Initial Draft
When the draft of PCI DSS v4.0 is released in late 2020, the Council will open a new round of RFC. The hope is the stakeholders, the merchant payment community, and the QSAs will provide feedback on the draft so the final version will better meet industry needs and address the changing threat environment. Below are the proposed changes to expect in the upcoming draft.
- Accounts for the use of different methodologies to achieve PCI DSS compliance
- Accounts for new payment technologies (e.g., the cloud environment)
- Improved flexibility by focusing on the end result (i.e., security flaw addressed) versus the exact implementation process. Not every company will approach the noted vulnerability the same way, but what matters is that the outcome is uniform across the industry
- New document language focuses on intent and the desired outcome, rather than exactly how to achieve that outcome
- New validation approach gives companies more options for achieving compliance
Emma Sutcliffe, speaking on behalf of the PCI DSS Council, described the new approach as the following.
“Through customized validation, entities can show how their specific implementation meets the intent, and addresses the risk, providing an alternative way to meeting the requirement as stated. By offering two approaches to PCI DSS validation, entities can identify which approach is best suited to their security implementation for each PCI DSS requirement.”
- Insight on scope of PCI DSS and acknowledge if changes need to be made
PCI DSS 4.0 Projections
With the initial draft still in progress, the exact changes that will be made are unknown. However, industry leaders believe the following categories will likely receive updates.
Data Transmission
Payments and cardholder information that previously went through banks or websites, now pass through numerous other platforms, such as budget apps, service payment apps, online stores, and much more. With each new transit point, the attack vectors increase. As a result, experts expect v4.0 of PCI DSS to expand controls and requirements for data transmission in areas like encryption.
Download Free PCI Compliance Checklist
 |
Attack Vectors
In creating and updating cybersecurity standards like PCI DSS, governing bodies take into account the changing nature of attacks. Within the payment industry, phishing and social engineering have increasingly become the top attack methods. As such, the PCI SCC announced the new version will address these threat areas more thoroughly. In reaction to the new threats, the risk assessment guidelines will likely be revamped and expanded.
Authentication
Authentication methods in all industries are shifting. Password requirements are changing to allow for passphrases, which are easier to remember and in some cases more secure. Additionally, Multi-Factor Authentication (MFA) continues to be implemented using combinations of SMS, email, and biometrics. It is expected that PCI DSS will follow suit and update its documentation on how to approach and better authenticate users.
The Cloud
With the growing option in cloud storage and computing power, experts forecast that the PCI SSC will update its cloud computing standards in v4.0, particularly regarding serverless computing and how to better secure cloud environments.
Rethinking PCI DSS Scope
Based on the current v3.2 documentation, PCI DSS scope is broad. By definition, PCI DSS applies, “to all system components included in or connected to the cardholder data environment.” Cardholder data passes through numerous environments, including, but not limited to, network devices, firewalls, devices, routers, the cloud, and application. Not surprisingly, this breadth of scope has caused some concern within the industry and has led the PCI DSS council to put forth ways of reducing the scope.
Steps to Reduce Scope
- Examine the flow of cardholder data, both inflow and outflow. For example, when individuals make purchases online, where does their financial data go first? Even limited transactions, such as a yearly account status update should be noted. In other words, whenever cardholder data is in motion, whether often or once a year, it must be noted in a data flow model. Inflow and outflow may be in a physical or virtual method. Due to the interconnected nature of online transactions, it is common for outflow to go to backup servers or third parties.
- Review what happens to cardholder data in between inflow and outflow. Is cardholder data stored or logged in a system. Is the data connected to a cloud environment? Any environment which the cardholder data comes in contact with must be included in the scope.
Creating a data flow model and analyzing it may reveal that the actual cardholder data doesn’t touch certain systems and, thereby, reduces the scope of PCI DSS compliance.
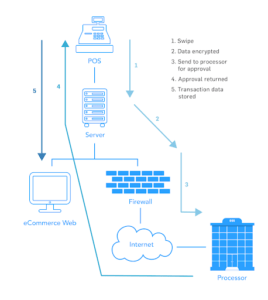
Image Source: Example of Cardholder Data Flow Map https://www.securitymetrics.com/blog/pci-consultants-say-reduce-pci-dss-scope
What Expands PCI DSS Scope?
One aspect of the PCI DSS assessment process includes a Self-Assessment Questionnaire (SAQ). Depending on the level a company falls into, the self-assessment may be very involved, which can expand the scope of overall compliance. For example, storing Primary Account Numbers (PANs) automatically means a company must complete SAQ level D. As of PCS DSS v3.2, there are eight SAQ levels — A, A-EP, B, B-IP, C-VT, C, P2PE-HW, and D. Entities not electronically storing cardholder data will typically fall into the first five categories. If stored PAN data does not include a user’s name or expiration date, it is not considered cardholder information, but this scenario rarely occurs. Since PANs are considered highly desirable targets, they should be encrypted while in storage.
Key Takeaways
- The second draft of PCI DSS 4.0 is expected at the end of 2020, with the final version published in mid-2021. After the initial release, a second round of RFC will open.
- Improvement areas will focus on new technology and evolving threats, as well as how to better focus self-assessment and avoid a needlessly broad scope.
- Create a plan of action for comparing the current 3.2 version to the new drafts and research the tools or third parties available to help
Since the launch of PCI DSS in 2004, global compliance has fallen. Despite increasing threats, in 2018 global compliance stood at 52.5% compared to 36.7% globally in 2019. In order to shift this trend, the PCI is committed using multiple rounds of RFCs to shape PCI DSS v4.0. Do you need assistance becoming PCI DSS compliant? Contact RSI Security today for a consultation.
Schedule a free consultation
