
Running a business is no easy task. Knowing whether you’re SOC 2 compliant or not is yet another thing on your already full plate of expense reports, hiring, marketing, and so much more. Using the following information will help clear any confusion so you can focus on the things you love about running your business.

What is SOC 2
Service Organizational Control (SOC) 2 reports are designed to ensure that if you are a service provider who handles customer data, it will be transmitted, stored, maintained, processed, and disposed of in a way that is strictly confidential. Introduced by the American Institute for CPAs (AICPA), SOC 2 compliance indicates to your customers that you will handle their data with the utmost care. And in today’s data-heavy world, avoiding data breaches is crucial to your success as a business owner.
 |
If you are storing your client’s data in the cloud, being SOC 2 certified provides an added level of trust you have with your clients.
A brief note to those who currently running in Amazon Web Services (AWS): this service is currently SOC 2 compliant. You can verify that everything is as it should be by checking in with AWS themselves.
Assess your SOC 2 compliance
Benefits of Being SOC 2 Compliant
- Increased Customer Trust and Organizational Reputation
- Increased Data Protection
- Organizational Vulnerability Awareness
- Increased Security, Availability, Processing Integrity, Confidentiality, and Privacy
SOC 2 Compliance Checklist
Not sure where to begin with guaranteeing your business meets SOC 2 type 2 compliance? Keep reading below.

Provide Framework
The first thing to do is determine what you will test for and why. RSI Security provides a free consultation to help you frame your client needs guaranteeing that you are meeting the necessary requirements and SOC 2 compliance checklists.
This framework needs to be clear and written in a way that external auditors can accurately assess that you meet the requirements for SOC 2 compliance. A proper framework will be a strong foundation for you as you implement—or maintain—the necessary actions for security compliance.
Pick the Right Report
Picking the right report will help you show your clients that you are a reputable service provider. Being SOC 2 compliant requires that you meet standard security criteria outlined by the AICPA, but the other four trust service principles are not mandatory. Nonetheless, examining additional principles can increase your organizational reputation and vulnerability awareness.
Types of SOC 2 Reports
There are two main types of SOC 2 reports.
- SOC 2 Type 1 examines the controls used to address one of all Trust Service Principles. This audit type can affirm that an organization’s controls are designed effectively.
- SOC 2 Type 2 includes the same information, with the addition of testing a service organization’s controls over a period of time.
The AICPA notes, “[Type 2] reports are intended to meet the needs of a broad range of users that need detailed information and assurance about the controls at a service organization relevant to security, availability, and processing integrity of the systems the service organization uses to process users’ data and the confidentiality and privacy of the information processed by these systems.”[1]
Asking the Right Questions
Ask yourself these key questions included in the AICPA guidelines for service organizations.
- “Will the report be used by your customers or stakeholders to gain confidence and place trust in a service organization’s systems?”[2]
- “Do your customers have the need for and ability to understand the details of the processing and controls at a service organization, the tests performed by the service auditor and results of those tests?”[3]
If you answered yes to one or both of these questions, then a SOC 2 type 2 compliance certification is right for you.
If the report will only be used to help with future audits of you or your clients, you may only need to do a SOC 1 report.
Refer to the graphic below to determine which report is best for you:
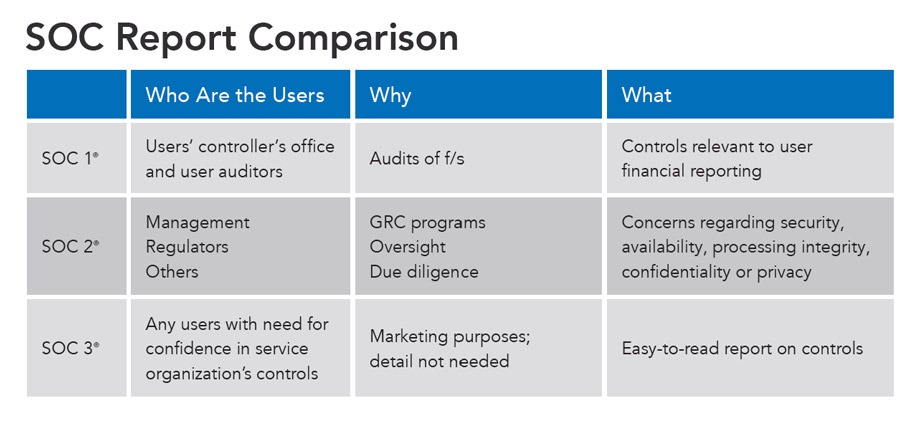
Test for Service Principles
As a business owner, think of your customer’s needs and which service principles would best suit those needs. Below you will find a more detailed outline of the five service principles. Please refer to other requirements regarding SOC 2 compliance for further insight into the trust service principles.

5 Trust Service Principles
SOC compliance checklists focus on five trust service principles that include:
- Security
- Availability
- Processing integrity
- Confidentiality
- Privacy
An external audit by a certified public accountant (CPA) can ensure that your business is meeting the necessary requirements. This article, along with our expert advice, helps prepare you for an external audit. Take a look at the different kinds of SOC reports you may need during your SOC 2 Compliance and Audit journey.
Security
Strong security at both the front and back end are crucial to SOC 2 compliance. It’s important that factors like two-factor authentication or strong passwords secure customer data from the front end.
Establishing application/network firewalls in addition to threat detection on the back end provides protection from breaches that would abuse or misuse a customer’s confidential data. Maintaining up-to-date security programs is critical to prevent against rapidly changing intrusion techniques.
Monitoring unknown/known activity is also important to your security. First, establish a pattern of what known interactive behaviors with your cloud software look like, then you can determine what unknown activity looks like. This practice can help you mitigate potentially dangerous threats before they expose your client’s data to third parties.
Furthermore, SOC 2 compliance with security focuses on you providing accurate reports to the auditors on anomaly reports. Security incidents are bound to happen due to the value of customer data. Make certain that in the event of an incident you have shown the ability to quickly and effectively respond.
Much like establishing a baseline of normal activity on your cloud server can help you detect unknown behavior, keeping audit trails will give you insight into overall context concerning your server. These trails also add a layer of transparency in terms of who has accessed the data in question.
Availability
Availability is determined by the service provider and client in a service-level agreement. According to computer science researcher K.T. Kearney, “Particular aspects of the service – quality, availability, responsibilities – are agreed between the service provider and the service user”[4] Accordingly, the performance level varies from service provider to client and thus should be focused on best meeting the needs of each customer.
Monitoring a customer’s needs as they change and develop with their data services guarantees you will meet SOC 2 compliance checklists and maintain positive service relationships with your customers.
Processing Integrity
Processing integrity determines whether the system is reliable. The AICPA details that processing integrity references when, “system processing is complete, valid, accurate, timely, and authorized to meet the entity’s objectives.”[5]
If you are a business that provides financial services to your clients, processing integrity is highly important to show the client that their transactions are complete, valid, accurate, and timely.
Processing integrity is also an important factor in correcting any errors that may occur. This serves as an internal control to prevent system errors causing other delays or inaccuracies.

Confidentiality
Determining who has access to your client’s data and how that data is disseminated to other parties requires a clear understanding of confidentiality. Your customers will have more peace of mind if you can show that if their data has controlled access by the correct parties and no others, is fully encrypted (should you be working with highly sensitive data), and has the necessary firewalls in place to protect against outside intruders.
Maintaining confidentiality also means that you are careful in having other trust principles in place. Take for example the possibility of a client mistyping a search that leads them to unpublished information on your service; this accidental intrusion into private data—even if seemingly benign—deters client’s from believing their data is held in confidence.
Remember to categorize information that needs to be kept confidential and which is for public use. Keeping audit trails, as mentioned above, establishes transparency and regulates unwarranted access.
Privacy
While you may think you look good in that new speedo you bought on a whim, we are pretty sure the rest of the internet wished you kept those photos private. Nonetheless, the choice should be left to you the consumer which data you wish to keep private or not.
As a service provider, you must afford that same level of privacy to your clients. That embarrassing photo of you in your speedo being spread across the internet is one thing, losing personal contact, medical, or financial data—inadvertently or not—is another.
Throughout the process of collection, storage, use, disclosure, and disposal of information, data that needs to remain private must be a top priority. Research from the Pew Research Center indicates that “93% of adults say that being in control of who can get information about them is important.”[6]
While the majority value this privacy, being able to share confidential information is also important as the Center adds in their findings, “Nine-in-ten (93%) adults say this ability is important to them.”[7] Thus, confidentiality and privacy go hand in hand.
Ensure You Meet Other Compliance Requirements
Streamlining tasks is always within your best interest and fortunately, many of the requirements for SOC 2 Type 2 Compliance are similar to other compliance requirements such as PCI DSS or HIPAA.
Evaluate Your Readiness
It can be stressful as a business owner to feel that you have checked all the boxes to meet service operator standards. By taking advantage of our SOC 2 Type 2 Compliance Checklist, you can easily strategize for any areas that are lacking and mobilize your resources to address problems.
Just like your customer’s needs vary, so do your needs for how to manage and protect those needs. It is important to remember that there is no singular formula for obtaining SOC 2 certification; each is tailored to your specific organization. By scheduling a consultation with RSI Security experts, you can be confident that you will receive the help you need to achieve or maintain SOC 2 compliance.
If you still have questions or concerns, we are here to help! We have a dedicated team of experts who can answer your questions and make sure that your clients’ data is protected.

SOC 2 Compliance Checklist
Take another look at the following steps to help you know that you are ready to be audited and certified:
- Provide a framework
- Pick the right report
- Test for service principles
- Ensure you meet other compliance requirements
- Evaluate your readiness
- Get an RSI Security consultation
It is important to note that there is a variable cost to become SOC 2 certified. The cost of the audit depends on a number of factors which include: your company’s inherent risks, the size of your organization, how long you have been operating with your system, and the number of trust services you decide to test.
Even still, it can be of great benefit to your company to be certified. As mentioned above, increased customer trust and organization reputation are just two of the many benefits. Your current customers and future customers look for that certification to know their important data is kept safe. We can discuss with you what to expect and any pros and cons to becoming certified.
Your customers would be interested to know that the experts at AICPA have been conducting audits and ensuring best practices since their foundation as an organization in 1887. A SOC 2 audit done by a certified accountant can play an important role in these key areas:
- Oversight of the organization
- Vendor management programs
- Internal corporate governance and risk management processes
- Regulatory oversight[8]
This SOC 2 Compliance Checklist is designed to help you prepare for certification and guarantee that you, as a service provider, are meeting technical and ethical standards. Your success is in securing yours, and there is no better success than trust and confidence with your clients.
[2] ibid
[3] ibid
[4] Kearney, K.T.; Torelli, F. (2011). “The SLA Model”. In Wieder, P.; Butler, J.M.; Theilmann, W.; Yahyapour, R. (eds.). Service Level Agreements for Cloud Computing. Springer Science+Business Media, LLC. pp. 43–68.
[5] https://www.aicpa.org/interestareas/frc/assuranceadvisoryservices/trustdataintegritytaskforce.html
[6] https://www.pewinternet.org/2015/05/20/americans-attitudes-about-privacy-security-and-surveillance/
[7] ibid