Be Proactive! While the phrase sounds like a self-help slogan, it’s also the key phrase when it comes to current cybersecurity best practices. Rather than waiting until an attack occurs, more and more companies are turning to ethical hacking and, in particular, penetration testing to secure their cyber environments. Penetration testing enhances risk management plans by revealing preventable cyber-attacks. Learn about the different types of pen testing and how they can secure your business with this comprehensive guide. Read on now!
What Is Penetration Testing?
A penetration test, also known as a pen test, is an intentional attack on hardware or software to determine vulnerabilities that could be exploited by threat actors in the future. Pen tests often have two goals, to establish how thoroughly a system’s integrity can be compromised and how much user or company data can be accessed. Pen tests vary based on the level of intrusion — how deeply ethical hackers can infiltrate systems, apps, or hardware. When conducting a pen test, security teams usually look at injection vulnerabilities, broken authentication, broken authorization, and improper error handling.
Why Is Penetration Testing Important?
Pen testing provides much-needed insight on where cybersecurity weaknesses particular to a company. Not all companies are alike, and while a threat assessment will look for common system weaknesses, a pen test identifies those unique to the particular client. Rather than spending money on damage control after an attack occurs, pen testing can identify coding errors, ensure strong security controls are in place and functioning as expected, and detect new software bugs, all of which highlight the threat vectors that require more attention. Moreover, many regulations now require penetration testing, including HIPAA and PCI DSS.
Positive Technologies published a report in 2018 detailing the pen testing result commonalities among all its corporate clients. The tests covered many sectors including energy, finance, transportation, and IT. The image below highlights the major vulnerabilities pen-testing revealed and notes whether those vulnerabilities fell into the medium, high, or critical threat range. Understanding the common threats offers a baseline for threat assessments and pen tests.

Image source: https://www.ptsecurity.com/ww-en/analytics/corp-vulnerabilities-2019/
Benefits of Penetration Testing
- Catching a security vulnerability prior to a real threat actor exploiting it will save a company time, money, and reputation damage.
- Unlike a real attack, penetration testing can often be conducted without affecting the daily operations of a company.
- Pen tests help establish a baseline in terms of response time, communication chains, and tool functionality.
- Conducting a pen test follows current regulations and achieves industry compliance.
Vulnerability Assessments vs Penetration Testing
While both vulnerability assessments and pen testing offer valuable insights for cybersecurity teams, they are not interchangeable. Rather, they should be used in conjunction with each other.
Vulnerability Assessment
A vulnerability assessment looks at a company’s environment, ranks risks, and takes stock of current security controls. Such assessments are resource centered, looking at what resources face the greatest threats and then allocating security budgets to address the most critical risks.
Pen Tests
Pen testing, on the other hand, is testing-centered. These tests exploit and try to escalate situations to identify the weaknesses of networks, applications, and physical locations. When engineers complete the pen test, they will provide a report identifying the risks to the client. As noted above, pen testing looks for all weaknesses, not just those commonly expected for companies in certain industries.
But What about a Vulnerability Scan?
Another commonly misunderstood concept is a vulnerability scan. These scans can be conducted automatically and search for known vulnerabilities, whereas pen-testing (usually manual) looks for new vulnerabilities. For example, a vulnerability scan may compare available system patches with patches a company actually implemented, but it does not seek out new vulnerabilities. Some well-known scanning tools are Nessus, GFI LANGuard, Rapid7, Retina, Qualys.
Get Penetration Testing services today!
Types of Testing
Broadly speaking, there are two types of pen tests: “white box” and “black box.” White box testing occurs after a vulnerability assessment and after a company discloses system information. Conversely, black box testing leaves the reconnaissance to the pen tester, meaning the extent of the exploitation relies on the tester’s hacking and information gathering skills. Within these two categories, there are five types of pen testing a security expert may conduct.
Network Service Tests
Network pen testing assesses the client’s network infrastructure for access points. This kind of test encompasses both locally run tests, to identify internal gaps, and remote tests, to identify externally accessible vulnerabilities. Typically, a network pen test will look at firewall configuration, IPS deception, DNS attacks, and software modules. Firewall configuration may also encompass stateful analysis testing which monitors active network connections and determines what network packets are allowed through the firewall.
Client-Side Tests
Client-side testing, also referred to as internal testing, looks at local problems, such as when a user accesses an application on his/her device. For example, browsers and packages, like Microsoft, Adobe, or Photoshop, may have application flaws that manifest differently on users’ computers. Client-side attacks will be more focused and targeted than trying to breach a large company’s network perimeter. According to InfoSec Institute, client-side penetration testing should answer the following questions:
- How reliable is the security posture of an organization?
- Are there any vulnerabilities?
- What harm can an attacker do by exploiting these vulnerabilities?
- How can a malicious actor exploit a vulnerability?
- Are the access rights and privileges for employees set correctly?
- How can the detected weak points be closed in an economical and sensible way?
.
Wireless Network Tests
Wireless network tests evaluate the devices and connectivity of wireless networks. These tests will analyze protocol configuration, access points, DoS attack vectors, and signal leakage (the range the network covers outside of the designated coverage zone). Pen testing is particularly beneficial for companies offering wireless services for improved customer satisfaction. For example, we have all been warned about the dangers of logging on to cafe networks. In the past, poorly protected networks used LAN (Local Area Network) which uses Wired Equivalent Privacy (WEP), a now outdated and extremely insecure form of wireless network protection. It’s important to note that a wireless network pen test encompasses more than simply Wi-Fi; it also covers Bluetooth and Bluetooth Low Energy (BLE) devices that interact with the network.
Social Engineering Tests
Social engineering tests target the human network by attempting to “penetrate” through the security training employees should have received. Pen testers may conduct remote or physical tests. A remote test utilizes electronic means, such as an email, to try and deceive an employee into granting access or revealing sensitive information. Phishing campaigns serve as a remote example and are often successful because they use the target’s wants,(such as a free vacation) or needs (like a bank account verification) to trick the target. A physical attack involves interaction with people at a facility. For example, a pen test team may pose as a maintenance team and try to bluff their way inside the building.
Web Application Tests
Web-based applications tests look at browsers and plug-ins related to web applications. Conducting a web app penetration test involves endpoint security on both the consumer side and backend. A pen tester will consider the functionality, usability, security, compatibility, and performance of web apps. Functionality encompasses links, defaults/error messages, cookies (i.e., files that remember user sessions for easier returning to a website), HTML, and CSS. For usability, engineers check navigation and content. For web app security interface and database testing, as well as session access and payment information processes are the commonly testing vectors.
Automated vs Manual Penetration Testing
Companies face two options when determining how to initiate penetration testing. They can use an automated system or they can hire a human team that will manually conduct the pen testing. In most cases, companies choose to implement a combination of automated and manual testing. Regardless, many regulations, including PCI DSS, FISMA, MARS-E, HIPAA, Sarbanes-Oxley, and ISO require some kind of penetration testing to achieve compliance.
Manual – With manual testing, expert engineers collect data, run a vulnerability test, try and exploit the identified vulnerabilities, and finally compose a report with suggestive corrections. If using manual testing, companies can more easily tailor a pen test by either conducting a focused manual test or a comprehensive manual test. Comprehensive tests involve situational details, more scenario-based tests compared to focused tests.
Automated – Automated pen testing is faster and can be run by less knowledgeable people. Additionally, they are often more efficient and can be run automatically. Automated pen tests may be ideal for smaller companies that cannot afford to hire expert engineers. The major weakness of automated testing is that it cannot “think like a hacker” to the extent that an individual can. In other words, a human pen tester possesses the ability to analyze situations better. Additionally, an expert can run multiple tests at once, whereas not all automated systems can multitask.
Using Third Parties
Third parties can be a great resource when it comes to pen testing, but it’s important to understand the pros and cons before signing a contract.
The Pros – In the case of penetration testing, many experts agree that third party penetration testing enhances accountability and provides an unbiased assessment of security control effectiveness. If you don’t have an experienced internal team that is qualified to conduct pen tests, unskilled employees attempting to run such tests may cause downtime and performance issues. Hiring a third party offers a cost-saving option for companies that cannot afford to hire a full-time pen tester.
The Cons – If research is not done on the third party, a company may hire an unqualified team. Consequently, a company endangers its sensitive/proprietary information. As experts so often note, the more people who have access, the more at risk data faces. Thoroughly vetting any potential third party and having clear guidelines in contracts reduces the risk.
Lastly, information could be lost while a pen test is being conducted, so backups, as always, are a good idea.

NIST’S Pen Testing Recommendations
In the National Institute of Standards and Technology’s (NIST) special publication SP 800-115, entitled a Technical Guide to Information Security Testing and Assessment, companies can find a four-step process for penetration testing. This is by no means meant to be an inflexible structure; rather, it is a stepping stone for companies interested in learning about the general pen testing process.
STEP 1: The planning phase gives companies an opportunity to establish goals, determine rules, and finalize legal documentation. Although penetration testing falls under ethical hacking, it is nonetheless hacking, so it’s important to cover all angles legally speaking.
STEP 2: The first half of the discovery phase involves information gathering and system scanning, while the second half focuses on vulnerability analysis. During the information gathering stage, experts identify the IP addresses, ports, system names, and application information (e.g., versions). This first stage may vary if a physical pen test is being conducted. In the second discovery stage, testers will compare/determine if common vulnerabilities exist by referencing an internally compiled list or a third-party database, such as the National Vulnerability Database (NVD).
STEP 3: During the attack phase, pen testers actually try to get into systems, networks, or locations. Gaining access relies on having enough information to penetrate the defenses. The next step involves escalating privileges, basically trying to gain control over systems. Once access and control are achieved, the pen tester will see what information can be compromised by browsing through available databases, files, or communication channels. Lastly, a tester may see what plug-ins or malicious software they can leave behind/install.
STEP 4: The reporting process summarizes the results and offers suggestions for how to strengthen weak networks, systems, applications, etc.
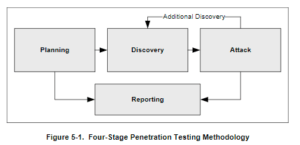
Image Source: NIST SP 800-115
Need Help?
Pen testing provides companies with vital knowledge for strengthening their internal and external security controls. Moreover, such testing highlights a company’s dedication to both consumer privacy and compliance requirements. If you’re interested in learning more about the benefits of a penetration test, contact RSI Security today.
