Banking and financial systems often go unnoticed by the general public despite the fact that they support daily tasks. The US government even classifies financial systems under critical infrastructure. With both America and European countries relying heavily on technology, they have attempted to keep pace with new banking cybersecurity regulations. Ever wondered about the differences in cybersecurity regulations of banking in Europe vs. the US? Read on to find out now.
Cybersecurity for Banks
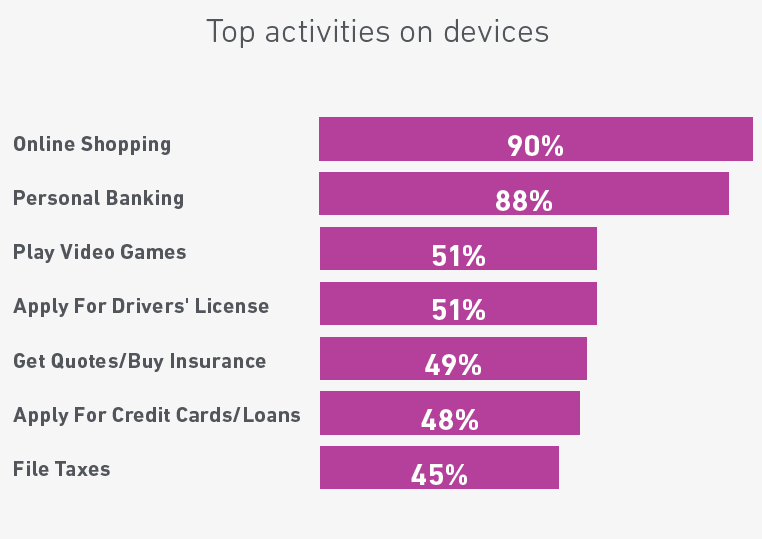
Graphic source: Experian Blog
The American Bankers Association notes that the increase in portable device usage for banking increases overall vulnerability and the risk of fraud. A 2018 Experion study reported that 88 percent of individuals conduct some form of personal banking online. Consequently, keeping abreast of new cyber laws remains fundamental to running a banking business.
The concept of globalization means banking now transcends borders, and, as a result, both the EU and the US face similar banking cybersecurity threats. In many ways, the EU as a whole parallels the US in cybersecurity regulations – EU member states are like US states. Just as every EU member may have specific regulations, the EU governing body as a whole also issues cybersecurity regulations. Likewise, the US government issues regulations in addition to state guidelines.
Assess your cybersecurity
Features like two-factor authentication and automatic transaction alerts, implemented in both the US and EU, are just some of the new ways companies are trying to balance ease of access with security. However, security measures can be double-sided. As companies require more complex passwords, consumers forget them and leave an opening for fraudsters to simulate a password reset process. That’s where new regulations come into play.
US Banking Regulations
US regulations cover anti-laundering, fraud, data storage, and transactions. Unlike individual European countries, the US has a more fragmented system for financial cybersecurity regulations in that both states and the federal government have jurisdiction (although as noted above, the member state concept is similar). The regulations below highlight some of the key/broader regulations currently in place; however, there are many more specific laws active across the country.
Dodd-Frank Repeal
In 2018, the Mobile Act, part of the new Economic Growth, Regulatory Relief, and Consumer Protection Act, went into effect. This new act overrides the previous limitations imposed by the Dodd-Frank law. The Mobile Act enables banks to onboard customers via an easier online verification process. For example, potential clients can scan a form of identification (e.g., passport) and use an e-signature for confirmation. The multi-step process uses Consent-Based Social Security Number Verification (CBSV).
Gramm-Leach-Bliley Act (GLBA)
The government passed this act in 1999 as the Financial Modernization Act. Under the law, companies must inform consumers about data protection measures and how/if their data is shared. Additionally, GLBA compliant companies must give consumers the option to opt out of third-party data sharing. Protected account activity is also tracked to ensure that fraudulent activity is caught as soon as possible. Companies required to comply with the GLBA include check-cashing businesses, payday lenders, mortgage brokers, nonbank lenders, personal property or real estate appraisers, professional tax preparers, and courier services. The overall takeaway is that confidentiality and transparency rules, as outlined in the GLBA regulations, will bolster consumer loyalty and trust for compliant entities. For more information about how to comply, click here.
NIST Cybersecurity Framework
The National Institute of Standards and Technology (NIST) created a general threat management framework for all industries. The framework can be tailored to each business needs. However, NIST specifically highlighted regulations for the healthcare, financial, and retail industries. Financial institutions report to the Financial Industry Regulatory Authority (FINRA). NIST’s guidelines go hand in hand with the Financial Industry Regulatory Authority’s (FINRA) requirements of processes and controls necessary to manage and mitigate cyber risks. Topics covered include authentication controls, internal risk assessments, and vulnerability disclosures (e.g., New York’s 23 NYCRR 500 cybersecurity regulation requires that cybersecurity breaches be disclosed within 72 hours).
European Requirements
Like the US regulations listed above, the following EU guidelines are not comprehensive. Rather, they highlight the key changes EU governing bodies have made in regards to cybersecurity policies. While applicable for all EU industries, the regulations do have certain implications for the banking/financial industries.
Payment Services Directive 2 (PSD2)
the EU implemented PSD2 (also called the Revised Directive on Payment Services) in 2015. PSD2 requires financial institutions to increase authentication protections, conduct risk assessments, link authentication codes with amounts and payees, and adopt mobile application security procedures. “Increased” authentication protection means using two-factor authentication, biometrics, and tokens (i.e., one-time password). Regarding mobile app security, PSD2 specifies that financial institutions must actively employ counter cloning measures (i.e., replication protection).
Security of Network and Information Systems (NIS Directive)
The NIS Directive was adopted in 2016 and serves as a broad cybersecurity regulation. It requires EU members to establish cooperation groups (to facilitate clear communication in the event of a cyber attack affecting more than one member state), encourage preparedness (e.g., create incident response teams), and foster a culture of security across critical infrastructure (e.g., healthcare, banking). Similar to the US NIST cybersecurity framework, the EU Commission provides a NIS Toolkit.
PSD2 Regulatory Technical Standards (RTS)
Although the initial PSD2 outlined certain goals for ensuring safe banking transactions across all EU member countries, it lacked the specificity necessary for a comprehensive security checklist. Consequently, in 2017, the EU Commission released the Delegated Regulation on Regulatory Technical Standards (RTS) which elaborated on the PSD2’s goals. The RTS lists specific protocols necessary for securing communication and customer data. In particular, companies must identify KPIs (Key Performance Indicators) and service level targets. Furthermore, RTS requires the use of eIDAS (electronic IDentification, Authentication and trust Services).
General Data Protection Regulation (GDPR)
The GDPR went into effect in May 2018 for all EU members. The GDPR focuses on who controls what data. In large part, the regulation gives consumers more control over how and which companies use their data. Notably, the GDPR applies to any company using EU citizen data, even if those companies are non-EU based entities. According to Skadden, the GDPR applies to controllers or processors with an establishment in the EU that process personal data in the context of the activities of that establishment, whether the processing happens in the EU or not (the establishment criterion).
FinTech Action Plan
FinTech is the new technology used by the financial industry and includes products and processes. In 2018, the European Commission’ launched a new plan to encourage the use of FinTech and establish safety practices. on utilizing new security technology (e.g., Blockchain) to be both more competitive and more secure.
Overlapping Regulations
Since money influences every nation, it is understandable that financial institutions also tend to operate in more than one country. Consequently, certain banking standards overlap between Europe and the US.
PCI DSS
The Payment Card Industry Security Standards Council (PCI SSC) oversees the administration of the Payment Card Industry Data Security Standard ( PCI DSS). The standards address card issues and ensure safe storage, processing, and transmission of data. The first PCI DSS document was released in 2004 prior to the formation of the council in 2006. The council updates the standards when new exploits surface and the current version is 3.2. Although this standard started in the US, it has global implications as the card providers (Visa, Mastercard) operate in many different countries. To learn more about the standards, check out the PCI DSS checklist.
US vs EU Non-Compliance Consequences
As noted above, European GDPR laws parallel many of the US federal and state laws. Likewise, the penalties of noncompliance are equivalent in many ways. Just as each US state can penalize a company for noncompliance, each member state of the EU possesses the power to administer fines. Additionally, both the US and EU divide penalties into levels.
The GDPR has a lower and upper level. Failure to comply with the GDPR lower level results in fines of up to €10 million or 2% of the worldwide annual revenue. Controllers/processors, certification body, and monitoring body fall under the lower level purview. For upper-level infringements, the fines are up to €20 million, or 4% of the worldwide annual revenue of the prior fiscal year. The upper level encompasses processing, including conditions for consent, data subjects’ rights, transfer of personal data to a recipient in a third country or an international organization, obligations pursuant to Member State law, and non-compliance with an order by a supervisory authority. Under the GDPR, the most significant infringement takes precedent if a company violates more than one regulation.
In the US, GBLA penalties are divided into individual and institutional violations. For institutions, each violation results in a USD 100,000 fine. For individuals in positions of oversight (e.g., directors), fines may be USD 10,000 per violation. In more severe cases, individuals may face up to 5 years in prison.
Each of the other regulations has similar penalty processes that can be found on their respective websites.
Emerging Cyber Risks for Banking
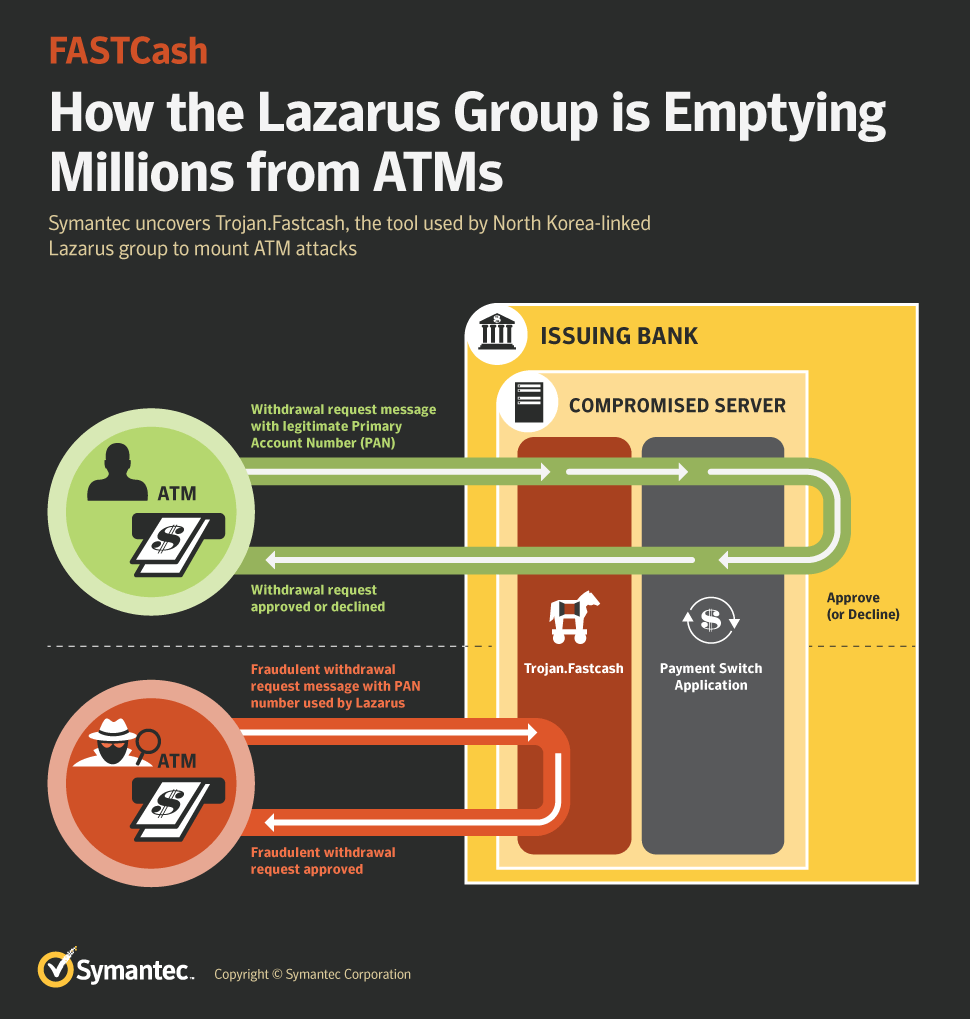
Graphic source: https://www.symantec.com/blogs/threat-intelligence/fastcash-lazarus-atm-malware
For the financial industry, ATMs, banks, mobile banking, fin-tech companies, and cryptocurrency are just a few of the current cyber targets. The younger the industry, like cryptocurrency, the more vulnerable.
In terms of attack types, a new trend focuses on attacking via the supply chain. Two hacking groups, Lazarus and MageCart, implemented this tactic in 2018. Lazarus released the AppleJeus malware targeting the cryptocurrency supply chain, and MageCart infected British Airways’ payment process through Magento. More recently, the FBI claimed North Korea targeted cryptocurrencies in retaliation for US sanctions.
ATM threats continue to develop. In 2018, the majority of ATM attacks occurred due to compromised internal networks. As a result, threat actors gained access to numerous ATMs and implemented ATM malware automation (like Lazarus). As mobile banking grows, more threat actors will shift away from PC attacks.
Mobile Banking Fraud
Since more and more of our daily lives include the use of a cell phone (e.g., creating a Powerpoint or grocery shopping), threat actors have shifted their attention from desktops/laptops to mobile vulnerabilities. In 2018, SecureList reported that the number of Trojans attacking users of mobile devices has more than doubled over the past year.
Subsequently, it’s in a bank’s interest to invest in mobile security. ThreatMatrix reported that it costs 10 cents for mobile transactions versus 4 dollars for the same transaction in a physical bank branch.
Top mobile financial functions include:
- P2P payments
- transaction monitoring
- mobile account opening and Remote Deposit Capture (RDC)
In other words, mobile financial transactions go beyond withdrawals or cashing checks, it includes many other transactions like GrubHub or Uber. Anytime a credit or debit card is involved, mobile “banking” is in play. One of the most common frauds involves tricking users into revealing their login credentials (e.g., sending an email saying the system is updating and you must re-login). Experts suggest improving authentication/identity verification processes and implementing behavioral analysis to combat credential fraud.
EU vs US Mobile Regulations
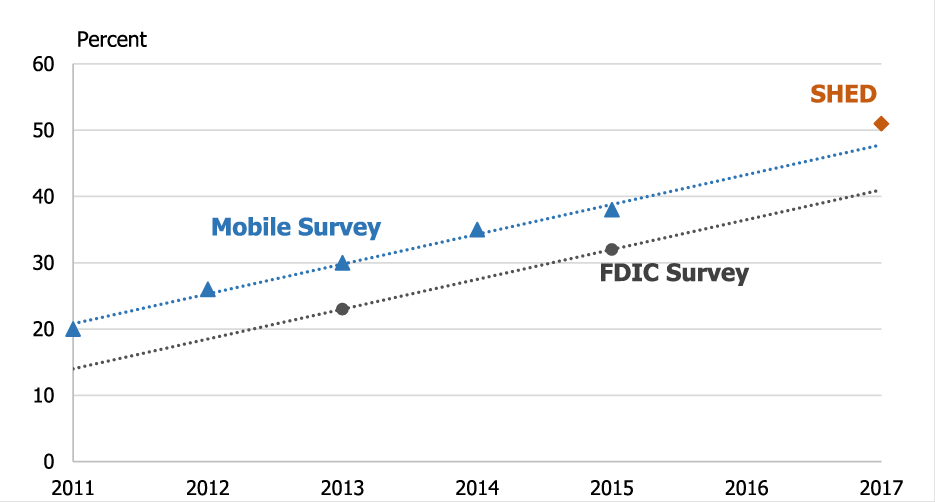 Since mobile banking continues to grow, it’s worth noting the different efforts currently in motion for combatting mobile fraud. The European Payments Council (EPC) is currently working on the Single Euro Payments Area (SEPA) project and a new mobile payments framework. SEPA deals with cross-border fees for credit transfers, ATM withdrawals, direct debits, etc. The underlying goal centers on equal charges for domestic and cross-border activity. The mobile framework is reportedly going to incorporate SEPA concepts and will address both near proximity (e.g., NFC, QR codes) and remote (e.g., mobile commerce, internet) payment security. Although the framework is still in progress, the EPC did release a white paper threat report that includes a section on mobile banking fraud.
Since mobile banking continues to grow, it’s worth noting the different efforts currently in motion for combatting mobile fraud. The European Payments Council (EPC) is currently working on the Single Euro Payments Area (SEPA) project and a new mobile payments framework. SEPA deals with cross-border fees for credit transfers, ATM withdrawals, direct debits, etc. The underlying goal centers on equal charges for domestic and cross-border activity. The mobile framework is reportedly going to incorporate SEPA concepts and will address both near proximity (e.g., NFC, QR codes) and remote (e.g., mobile commerce, internet) payment security. Although the framework is still in progress, the EPC did release a white paper threat report that includes a section on mobile banking fraud.
Compared to the EU, the US began releasing mobile banking regulations/recommendations earlier. In 2011, the FDIC released supervisory guidelines for the mobile banking industry. Notably, the FDIC separates mobile banking from mobile payments; however, the two categories have begun to blur. The publication highlighted the risks associated with the three banking delivery channels: text messaging, mobile-enabled internet browsing, and mobile applications. The text channel is vulnerable as fraudsters may spoof a bank and send consumers fake texts that prompt them to reveal PII. Additionally, SMS messages are not usually encrypted (unlike web-based WhatsApp). The FDIC also noted that web-based banking on small devices makes it harder to identify suspicious indicators, and mobile application banking faces the difficulty of malicious software installations.
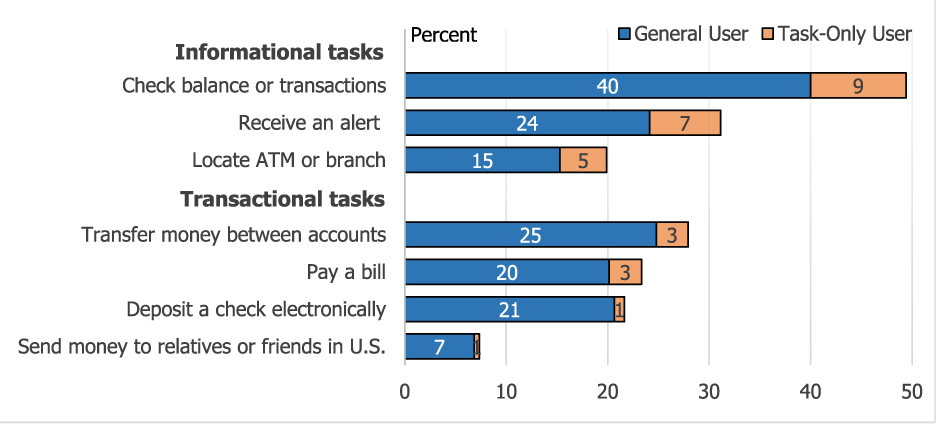
Graph Sources: https://www.federalreserve.gov/econres/notes/feds-notes/mobile-banking-a-closer-look-at-survey-measures-20180327.htm
In 2012, the Federal Deposit Insurance Corporation (FDIC) published Mobile Payments: An Evolving Landscape. Since then, the FDIC continues to produce new findings almost every year (see the 2018 update here). Lastly, the FDIC provides a list of relevant regulations companies should review if they are involved in the mobile/e-banking environment.
- FFIEC IT Examination Handbooks on Development and Acquisition
- Outsourcing Technology Service Providers
- E-Banking
- Information Security
- Interagency Information Security Standards
- Interagency Regulations and Guidelines on Identity Theft Red Flags
- FFIEC Guidance on Risk Management of Remote Deposit Capture
- Guidance on Electronic Financial Services and Consumer Compliance
- Guidance for Managing Third-Party Risk
Need Help?
Online and mobile banking platforms are the future! People want convenience and mobile banking satisfies the quick-service younger generations expect. Consequently, the EU and the US are rolling out new cybersecurity regulations for the industry. If you’re interested in learning more about the EU or US cybersecurity regulations, mobile banking, or financial compliance, contact RSI Security today.
