Integrating cybersecurity best practices has become an essential aspect of the information and communication technology (ICT) supply chain. There is a growing cyber risk associated with dealing with vendors that are not adequately vetted or audited for their cybersecurity capabilities. The National Institute of Standard and Technology (NIST) have devised a series of frameworks for cybersecurity best practice.
In this article, we will discuss what the vendor, or third-party risk management framework entails, and give a few tips on managing third-party risk.
Basics of the Framework
The NIST third-party risk management framework forms one publication within the NIST 800-SP. The paper outlines concerns along the ICT supply chain primarily:
- Products and services that may contain malicious functionality
- Potentially counterfeit
- Vulnerable due to poor manufacturing and development practices
- Tampering or theft of ICT solutions
- etc.
These risks, and others, arise from an organization’s lack of understanding and control over the technology they acquire. They also do not have an insight into how the technology is developed, or the processes, policies, and procedures in which the supplier employees to ensure the integrity, security, and resilience of the product or service.
These unknowns create an environment of high risk, which can be exploited by attackers. There is a general practice of due diligence for most organizations when acquiring new products; cyber risk has become a priority within the ICT ecosystem.
The framework intends to mitigate against the risks outlined above. In the following sections, we will discuss in more detail some areas of the framework.
Throwing Stones From Glass Houses
Before going into detail over the security controls of the NIST third-party risk management framework, it is crucial to clean the house first. Ensure that your organization has control over its cybersecurity architecture and that cybersecurity best practice is implemented at all required levels.
Why is this important?
As the saying goes, “those who live in glass houses shouldn’t throw stones,” essentially you shouldn’t criticize (or in this case assess the cyber risk of) another organization’s cybersecurity practice if yours isn’t a good example for the wider community, or the supplier. More so, you should try to create an open communication between you and your supplier as it fosters a better security culture for all parties involved (more on this point later).
Assess your Third Party Risk Management
Supply Chain Risk Management
Supply chain risk management (SCRM) is a vast subject, too large to be contained in one blog post, at least the NIST third-party risk management framework only pertains to ICT SCRM, which again is no small game.
The framework outlines two critical aspects of ICT SCRM those being:
- Integration of ICT SCRM into organization-wide risk management and;
- ICT SCRM security controls.
It is best to employ the skills of a specialist if you are looking to assess and improve the condition of your cyber risk management strategy, consider looking into our compliance services today!
Organization-wide risk management
Implementing ICT SCRM into the organization’s broader risk management framework is made easier the earlier it is done. When developing a risk management strategy, the formula is relatively standard:
- Identify possible risk events (Frame).
- Calculate the likelihood of the event occurring (Assess).
- Apply necessary countermeasures where possible (Respond).
- Monitor risks
Keeping in mind that certain risks just can’t be hedged against (acts of God). This example is an extremely rudimentary step-by-step of a risk management strategy and should be taken only as a summary and not a “how-to” (see below for a more detailed graphics from NIST). But ICT SCRM is similar in that way, the implementation strategy is identical, but the events are virtually projected onto the supply chain.
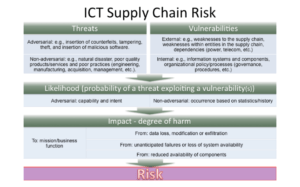
Image Source: Supply Chain Risk Management Practices for Federal Information Systems and Organizations, NIST Special Publication 800-161, Boyens et al., April 2015, Page 7
The NIST describes ICT SCRM integration as a tiered system (3 Tiers). Tier 1 deals with the overall development of SCRM strategy, determination of ICT SCRM risks, and guiding organizational policies. Tier 1 (Organization) ICT SCRM Activities:
- Establish policies based on external and internal requirements (costs, regulations, purpose, and applicability)
- Based on policy, identity:
- Business requirements (cost, security, privacy, etc.)
- Infosec. Requirements
- Org. wide function and how ICT SCRM will be integrated into the process
- Establish a risk tolerance level across org.
- Establish a group/individuals who will handle ICT SCRM requirement org. wide.
Tier 2 establishes the organization’s mission and business function, conducting business-level/mission risk assessment, and lastly, implementing tier 1 strategy and guidance to an organizational level, especially with acquisitions. Tier 2 (Mission/Business Processes) ICT SCRM activities include:
- Develop and define a risk response strategy.
- Create ICT SCRM processes that support the business process.
- Incorporate ICT SCRM requirements into the business process.
The final tier, tier 3, involves the application of ICT SCRM capabilities (from tier 1 and 2) to individual information systems and information technology acquisitions. Tier 3 (Information Systems) ICT SCRM activities are:
- Apply, monitor, and manage the ICT SCRM controls
This brings us into the next section of the article, where we will discuss the ICT SCRM security controls.
ICT SCRM Controls
The NIST has outlined a series of security controls that should be implemented as part of the overall risk management strategy; the NIST defines the controls as:
“The management, operational, and technical controls (i.e., safeguards or countermeasures) prescribed for an information system to protect the confidentiality, integrity, and availability of the system and its information. [FIPS 200, FIPS 199, CNSSI No. 4009, NIST SP 800-37 Rev. 1, NIST SP 800-53 Rev. 4, NIST SP 800-53A Rev. 4]”
The controls within this framework are relevant to the ICT supply chain as should be tailor implemented depending on applicable tiers of the ICT SCRM integration and specific needs of the organization.
The controls are broken down into “families,” which consist of sub-controls; if you wish to read the technical paper and all sub-controls you can find the full publication here. In the following sections, we will discuss in brief each control.
Access Controls
The first control family is access control. This control requires organizations to limit access to information systems to only authorized personnel, users, and devices. The use of usernames and passwords is a must.
Awareness and Training
This control requires that the organization employ a cyber awareness training program. Managers and key personnel who control information systems should be aware of any cybersecurity risks associated with their activities. Ensure that staff can carry out their responsibilities in a security-conscious way.
Audit and Accountability
Ensure the organization maintains logs of all activity on the information system. These logs should enable the identification of unauthorized users/devices connected to the information system. Individual information systems users should be unique and easily traceable in the event responsible entities need to be identified.
Security Assessment and Authorization
Your organization must assess security controls periodically. This assessment determines whether the controls are effective in their application. Correction in the implementation should be made if they are found lacking.
Configuration Management
Any device, software, hardware, etc. installed or connected to the information system must be configured with full security settings and not with off-the-shelf default configuration.
Contingency Planning
Your organization must ensure that a policy/plan is in place in the event of an emergency. This contingency plan could mean back-up operations, post-disaster recovery, and maintenance/availability of critical information systems.
Identification and Authentication
This control requires organizations to have a system that can identify and authenticate users or user-generated processes before allowing access to organizational information systems.
Incident Response
The organization must have policies and plans in place for incident response reporting and management. This incident response plan (IRP) must include systems for the detection, analysis, containment, and recovery of critical information systems. This should then be tracked, documented, and reported to appropriate authorities.
Maintenance
Organizations must conduct periodic maintenance on organizational information systems. They must also provide appropriate documentation on the tools, mechanisms, and personnel used to perform the maintenance.
Media Protection
This control family requires organizations to protect and limit access to media, both paper and digital, to authorized users only. The appropriate sanitization (disposed of correctly) of media is also required.
Physical and Environmental Protection
This control, as the title suggests, requires the organization to ensure adequate protection of physical space. Physical security means locking and limiting access to physical locations to authorized personnel only and protecting physical assets from environmental hazards such as flooding.
Planning
The organization must develop, document, update, and implement a security plan for organizational information systems. The plan should include the security controls that are in place, and ones that are yet to be implemented, and a code of conduct for individuals accessing the information system.

Personnel Security
Your organization must ensure that anyone holding a position of responsibility, including third parties, is trustworthy and meets established security criteria. Furthermore, information systems must be protected during and after termination or transfers of said personnel. Sanctions should be implemented to staff who do not comply with the policy.
Provenance
Provenance is a new control family introduced to the framework. The control requires that all acquisitions along the ICT supply chain have their origins documented. Your organization should be maintaining a recorded history of any changes made so that specific stakeholders can be notified of changes.
Risk Assessment
Your organization must periodically assess the risk to organizational operations, assets, and individuals resulting from the information systems’ function.
System and Services Acquisition
This control requires organizations to allocate appropriate resources for the protection of organizational information systems. They must also incorporate information security considerations in the overall system development lifecycle and software installation restrictions. Lastly, the organization must ensure that third-parties take adequate security measures that protect information, services, and application outsourced by the organization.
Systems and Communication Protection
This control primarily entails boundary level defense. Your organization must ensure that communication transmitted or received is protected at the internal and external levels. Software can be employed to aid, such as firewalls or a mix of system engineering principles that promote a favorable security environment and good security systems architecture.
System and Information Integrity
The final control requires organizations to identify, report, and correct information flaws within the system. Following the identification and correction organization must apply protection against malicious code injections and monitor security events reporting them to the appropriate authority.
RSI’s Tips to Third-Party Risk Management
Now that we have discussed the basics of the NIST third-party risk management framework, it’s time to put it into practice. The framework addresses the technical aspects of security risk management. Still, the reality is, dealing with suppliers means you are dealing with people, and they are, above all else, the most unpredictable factor in a risk assessment.
If you recall the previous section titled “throwing stones from glass houses,” we discussed the necessity for your organization to have implemented best practices methods before approaching suppliers with a cyber risk framework, which brings us to tip number one.
Implement Security Controls in your Organization
Take a look at the security controls listed in the NIST special publication document, and assess your organization and what level of security is necessary and then use that measure to interface with your supplier/vendor. Keep in mind that the risk assessment involves stipulating which controls are required for the third-party before you engage in business with them. This measure then becomes a tool in risk mitigation.
The framework implementation can be tricky, but it is also flexible to the needs of the business. Consider employing the skills of a specialist to help with security control implementation. Find our compliance services here.
Assess the Supplier
More so a requirement than a tip, the framework outlines the need for your organization to assess how well and at what level the vendor has implemented the necessary controls. The tip; ensure implementation is done correctly through formal agreements, such as contracts. This increases the likelihood that both parties know what is needed and that there is some reference if there are any hiccups. This brings us to our last and probably most important tip, communication.
Communication
The success or failure of most cybersecurity frameworks, projects, or initiatives mostly comes down to communication. The wider cybersecurity community often stresses how important it is to communicate information to each other, whether it be new developments in cyber defence tactics or new threats (the early the better in the latter case). It can help reduce the fallout of large-scale cyberattacks, foster new innovations in cyberdefense, and, most importantly, build a sense of community.
When assessing the cyber risk of third-parties what you are doing is building relations with them. In most cases, both of you are there to grow the organization and supply the best service or product to the customer. At the same time, there is a requirement of both parties to ensure that appropriate measures have been taken to protect the information ecosystem.
Use this as an opportunity to grow a healthy relationship together; this way, you can also develop secure cybersecurity practices together, and become an example for this community.
Closing Remarks
The NIST third-party risk assessment framework is one of many special publications in the NIST 800 series. Keeping up to date on all NIST frameworks, and the plethora of other cybersecurity frameworks, should not be the job of your organization.
Your organization should do what it does best, offer great products and services to your customers, and leave cybersecurity to the specialist.
With some of the tips given in this article on assessing vendors, cyber risk should be that much more comfortable. For all the rest, leave it to us!
Get in contact with our cybersecurity specialist today.

