When conducting experiments, scientists will carefully set up control measures to provide parameters for results. These controls help define the outcome by marking what ways the experiment did or did not meet expectations.
Likewise, as you decide to gauge the effectiveness of your security, you will set up parameters that will help drive results. A penetration scan or a vulnerability assessment can help you evaluate the performance of your system.
This guide below will lay out in detail the difference between the pros and cons of penetration tests and vulnerability assessments, their differences, and why you might choose one or the other.
Penetration Test
A penetration test, or more commonly referred to as a pen test (or even Pentest), is a simulated attack on your computer system designed to test the security of that system. A team of trained experts will perform a series of diverse attacks against your system looking at both the strengths and vulnerabilities.They might use any number of penetration testing tools to fully test the security of your system. The U.S. Department of the Interior’s Chief Information Officer describes three results of penetration testing:
- Identifies vulnerabilities and threats
- Tests the reaction and identification capabilities of your agency
- Provides a measurement of continuous improvement
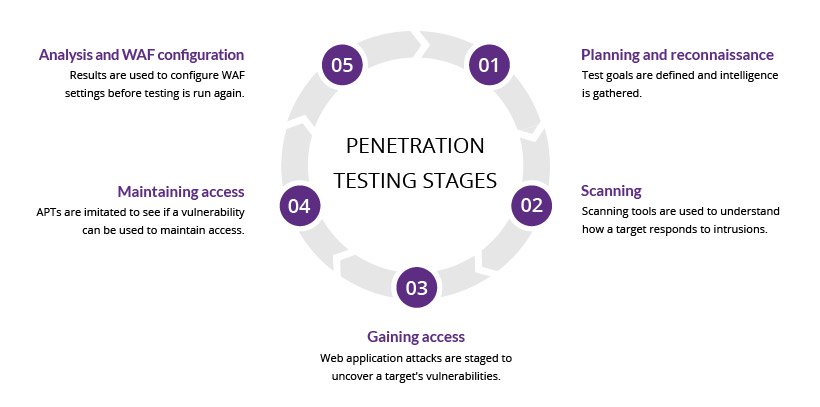
Image Source: https://www.imperva.com/learn/application-security/penetration-testing/
Need a Penetration Test? Learn more.
Why Should I Perform a Penetration Test?
Performing this test allows you to test your system’s weaknesses and strengths in a controlled environment before your adversary’s hack into your system for nefarious purposes. A pen test can also be a useful way to help gauge your organization’s readiness for a certification or compliance audit.
Also Read: How does an External Penetration Test Work?
A standard, regularly re-occurring penetration test may also be a requirement to maintain certain services and keep data secure for cardholders. The Payment Card Industry (PCI) should take great care to protect client cardholder data.
Pen testing can also show to your clients that you regularly test your system’s security indicating that their data is of utmost importance.

Types of Penetration Tests
There are several types of pen tests. White box, black box, gray box, covert, external, and internal testing. Each provides a unique look into your system’s vulnerabilities and will provide a different result. You may choose to have an internal or external team perform the penetration test.
After your developers create your system or applications, you can have other IT professionals on your team or specifically assigned developers perform a pen test. This is a cheaper option than having an external team conduct the test, but they may miss problem areas because they created the system.
An outside team can be useful because they can look into your system’s security with a completely fresh set of eyes. They may bring a unique hacking skill that your internal team does not possess. However, an outside hacker will be much more likely to cost more than an internal hacker. Generally, most companies invest in an external team for pen testing.
White Box Penetration Test
A white box pen test provides system and background information to the hacker. The hacker then has a clearer idea of the scope of the test and what to look for.
Black Box Penetration Test
A black box pen test provides little to no information to the hacker. This is also referred to as a “blind test” as the hacker will only be given a directive to do his best to infiltrate a company’s system.
Gray Box Penetration Test
A gray box pen test is a combination test of black and white pen tests providing more information than a black box test but less information than a white box test.
Covert Penetration Test
This test is unique in that most people within the company have no idea that the test is occurring. This test is often referred to as a “double-blind test” because not even the internal security professionals are made aware of the attack. This tests how adept your internal security team is at recognizing threats, reporting them, and counteracting attacks.
Naturally, you want to be sure that key players are informed for legal purposes so that the hackers do not face retribution for performing the test.
Also Read: The importance of Web Penetration Testing?
External Penetration Test
In an external pen test, the hacker isn’t given access to the building and must launch an attack at the company’s external technology such as websites, apps, or external servers. This type of test allows the company to measure how strong their defenses are from nefarious hackers or random security breaches.
Internal Penetration Test
In an internal pen test, the hacker is allowed access within the building and given certain permissions. This type of test measures a company’s ability to prevent large internal breaches caused by an aggravated employee. This test measures what controls are in place to prevent multiple facets of one system being damaged by an internal hacker.
Penetration Testing Different Parts of your Environment
Pen testing isn’t just limited to testing the firewall; there are many other options for testing a number of application systems to guarantee that your system is protected at all points of access. For instance, you may want to run a test that takes a look at mobile security and apps on a mobile device that connect to your system. There is penetration testing for cloud computing, web applications, and front/backend servers.
By simulating a cyber attack with penetration testing services provided by RSI Security, you can determine where and how hackers will get into the system. A good penetration testing company will also inform you how a hacker may behave when they gain access to your system. Look for a company that does not just focus on network penetration testing, but will perform holistic system tests like those mentioned above.
Remember, you may be required to regularly perform compliance penetration testing to meet standards set by HIPAA, PCI DSS, or NIST. Work with a penetration testing company like RSI Security to uncover any gaps or vulnerabilities.

How Often Should I Perform a Penetration Test
Now that you know more about some of your options for types of pen tests you can do, you might ask yourself how often you should perform regular tests. Using trusted penetration testing services provide you with in-depth information to help secure your network.
You should regularly perform pen tests; doing so at least once a year will guarantee updated IT management and security. A few other times you may also perform a penetration testing according to TechTarget are when an organization:
- adds new network infrastructure or applications;
- makes significant upgrades or modifications to its applications or infrastructure;
- establishes offices in new locations;
- applies security patches; or
- modifies end-user policies.
Other factors do come into play as to how often you should perform a pen test which includes: the size of your company, your clients, how many certificates you hold and must maintain, and whether or not you house your system infrastructure in the cloud provided by another vendor.
Vulnerability Assessment
A vulnerability assessment is a specifically tailored process to identify and quantify security risks and vulnerabilities within an organization. It is an in-depth process that aims to not just identify vulnerabilities but also provide possible solutions for mitigating the risks.
A vulnerability assessment is performed using an automated tool that periodically will scan your system for any potential weak spots. Each tool can be programmed to scan or specifically search elements of your choice within the system.
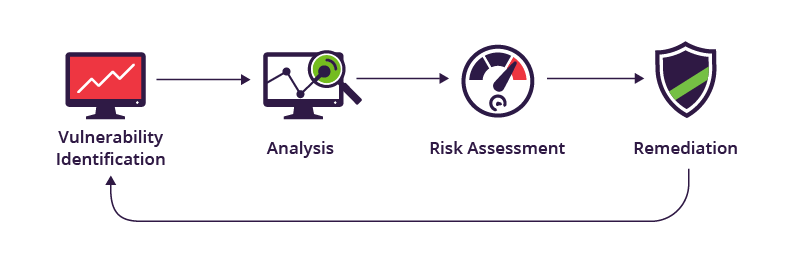
Image source: https://www.imperva.com/learn/application-security/vulnerability-assessment/
RSI Security has created a helpful guide on vulnerability scan expectations so that you can better understand what you should look for and the types of exams that exist.
There are several types of vulnerability assessment which include host-based scans, wireless network scans, network-based scans, application scans, and database scans. Each focuses on a different aspect of your organization’s system.
Why Perform a Vulnerability Assessment?
When hacking a system, one of the primary goals of a hacker is to leave no trace that he had penetrated the system. Like a robber in the home, he will do everything in his power to leave no trace behind of his presence.
This means that if you schedule a pen test with an external team, they would most likely miss any signs that someone else was already in the building, so to speak. Their goal is not to determine who has been there, but where your defenses are weak.
Thus, a vulnerability assessment is a crucial process to incorporate security best practices. This scan can identify bugs or remnants left behind by prior hackers. John Chambers, ex-CEO of technology conglomerate company Cisco points out, “There are only two types of companies: Those that have been hacked, and those that don’t know they have been hacked.”
Also Read : How to build an effective Vulnerability Management Program
When to Perform a Vulnerability Assessment
Since a vulnerability assessment is an automated process, you can perform them on a regular schedule to determine your system’s strength. This continuous monitoring will ensure that you are aware of any potential risks or changes that have been made to the system.
Another important time you would want to perform a vulnerability assessment is when a new vulnerability hits the market. Take for example the massive cybersecurity attack in 2017 referred to as EternalBlue.
EternalBlue and WannaCry
The NSA developed the EternalBlue and was aware of its potential vulnerabilities and risks. When it was leaked by a group of hackers, the NSA failed to inform Microsoft of the risks inherent to the EternalBlue cyber exploit. Eventually, after a group of hacker’s breached Microsoft’s system, the NSA reached out explaining the risks and vulnerabilities.
While Microsoft busied itself preparing for a software patch, hackers developed their own exploit to piggyback on the weakened exploit developed by the NSA. Before Microsoft had issued the new patch update, hackers had used EternalBlue to spread one of the largest cyber-attacks, the WannaCry Ransomware Attack.
Affecting over 200,000 computers across 150 countries, the WannaCry Ransomware Attack caused hundreds of millions to billions of dollars and was only stopped by emergency patch releases from Microsoft and finding a kill switch that stopped infected computers spreading the ransomware.
After this incident, many companies performed their own vulnerability assessments to see if any of their systems needed patch upgrades. Of course, prevention is much cheaper than restitution; regular assessments in combination with pen tests can help protect your system.
Primary Differences Between Vulnerability Assessments and Penetration Tests
Now that you better understand what a penetration test and vulnerability assessment are, look at the following points below as to when to employ each process.
Below is a list laid out by SecureWorks of the way a vulnerability assessment is performed in comparison to a penetration test.
A vulnerability assessment:
- Catalog assets and resources in a system
- Assign quantifiable value and importance to the resources
- Identify the security vulnerabilities or potential threats to each resource
- Mitigate or eliminate the most serious vulnerabilities for the most valuable resources
A penetration test:
- Determination of scope
- Targeted information gathering or reconnaissance
- Exploit attempts for access and escalation
- Sensitive data collection testing
- Clean up and final reporting
The primary difference is really noted in the intent behind each process. A penetration test is performed to adopt the mindset of a hacker who would be attempting to gain access to the system (remember a hacker may use tools like phishing scams or even physical tools to gain access) while a vulnerability assessment is designed as an analytical/technical report.

Pros and Cons of Vulnerability Assessments and Penetration Tests
A vulnerability assessment will give a basic overview of potential weaknesses within your system, but the scan may not reveal how that weakness can be exploited and what data may be lost if it is exploited. Therefore, bringing in an outside team to hack into your system will provide a more thorough report than just a vulnerability assessment.
A vulnerability assessment really focuses on looking at the bigger picture of your system. Because it is a rapid overview scan, this assessment can move through a large system quickly. Additionally, this allows you to more frequently perform this process.
A penetration test is focused on minute details of a system since a successful hacker will approach each aspect with a trained eye on how to bypass security. The hacker will have a wide range of tools available at their disposal which will help automate some of the processes while allowing them to focus manual efforts elsewhere. Naturally, as technology and software development improves, hackers will become more adept at breaking into systems.
You might think of a vulnerability assessment as a precursor to a pen test. A vulnerability assessment will detail the areas which need improvement allowing you to make those necessary changes to your system. Once this is complete, then you can have a third-party employ a hacker to test your system to gauge the effectiveness of your security.
Nevertheless, a vulnerability assessment isn’t a requirement to preclude a pen test. You may choose to launch an immediate look into your system with a hacker who can also determine ways in which your system is vulnerable. Thus, the scope of each process produces a different result.
This table provides a more accurate description of the differences between a vulnerability assessment and penetration test.
| Vulnerability Scan | Penetration Test | |
| Frequency | At least quarterly, especially after new equipment is loaded or the network undergoes significant changes | Once or twice a year, as well as anytime the Internet-facing equipment undergoes significant changes |
| Reports | Provide a comprehensive baseline of what vulnerabilities exist and what changed since the last report | Concisely identify what data was compromised |
| Focus | Lists known software vulnerabilities that could be exploited | Discovers unknown and exploitable weaknesses in normal business processes |
| Performed by | Typically conducted by in-house staff using authenticated credentials; does not require a high skill level | Best to use an independent outside service and alternate between two or three; requires a great deal of skill |
| Value | Detects when equipment could be compromised | Identifies and reduces weaknesses |
Image source: https://www.secureworks.com/blog/vulnerability-scanning-vs-penetration-testing
Final Thoughts
Ideally, your organization should perform both tests to ensure that you are safeguarded and protected against hackers and bugs. How frequently you perform them and what type of test you choose to use depends on the needs of your business. Reach out to one of RSI Security’s experts today for a free consultation on penetration testing and/or vulnerability assessments.
