Protecting assets isn’t always about having the latest cybersecurity monitoring software or the strongest encryption. While those safeguards hold value, having a robust data management approach is critical. The first step to protecting your valuable data is knowing exactly what you have and where it is. Learn about the importance of creating a data asset list and how you can create one.
Why Is Maintaining a Data Asset List Important?
The expansion of big data requires an organized approach for collecting, processing, and analyzing it. Having an established data inventory and upkeep process enables faster analysis and integration of data. Yet, in February 2020, CompTIA reported that only 44% of companies had IT employees dedicated to data management.
The gap in how many companies use data management may stem from a misunderstanding that technical safeguards are more important than taking an inventory. Data management plays a vital role in securing data because knowing what data you have allows companies to rank risk and better allocate security resources. Taking stock of what data you collect, store, and transmit may even highlight redundant data collection or improve data processing efficiency.
Satisfy Compliance Standards
Beyond maximizing data for better products and customer experiences, conducting a data inventory satisfies many compliance laws like GDPR, HIPAA, and PCI DSS.
GDPR – The EU’s General Data Protection Regulation has 99 Articles and more than 170 Recitals which makes compliance a daunting task. The International Association of Privacy Professionals (IAPP) recommends the following steps for effectively managing data in light of the GDPR’s stipulations.
- Take stock of data collection and map where it goes once it enters the company’s system. Data mapping improves transparency and helps fulfill communications obligations under the GDPR.
- Identify why data is being collected and processed. This will help reduce excess data collection, which increases security risk. Verify what data travels to countries covered under the GDPR and those not covered.
- Designate employees to work on a data management team tasked with building and maintaining a data governance system. This team will develop policies for handling data and provide training for employees.
- Perform data protection impact assessments, along with data protection by design and by default.
- Prepare and implement data retention and record-keeping policies and systems.
- Have a sound vendor management (processor) protocol.
PCI DSS – Requirement 2.4 of the PCI DSS maintains that companies must conduct a scope of the environment, which includes both systems and assets. During the audit process, auditors may request an asset list to compare it with the network flow or security controls.
HIPAA – HIPAA’s privacy rule indirectly addresses data asset management. The Privacy Rule requires companies to track hardware, like laptops, and electronic media that carry ePHI (data assets). An inventory, in this case, may also highlight what assets can be de-identified.
Assess your cybersecurity
Data Inventory for Beginners
What Is a Data Inventory?
A data inventory holds records about what data assets are maintained by a company, such as metadata, PII, design specifications, etc. Metadata is data about data and includes information on the type of data, update frequency, license use, contents, and related privacy considerations. For small companies, this process may not require segmentation, but for companies storing massive datasets across numerous servers, it will be helpful to break down an inventory list by department, employees, and the public.

Data Assets and Types
Not all types of data are going to garner the same level of importance, but they should all be included in an inventory. A data asset is something that can be used to generate future revenue for a company. A system, website, database, or document could all be considered an asset as long as they play a role in generating revenue for a company. The following points divide data assets into seven broad categories. These are the categories each asset will fall into when compiling an inventory list. Depending on the number of assets, a company may choose to break the seven categories down further.
- Design and Methods – Intellectual property, diagrams, schematics, patents, trade secrets
- Knowledge – Shared knowledge created and owned by a company, such as a presentation or a report
- Media – Video, article, images, etc.
- Transactions and interactions – Commercial transactions and interactions may be with customers, third parties, vendors, etc.
- User Input – User data collected by a company such as social media posts, search queries, etc.
- Sensor Data – Collected from sensors that track social movement, nature activity (weather, seismology, etc)
- Calculated Data – Models, forecasts, market activity charts generated by algorithms based on extensive data input/factors
How to Conduct an Inventory
GovEx, an initiative launched by John’s Hopkins University, strives to help governments maximize data management in order to make informed decisions and improve society. In pursuit of that goal, GovEx outlines 5 steps in the data inventory lifecycle that is applicable to the private sector as much as the government.
- Establish oversight authority – determining who will lead the inventory process will enable coordination and provide clarity when it comes to who is in charge. This individual, such as a Chief Data Officer, will then assemble a team or committee to create a timeline, policies, and serve as the point of contact should questions arise during the process.
- Determine the data inventory scope and plan – Once a team is in place to oversee the process, it will draw up a timeline, determine the scope of inventory, set deadlines, establish guidelines, and performance metrics. Depending on the size of the company or government entity, addressing scope will vary, but a general baseline for inventory addresses the following
- Data included in policies (government or compliance required)
- Distinguish between government, public, internal data
- Data assets
- Priority assets (those that aid in furthering the strategy of the company)
- Department assets
- Catalog data assets in accordance with your inventory plan – the oversight team should then liaise with departments in relation to the plan laid out in step 2. Each department reviews what data is collected, stored, or transmitted. Once the departments report back to the team, a comprehensive inventory list can be compiled. It’s recommended that the final list is in a machine-readable format such as a spreadsheet or CVS file.
- Complete data inventory quality checks – For government entities, an inventory may be published. This is not always the case with the private sector, but compliance standards may require a similar level of transparency. Once the final asset list is completed, the oversight team can determine next steps. For example, non-government entities may want to improve consumer trust by providing a list of what information is collected. Another consideration is how such a list will be used for compliance audits.
- Initiate data prioritization efforts – If considering publication, inventory teams should create a priority list for releasing the information. Consider the strategic ramifications of publication in balance with department needs and the public’s expectations.
Third-Party Data Management
The same CompTIA report found that 65% of companies are considering hiring third parties to assist in the data management process. Like all third-party services, there are different levels of outside involvement. For example, some companies may only want a data inventory assessment, but others may want a third party to initiate and supervise the entire data management process. In either scenario, conduct a thorough evaluation of the third party before hiring them.
How to Assign Risk Levels to Data Assets
The value of each data type will change based on the industry. For example, in the news broadcasting industry, media content will hold a high value, whereas in the technology industry design and methods will likely garner more worth. Risk levels will be assigned in part based on the asset type and how much value a company puts on that asset type.
ISACA, a professional association providing IT governance resources, published a journal article on IT Asset Valuation, Risk Assessment and Control Implementation Model, which outlines steps and quantifiable methods for assigning risk levels. The brief summation below will be very helpful when integrating your asset list with risk management audits.
Gather Asset List and Identify Ownership
Using the seven categories in the above section, start taking inventory of all data assets by department. Report back to the oversight team throughout the inventory process to avoid inventory gaps or overlapping efforts. With each asset, include information about if and where it is stored, and if it is transmitted or processed.
Next, identify whether the company owns the asset or if an outside party holds the rights to it. For example, if a company is collecting customer information, the consumer, in a sense, still owns the data and possesses certain rights to that data granted by privacy regulations. Noting this on the inventory list will permit the oversight team to better determine a commensurate level of security.
Determine Security Objectives
Once the inventory list is complete, begin the risk rating process. This begins by assessing the importance of Confidentiality, Integrity, and Availability (CIA) in relation to each container of data. A container simply means where one type of asset is stored. For example, all customer transactions may be stored in one container. Collaborating with your cybersecurity or IT team at this stage will provide greater insight on risk levels.
Assign Value
Using the previously created list, go through each category and assign a risk level based on the defined security objectives. Each asset storage container will garner a different level of risk based on the contents it holds. ISACA developed a weighting system to assign a value to each container type. However, each company may choose to establish its own ranking system. By the end of the process, companies should have assets divided into low, medium, and high-risk categories. The categorization process shows companies which assets should receive priority when implementing or testing security controls.
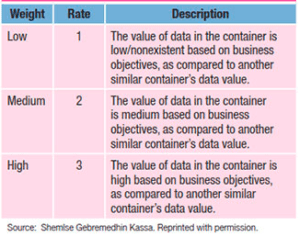
Image Source: Model to Measure Weight of an Asset
Estimate Asset Impact Likelihood
Vulnerability is only the potential for harm, but the level of vulnerability depends largely on how often it has been exploited within a certain industry. The more times a vulnerability is exploited, the higher the risk and chance of recurrence. For example, how often have healthcare entities fallen prey to ransomware attacks and by what methods?

Image Source: Model for Probability and Likelihood of Risk https://www.isaca.org/resources/isaca-journal/issues/2017/volume-3/it-asset-valuation-risk-assessment-and-control-implementation-model
Some data is a prime target for threat actors, and some, if impacted, would result in minimal damage to a company’s operations, revenue, and reputation. Two factors affect vulnerability: susceptibility and exposure.
Susceptibility – Refers to how easy it is to exploit a specific weakness
Exposure – Refers to the flow of an attack. For example, if threat actors breach defenses, what would they have access to and how far could they go (what can they expose).
The chart below breaks susceptibility and exposure categories down into three levels, with three being the most impacted.
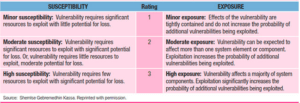
Image Source: Model for Asset Susceptibility and Exposure https://www.isaca.org/resources/isaca-journal/issues/2017/volume-3/it-asset-valuation-risk-assessment-and-control-implementation-model
Existing Controls and Gap Analysis
Once all an inventory list’s categories have a risk classification, analyzing the controls in place and identifying gaps is the final step. Controls, which may be proactive or reactive in nature, should limit impact, regulate, or reduce vulnerabilities. Controls typically mirror the determination made in the CIA assessment portion of risk assignment. In other words, the assets that received the highest priority based on the CIA should have a greater proportion of controls compared to less critical assets. Using a rating system like ISACA’s encourages uniformity throughout the asset inventory process and also reduces the likelihood of subjectivity.
Need Help?
If data is the new currency, then understanding how to manage it will put your company at an advantage. Keep in mind that the asset inventory process, much like the compliance process, isn’t stagnant. Inventory lists will change as new assets are added or removed. Throughout the process, you will likely make discoveries about how to improve operations and the data collection process. If you need assistance taking an asset inventory, contact RSI Security today.
