To the cyber-criminal, the world is a list of digital targets. There are two primary methods for selecting those targets. Sometimes the adversaries cast a very large automated digital net, looking for easily exploitable weaknesses wherever they exist. When the system reports one, they decide if the target is worth their time and either pursue it or move on to the next.
The other is a far more dangerous method, in which the target is pre-selected because it is considered high-value. When hackers decided to go after Target Stores in 2013 the attack was complex, methodical, and persistent; eventually compromising over 40 million people’s card data and costing the company over $300 million.
JP Morgan Chase suffered a breach in 2014 in which they reportedly compromised the financial and personal information of more than 76 million households and 7 million small businesses. The total cost of that incident is estimated to reach $1 billion!
According to the IBM X-Force Threat Intelligence Index of 2019, Finance and Insurance was the most frequently targeted industry in 2018 with 19% of the tracked attacks.
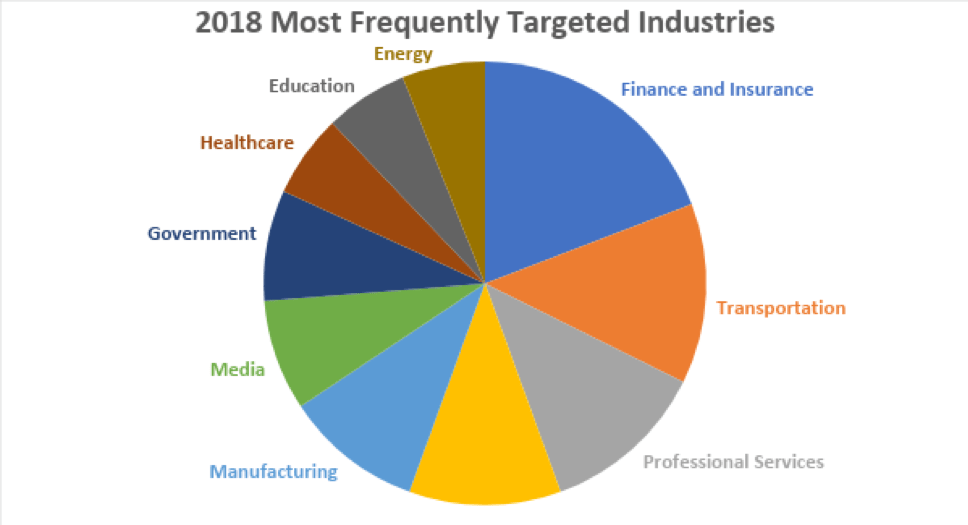
With statistics like these, improving the cybersecurity in financial institutions is an absolute necessity.
Regulatory Standards
There is a variety of different laws, agencies, and Information Security Standards that apply to the financial industry. Many of them are government standards but the payment card industry created, runs, and regulates its own program. Here are the major programs. Adherence to or compliance with any or all of them is company specific, but if you are a financial institution of any kind, you very likely fall under at least one of these program’s requirements.
FINRA – The Financial Industry Regulatory Authority
A not-for-profit organization authorized by Congress to protect America’s investors by making sure the broker-dealer industry operates fairly and honestly. FINRA operates with oversight from the SEC (Securities Exchange Commission)
Assess your cybersecurity
SOX – The Sarbanes Oxley Act
An Act to protect investors by improving the accuracy and reliability of corporate disclosures
made pursuant to the securities laws, and for other purposes. It was Congress’ response to the Enron, Tyco, and WorldCom scandals.
GLBA – The Gramm-Leach-Bliley Act
An Act that requires financial institutions – companies that offer consumers financial products or services like loans, financial or investment advice, or insurance – to explain their information-sharing practices to their customers and to safeguard sensitive data.

PCI DSS – The Payment Card Industry Data Security Standards
Published by a group assembled by the major card brands called the Payment Card Industry Security Standards Council (PCI SSC). It sets the requirements for any entity that stores, processes, or transmits cardholder data.
FFIEC – The Federal Financial Institutions Examination Council
The Council is a formal interagency body empowered to prescribe uniform principles, standards, and report forms for the federal examination of financial institutions by a variety of federal agencies including the FDIC. It is responsible for developing uniform reporting systems for federally supervised financial institutions, their holding companies, and the nonfinancial institution subsidiaries of those institutions and holding companies.
Also Read : Overview of Compliance Offerings for the Financial Sector
Compliance is not enough
Compliance with regulatory standards is important, but it is not enough. I talk about this often in my articles. A satisfactory assessment means that everything appears to be done right and is in compliance at that moment. It is merely a snapshot of your operating environment.
Too often, an upcoming assessment causes a flurry of work to get done in preparation. Policies are reviewed and updated, settings are checked, and people are forced to jump through hoops to meet training requirements before the inspector arrives. Even worse, in the middle of an assessment when it is discovered that some item wasn’t handled that could cause a negative assessment, everybody rushes to get it done in order to pass the assessment. The problem with this is the mindset.
In these types of corporate cultures, security is “the ticket that needs to get punched” to pass the assessment. This attitude from management leaves employees believing that once the assessment is over, we can go back to ‘business-as-usual’. Keeping the network secure wasn’t the point of all that work, passing the assessment was! Once that is done everyone can relax again. No one believes security is important because, in their perception, even Management doesn’t think it’s important based on their behavior.
On the other hand, at some companies, there are periodic security reviews, regular training, reminders at departmental meetings, exercises of their Incident Response Plan, posters touting the virtues of data security on the wall, and occasional spot-checks to ensure everyone is paying attention. They are forward-leaning and aware of all the latest developments on the security front, moving quickly to mitigate newly discovered vulnerabilities. Management often shows an interest in the company’s security status. These types of companies have a culture that encourages continuous security awareness and is thus, always ‘inspection ready’. More importantly, they are always ready for a cyber-attack.

The Basics
The CIA triangle
All information security comes from the concept of protecting the information’s Confidentiality, Integrity, and Availability.
Confidentiality – Only those allowed to may access the information.
Integrity – The information does not get changed either purposely or accidentally
Availability – The information can be accessed when needed, even in the event of DDoS or natural disaster.
Physical Security
Network equipment is locked in a separate room and access is controlled. The office doors and windows are all locked when no one is there. Sensitive areas are not accessible by unauthorized personnel. Fire protection is sufficient.
Network perimeter
An adequate hardware firewall that does a stateful inspection and is properly configured is the first piece of your network the internet must go through.
User management
All users are assigned unique IDs and only given access to information required to do their job. Elevated privileges are kept to a minimum number of users.
Patch management
Administrators keep abreast of new vulnerabilities on their networks. Software patching is tested and completed in a timely manner.
Anti-virus
A reputable A/V is installed, automatically updated, and settings are not able to be changed by users.
Personnel training
All personnel are trained on basic security measures the company observes. Personnel that deal with sensitive information regularly receive training specific to the data environment.
Beyond the basics
Your Information Security Policy (ISP)
Network security is about more than having the right IT gear with the right settings. Security should be looked at more holistically taking people, processes, and technology into account. Generally, the best place to start is with your Information Security Policy (ISP). This document should have detailed guidelines to all aspects of your program including Risk Assessments, Access and Authorization, Physical security, Incident Response Plan, Business Continuity Plan, and much more.
Defense in depth
This is the concept that vital information cannot be improperly accessed by beating 1 security measure. With defense in depth, multiple measures must be beaten. For instance, an attacker might have to beat a firewall, know a user name, crack a password, avoid the honeypot, and install malware that isn’t detected by the Anti-virus (A/V) all while not alerting the Intrusion Detection System (IDS) to reach sensitive portions of the network, and then beat the encryption and other measures to access the critical portions of the network.
Physical defense in depth may have roving security, cameras, complex locks, motion sensors, and alarms all before you can even access the server room.
Multiple barriers take time to overcome. The more time it takes to complete an attack, the more opportunities there will be to make a mistake, and the higher the chances of getting caught. Multiple barriers require multiple areas of expertise to overcome, making the attack more difficult and time-consuming.
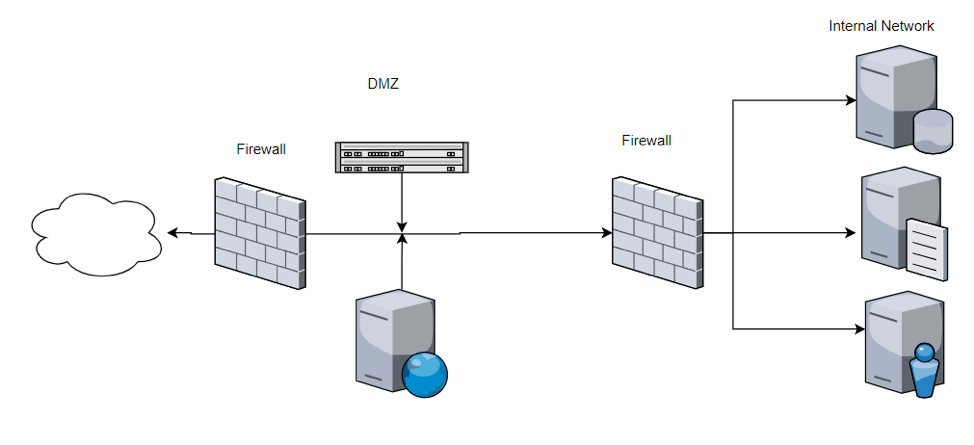
DMZ or Network segmentation
A form of defense in depth, segmenting your network can keep your sensitive information safe while allowing relative freedom for other portions of the network. A DMZ puts a web server behind a firewall that is accessible from the internet. A second firewall behind the web server protects the internal network.
Encryption
Encryption and key management can get complicated quickly, but there is no better way to protect sensitive data than with strong encryption. It is the final layer of your defense. If all other measures have been beaten, the adversary still must figure out how to decrypt the data. Encryption is so powerful that if you have a data breach, in many cases if you can prove the data was properly encrypted and the keys were not compromised, you may not be required to notify clients about the breach.
Options for database encryption include column level, tablespace or dataspace level, and file level. Another option for data at rest is whole disk encryption which is a particularly good choice for mobile platforms such as laptops and tablets.
Sensitive data should be encrypted in motion as well. HTTPS, TLS, and FTPS are some examples of encryption for data in transit.
Security Incident Event Management (SIEM)
Reviewing your logs is an essential part of a good security program. Depending on the size of your network, that task may be relatively easy or completely daunting. Naturally, there are automated solutions available that comb through all the incidents and events, notifying administrators when something looks suspicious. With each vendor having its own take on how SIEM should be handled including whether you need a software or hardware solution, significant research will be required before deciding what is right for you.
The nice thing about many SIEM solutions is that it can make compliance with many regulatory requirements much easier to stay on top of.
Some examples of top SIEM providers are Splunk, Alienvault, and IBM Security QRadar.
Logging and auditing
Propper logging is not only required by many of the security standards, it is also paramount to the forensics side of a data breach. The last phase of an online attack is called “Covering your tracks”. It involves attempting to remove all evidence of the intrusion. Common tactics include changing the server time and deleting logs. If the right events aren’t being logged, or logs aren’t saved and backed up securely, you may have to assume all servers were compromised instead of being able to forensically determine what the adversary did while your network was compromised. Keep in mind that log storage may be sizeable. PCI requires 12 months of logs be retained with 3 months immediately available!
In addition, if time isn’t being kept properly on your network, it may be impossible to determine what events happened when. Good time keeping involves one server getting time from a reputable outside source such as pool.ntp.org, with all other components in the network getting time from the one central server on the network.

Backups
Even if you do everything else right, disaster may strike. Server room fire, electrical problems, or any number of massive failures may take out your entire server bank. There is no substitute for good backups. Backups should be done often and stored offsite. The options vary by expense, and the amount of time it will take to restore following a disaster. Restoration should be practiced periodically to reduce time and errors in the event there is a real need to restore.
In Summary
Financial institutions are considered high-value targets by the adversary. Keeping a close eye on your network and constantly looking for weaknesses to improve is a must.
If you are a financial institution in need of assistance improving your security, don’t hesitate to reach out for expert advice. Contact RSI Security today .
Stay Secure!
